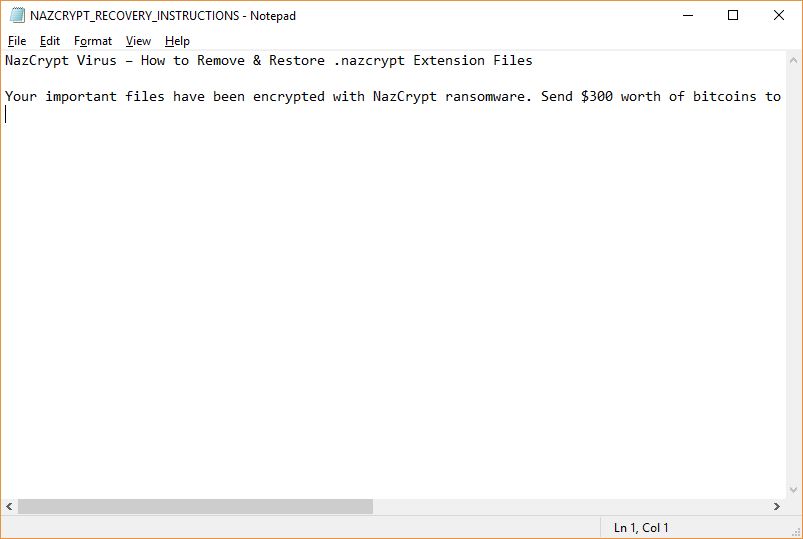
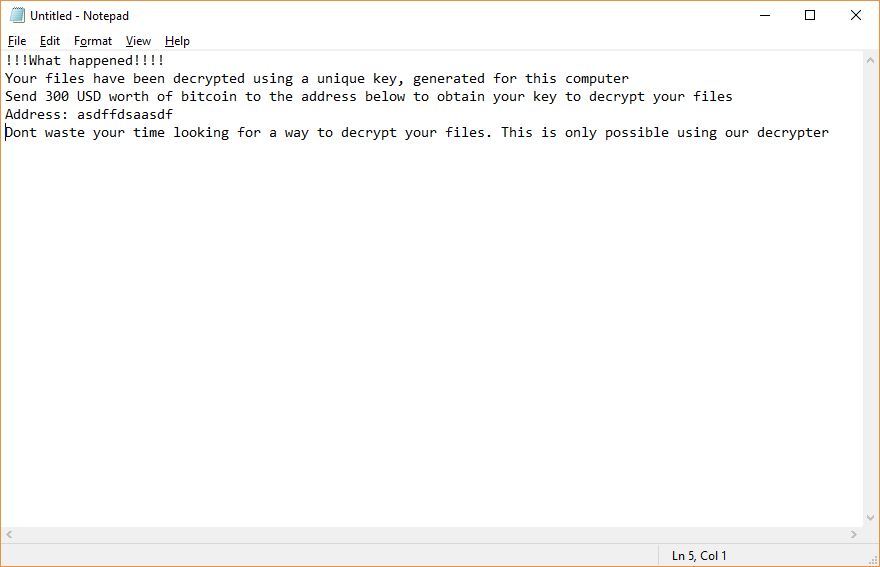
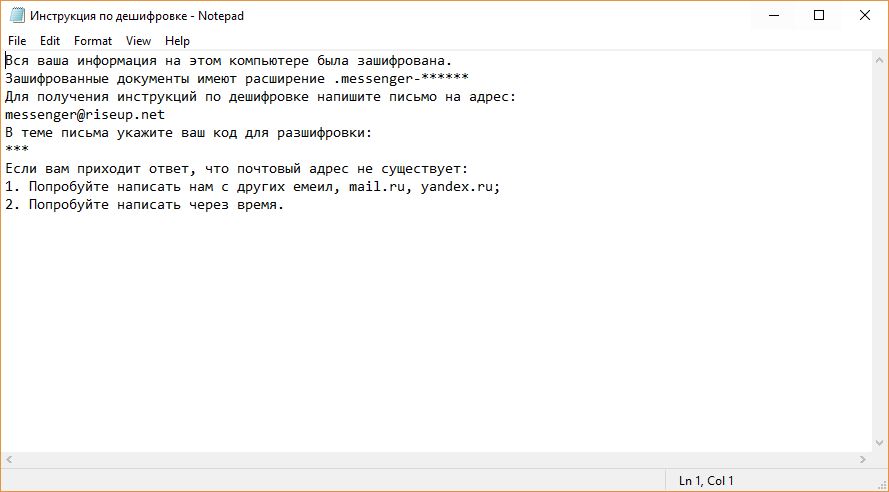
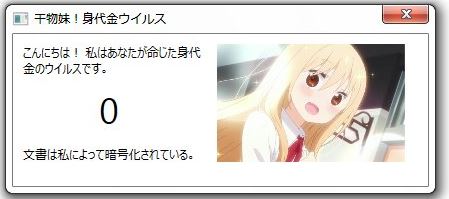
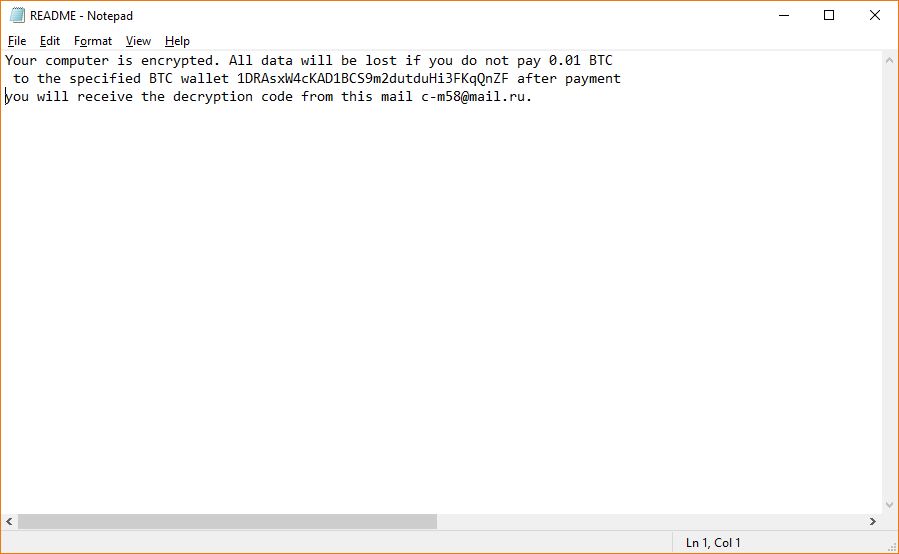
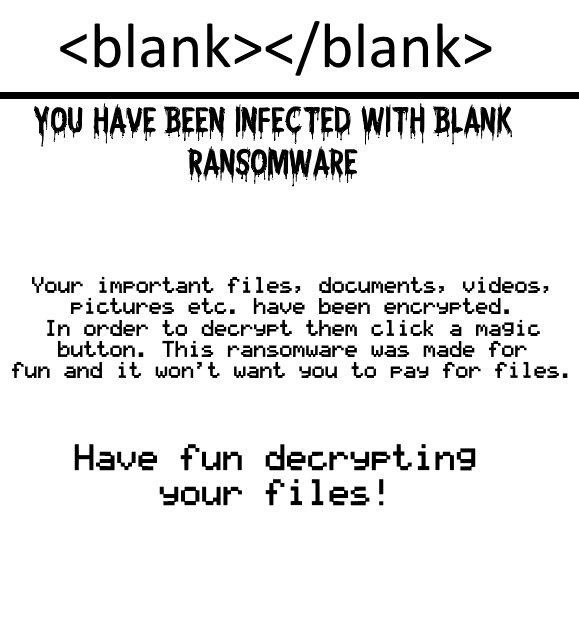
Cryptocurrency Theft Now Possible via Microsoft Word Documents
Security analysts have reported a worrying new discovery — cryptocurrency theft is now possible due to a new feature added in Microsoft Word which allows users to embed multimedia elements. Microsoft have apparently tried to ease the creation of interactive…