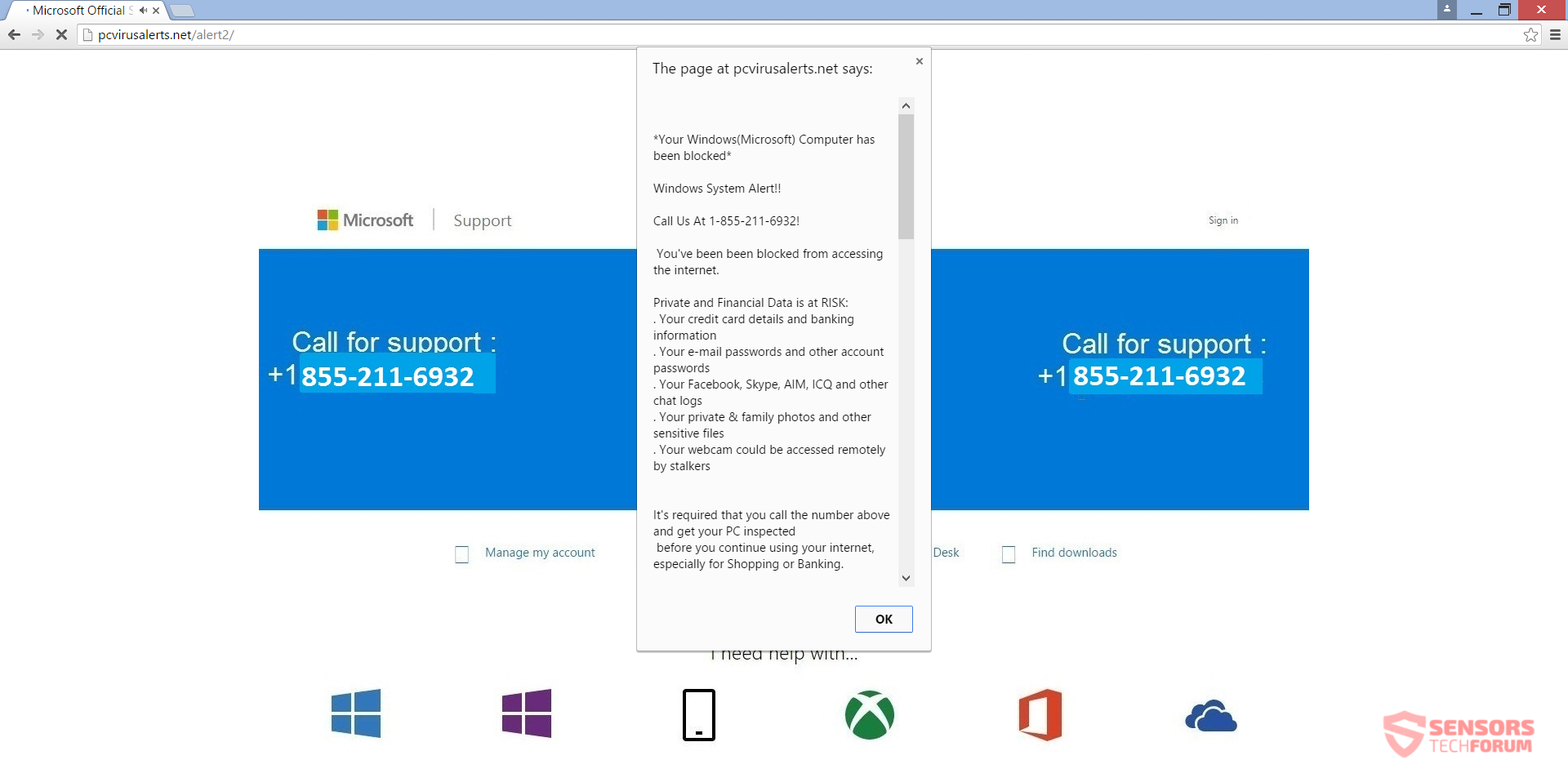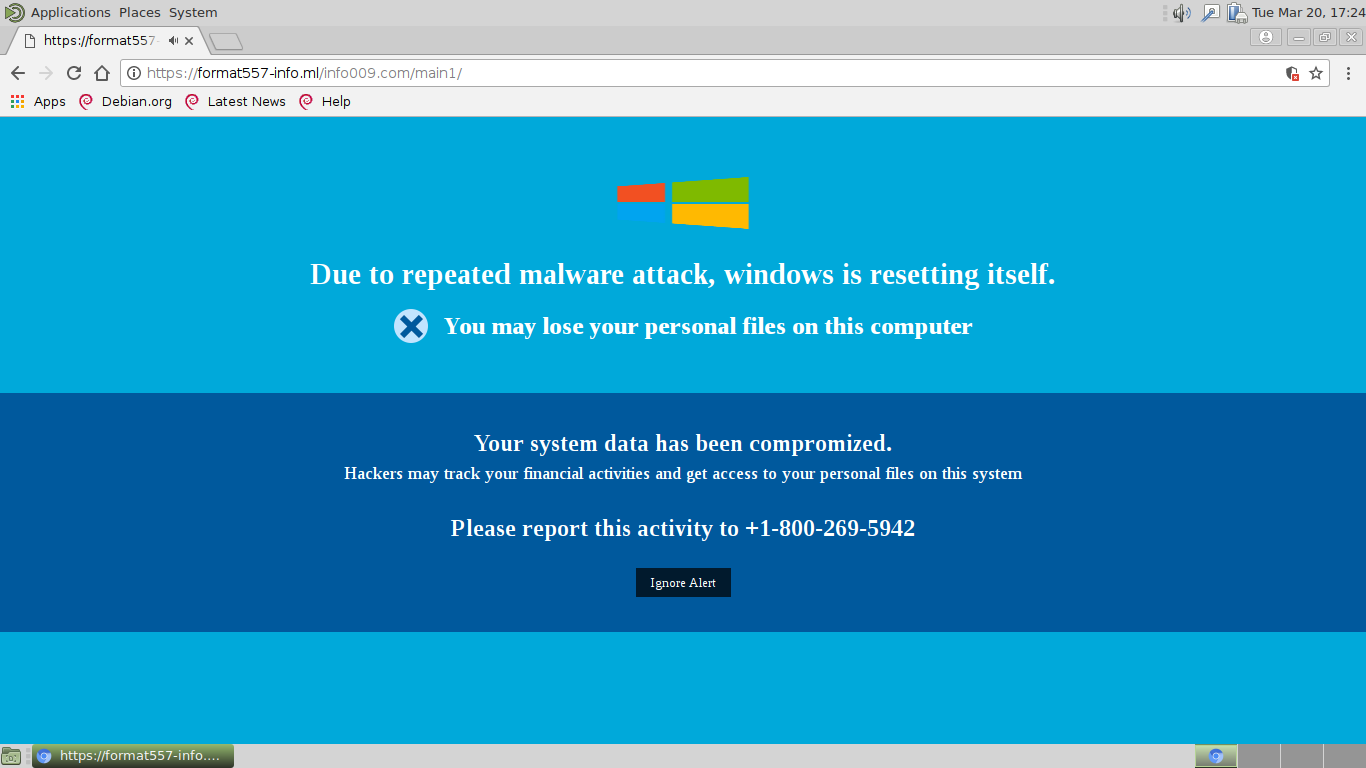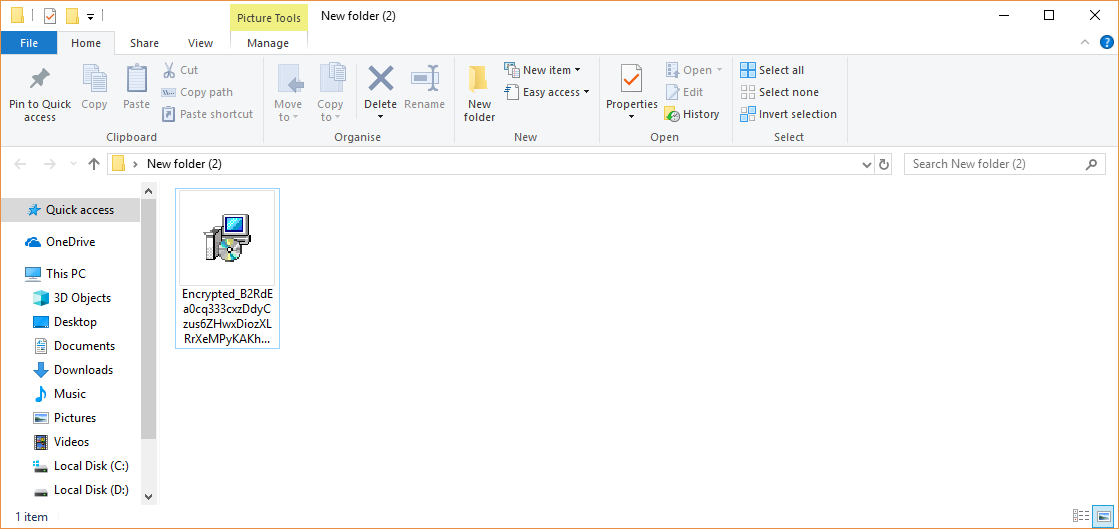
How to Remove Rapid 2.0 Virus — Restore Encrypted Files
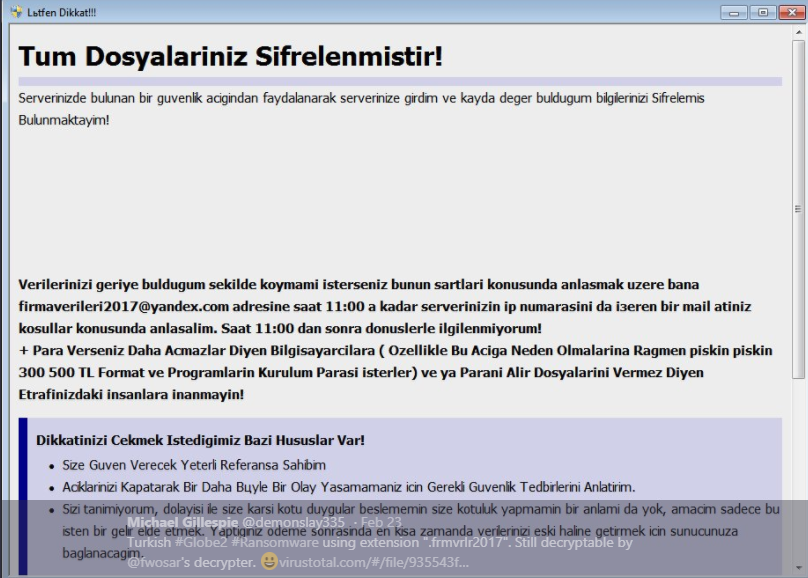
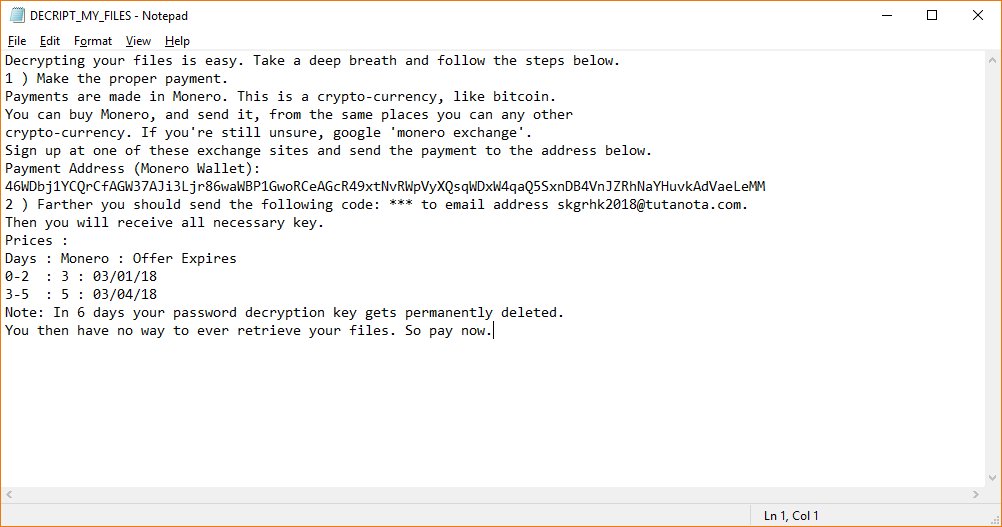
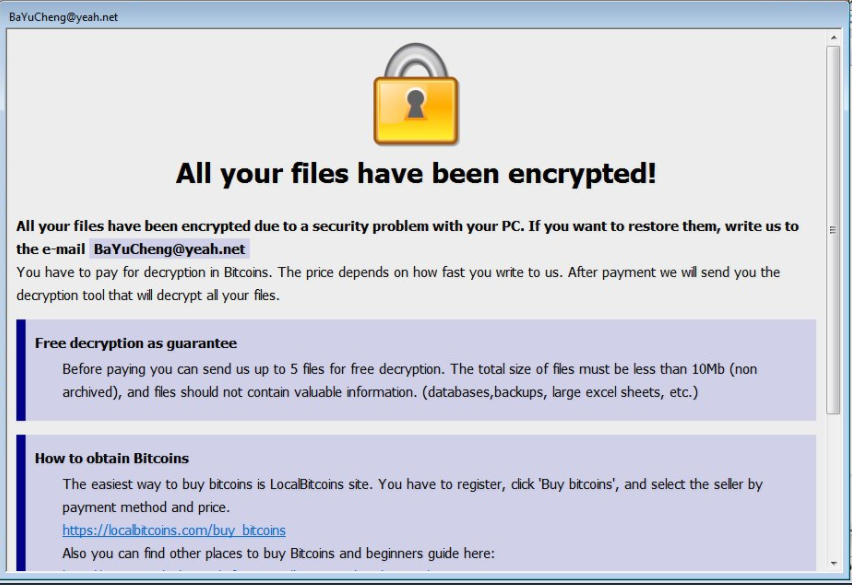
The Rapid 2.0 virus is an advanced ransomware that can reconfigure the system in a malicious way, gather sensitive data about the user and encrypt their personal data. As a result their data will be encrypted with a strong cipher,…