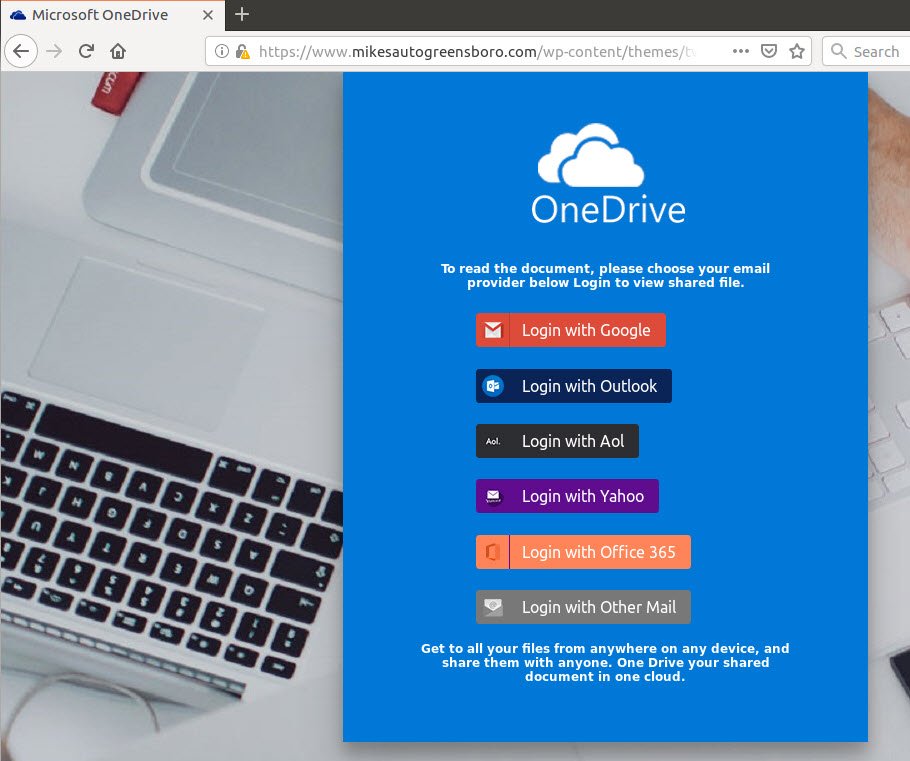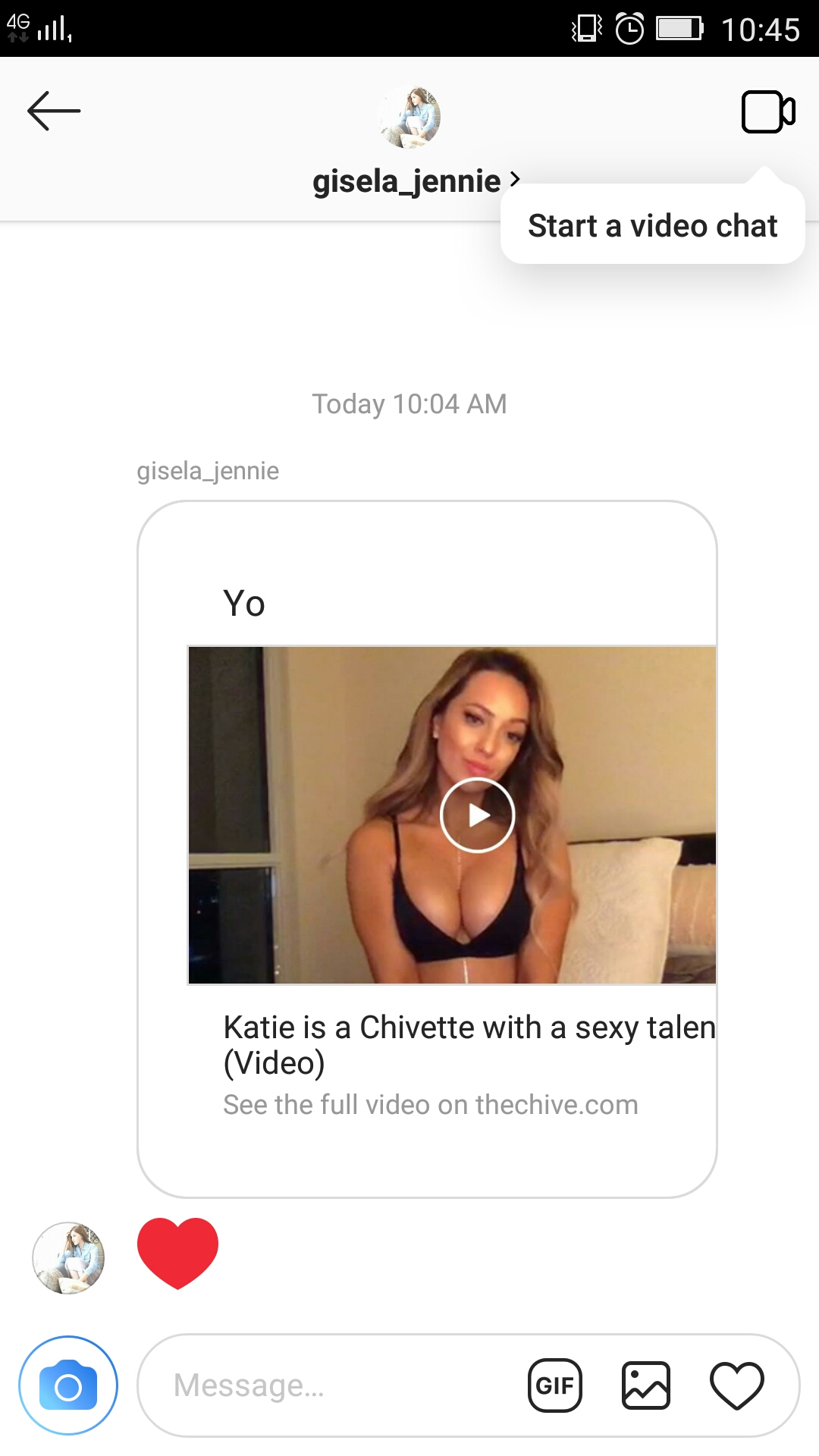
Remove Instagram Video Message Scam — How to Protect Yourself
This article has been created in order to explain to you what is the Instagram Video Message Scam and how you can remove them as well as all potentially unwanted programs delivered through them. The Instagram Video Message Scam is…