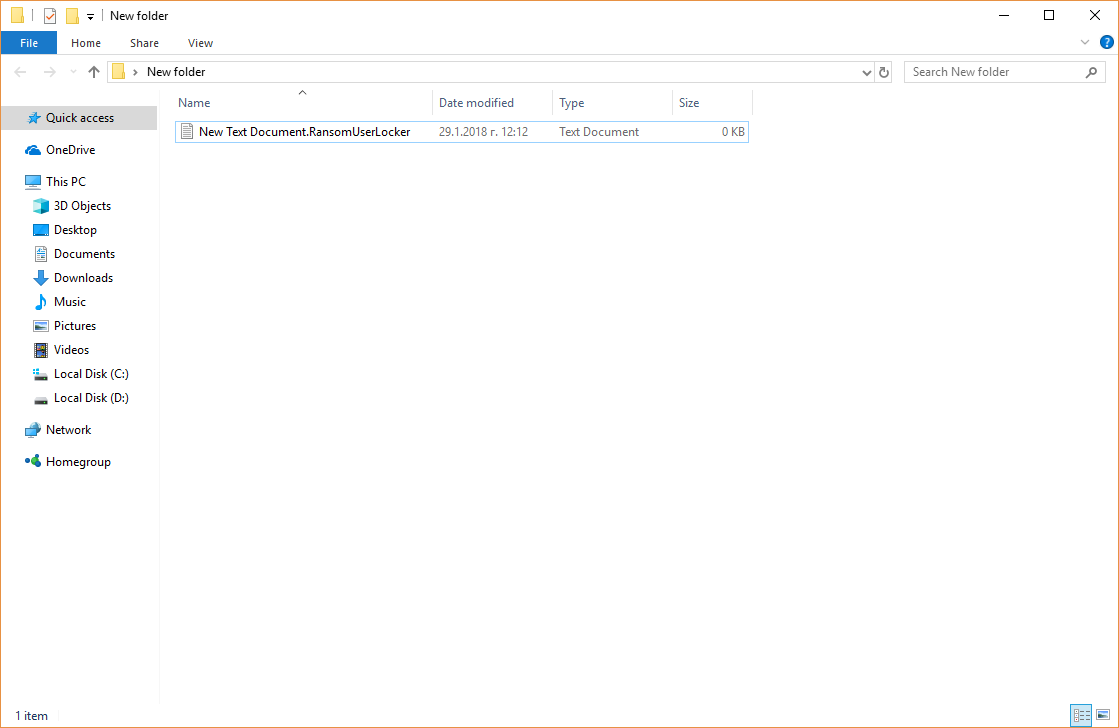
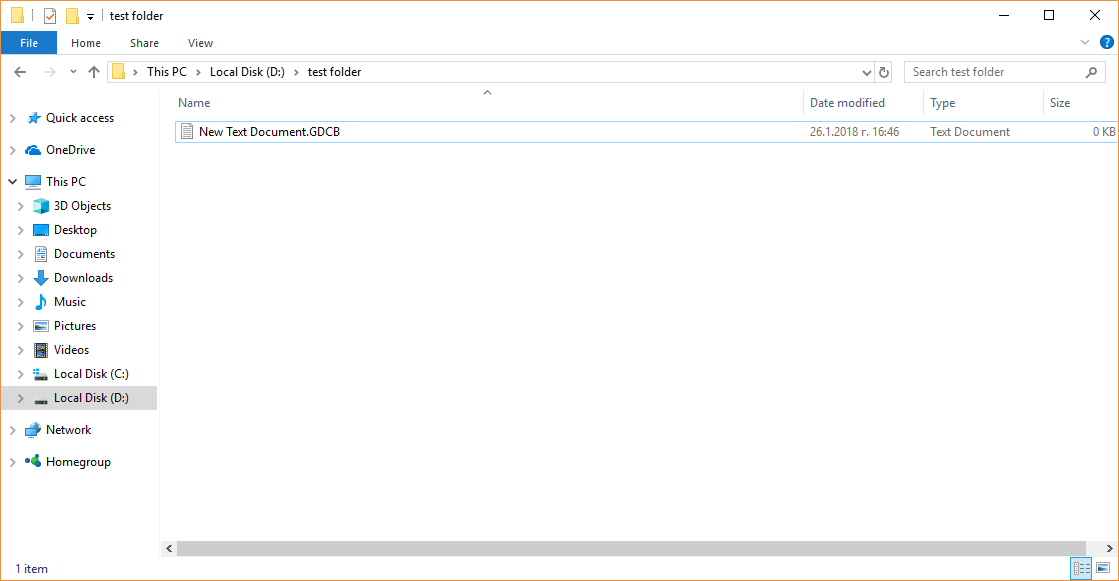
Octoly Marketing Service Leaked Private Data via Amazon Service
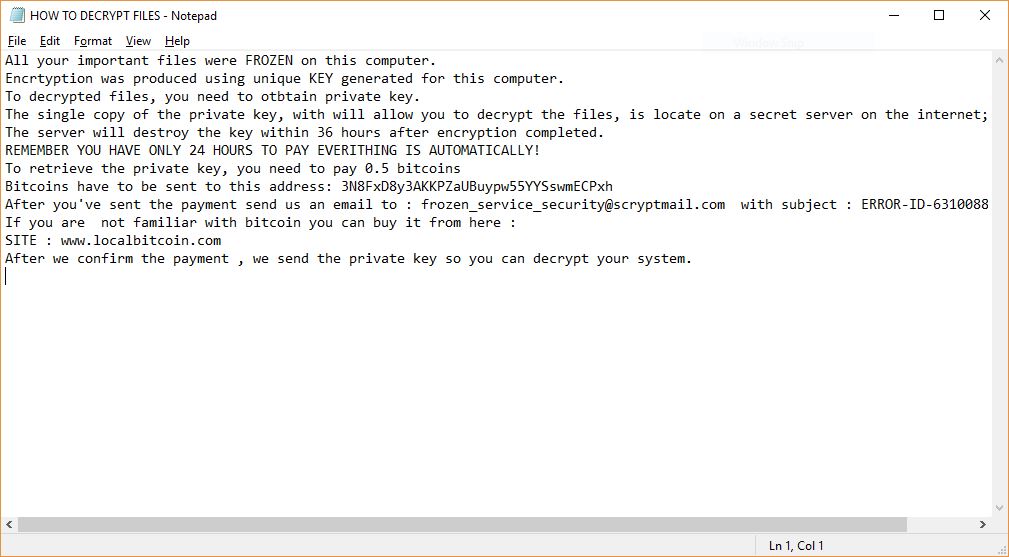
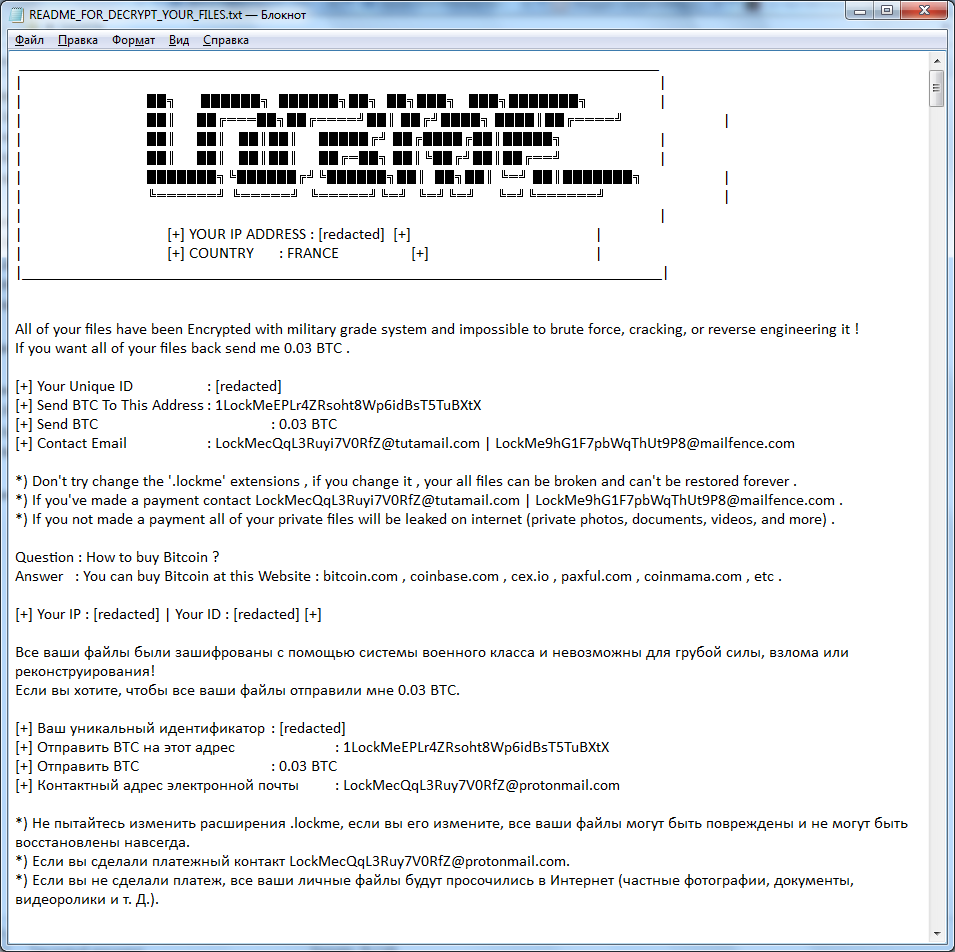
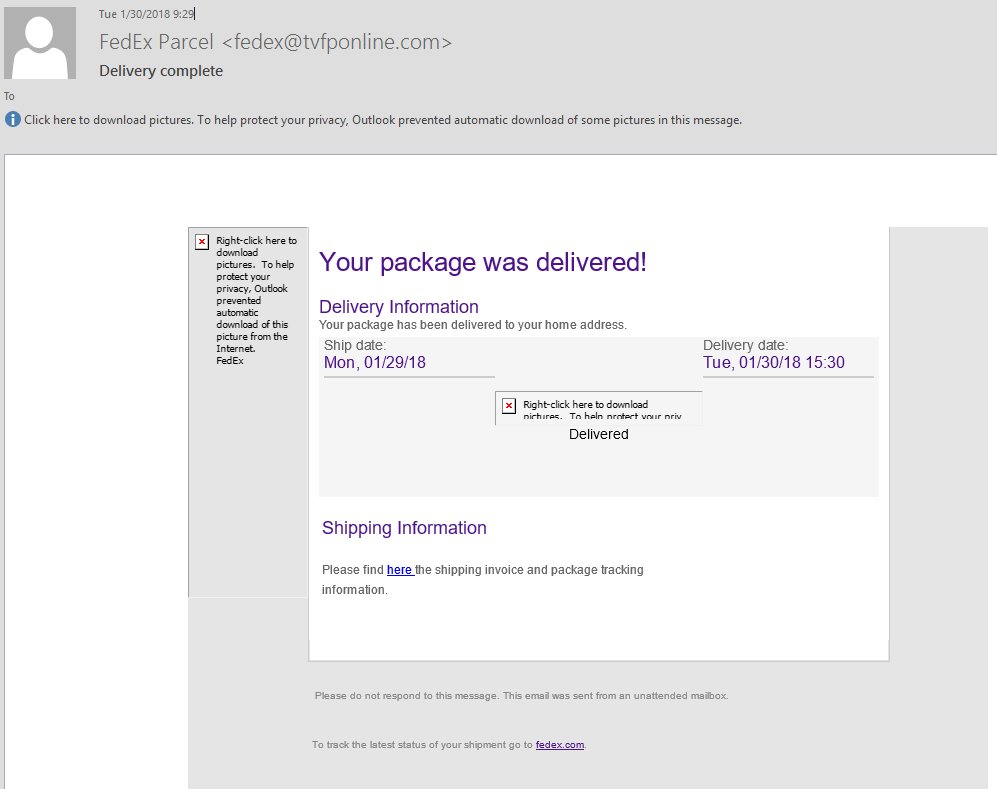
The marketing agency Octoly has erroneously exposed a lot of personal data belonging to their customers. The leak happened due to a misconfiguration in the Amazon S3 Simple Storage Service bucket which hosts the clients data. The security reports indicate…