Cerberus Virus Android Removal GUIDE
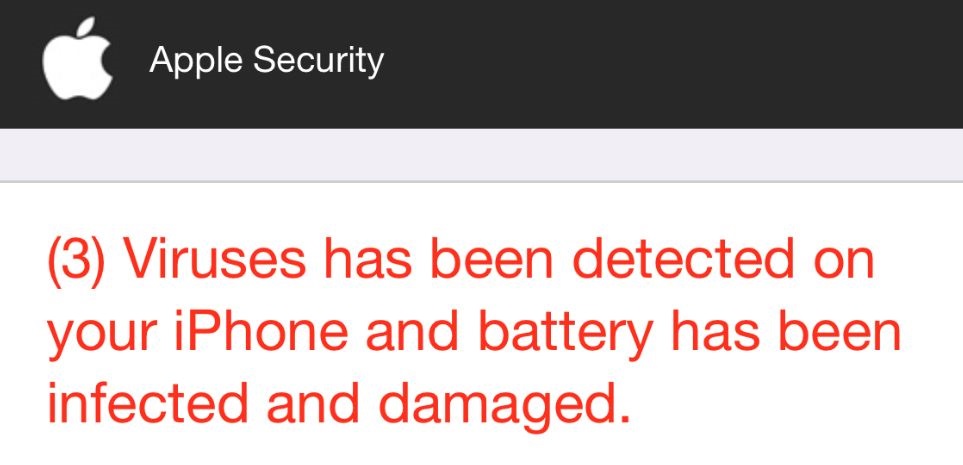
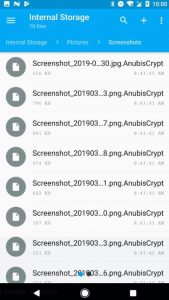
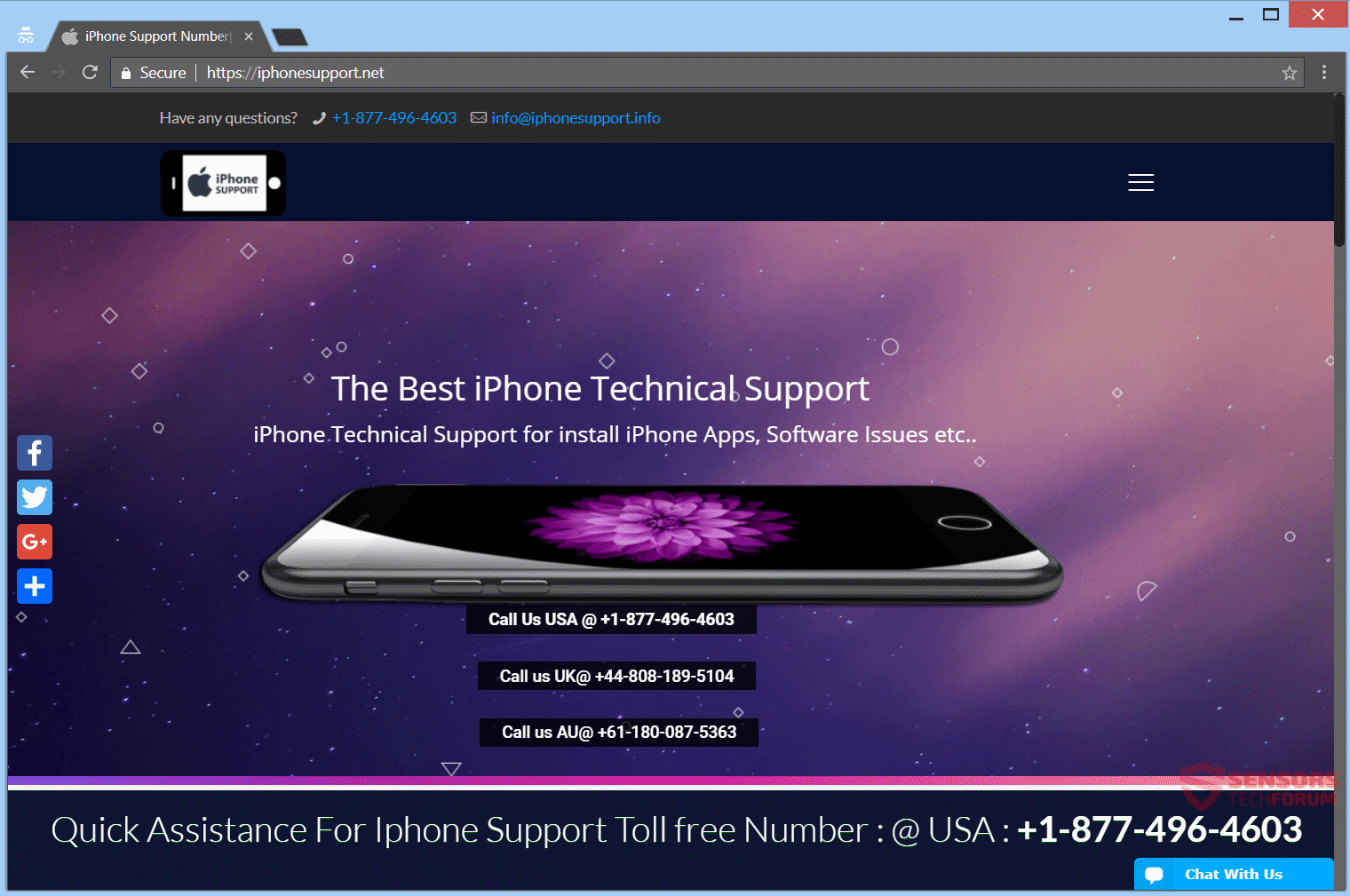
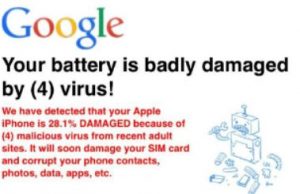
Cerberus virus for Android is a banking trojan that has the immense capability of bypassing 2 factor authentication and unlocking your phone or tablet automatically. Read this article to learn how to remove it. Cerberus Virus Android Ceberus is the…