A new Android miner malware has been uncovered – ADB.Miner. The miner is wormable and is designed to scan a wide range of IP addresses to locate vulnerable devices. The miner was discovered by researchers at Netlab security firm.

Related Story: Android Miner Virus (Coin Miner) – How to Remove It from Your Mobile
ADB.Miner – A Closer Look
Apparently, the miner is the first worm for Android that reuses the scanning code used in the infamous IoT Mirai botnet. The researchers were able to capture 9 samples of the malware, concluding that their core functions are worm propagation and mining:
– Worm infection: Infected device will initiate port scan on TCP 5555 adb interface, and attempt to – execute ADB command to copy itself to newly infected machines.
– XMR Mining: It will dig XMR tokens after infection.
More specifically, the worm uses code from Mirai’s syn scanning module which adds more efficiency to the malware as a whole. What is interesting is that the worm doesn’t employ a command and control server and directly obtains the cryptocurrency income via a single wallet address, researchers say.
Propagation
ADB.Miner is designed to scan for various types of Android devices ranging from smartphones and smart TVs to TV set-top boxes. The only specification is that these devices should be with publicly accessible ADB debug interface using port 5555 to run. Once located, the worm infects them with the mining module of the malware which seeks to mine Monero cryptocurrency.
The worm’s propagation is implemented through a feature known as droidbot. Once the worm discovers devices with port 5555 adb enabled, it will implant all the samples from local to the victim, using specific commands like the adb connect/adb push/adb shell.
As already mentioned, ADB.Miner uses the scan module source code from Mirai:
– Mirai SYN Scan module is found inside this module to accelerate the port 5555 scan. The following figure highlights the code that constructs a random IP with a target port 5555.
– The code structure is also similar to Mirai.
– This module also contains Mirai string tables, which are weak passwords encrypted by Mirai’s default key 0xdeadbeef. However, these weak passwords are NOT used in this worm.
In addition, ADB.Miner not only seeks to mine Monero but also propagate itself by scanning for more vulnerable devices on the Internet. Unfortunately, the type of vulnerability used in this operation is not known yet. What researchers believe is that the attackers are not leveraging one single flaw to target a specific vendor. As a matter of fact, researchers found devices from a number of manufacturers that were prone to this attack.
So far, the researchers detected 7,400 unique IP addresses which use the Monero mining code. Most victims are located in China and South Korea.
To avoid infection, Android users should implement a security solution on their devices and be extra vigilant with what apps they download, even from Play Store.
Preparation before removal of malware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Turn off your phone until you know how bad is the virus infection.
- Open these steps on another, safe device.
- Make sure to take out your SIM card, as the virus could corrupt it in some rare cases.
Step 1: Shut Down your phone to win some time
Shutting down your phone can be done by pressing and holding its power button and choosing shut down.
In case the virus does not let you do this, you can also try to remove the battery.
In case your battery is non-removable, you can try to drain it as fast as possible if you still have control over it.
Notes: This gives you time to see how bad the situation is and to be able to take out your SIM card safely, without the numbers in it to be erased. If the virus is on your computer, it is espeically dangerous to keep the sim card there.
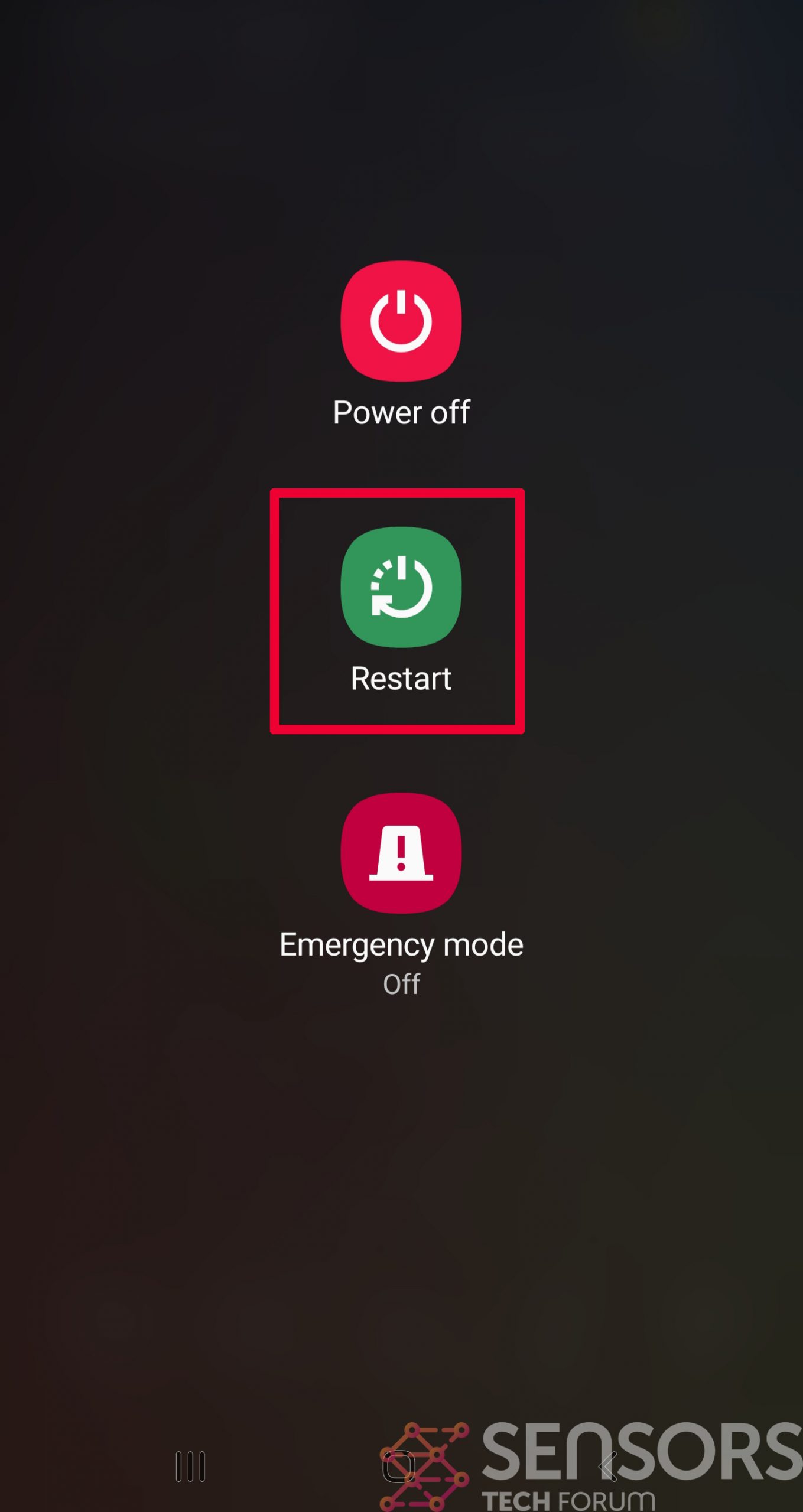
Step 2: Turn on Safe Mode of your Android device.
For most Android devices, switching to Safe Mode is the same. Its done by following these mini-steps:
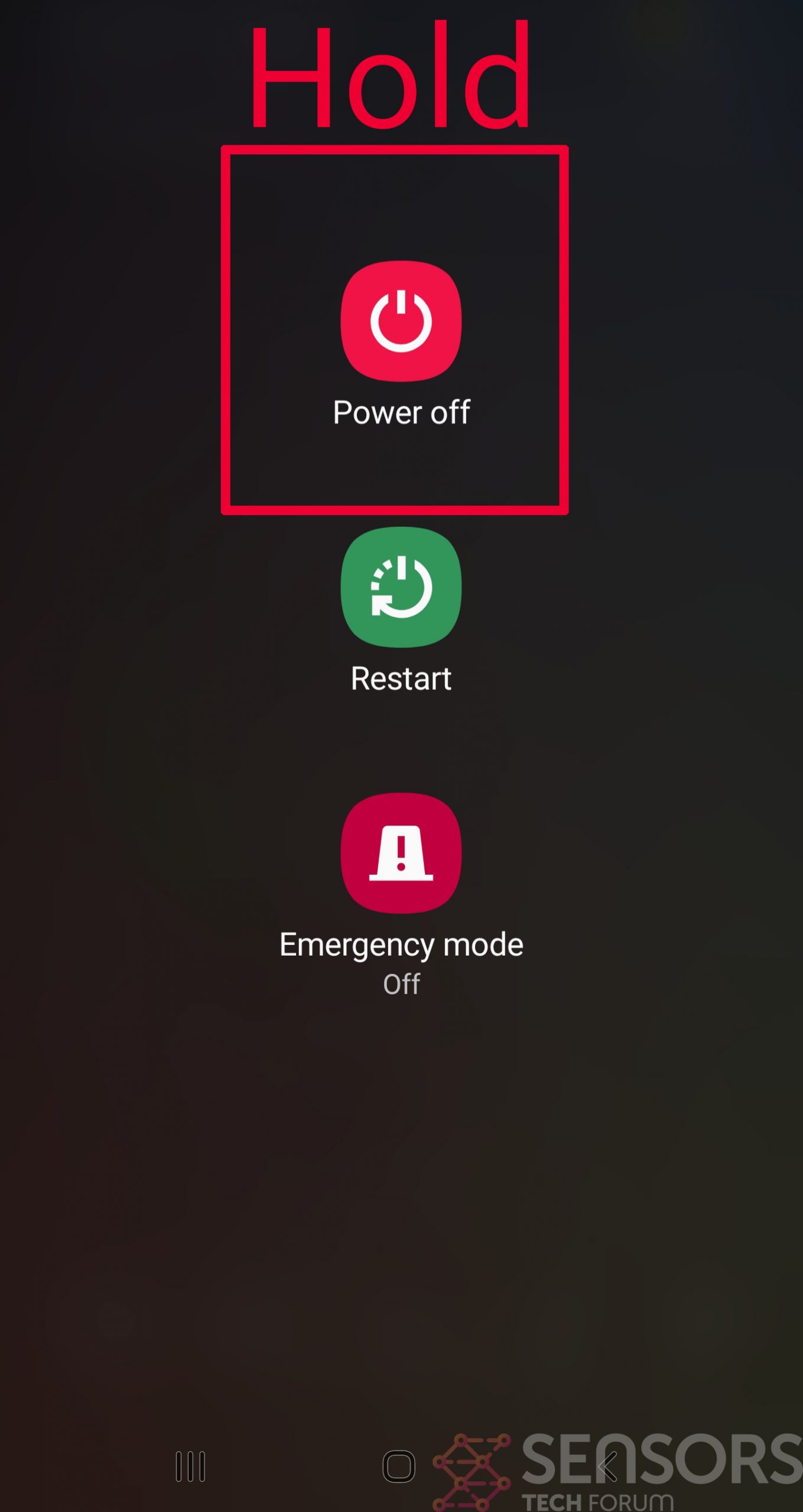
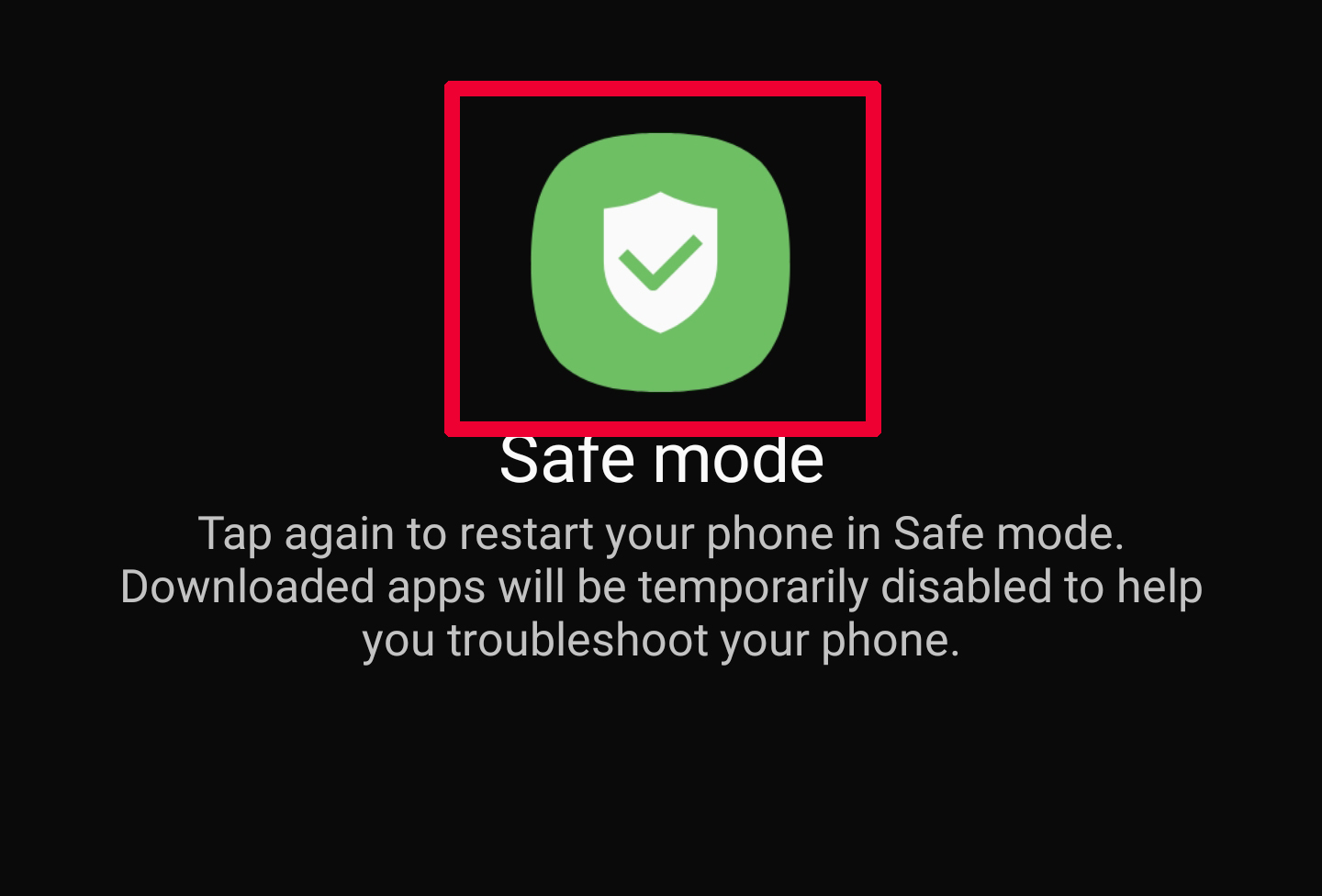

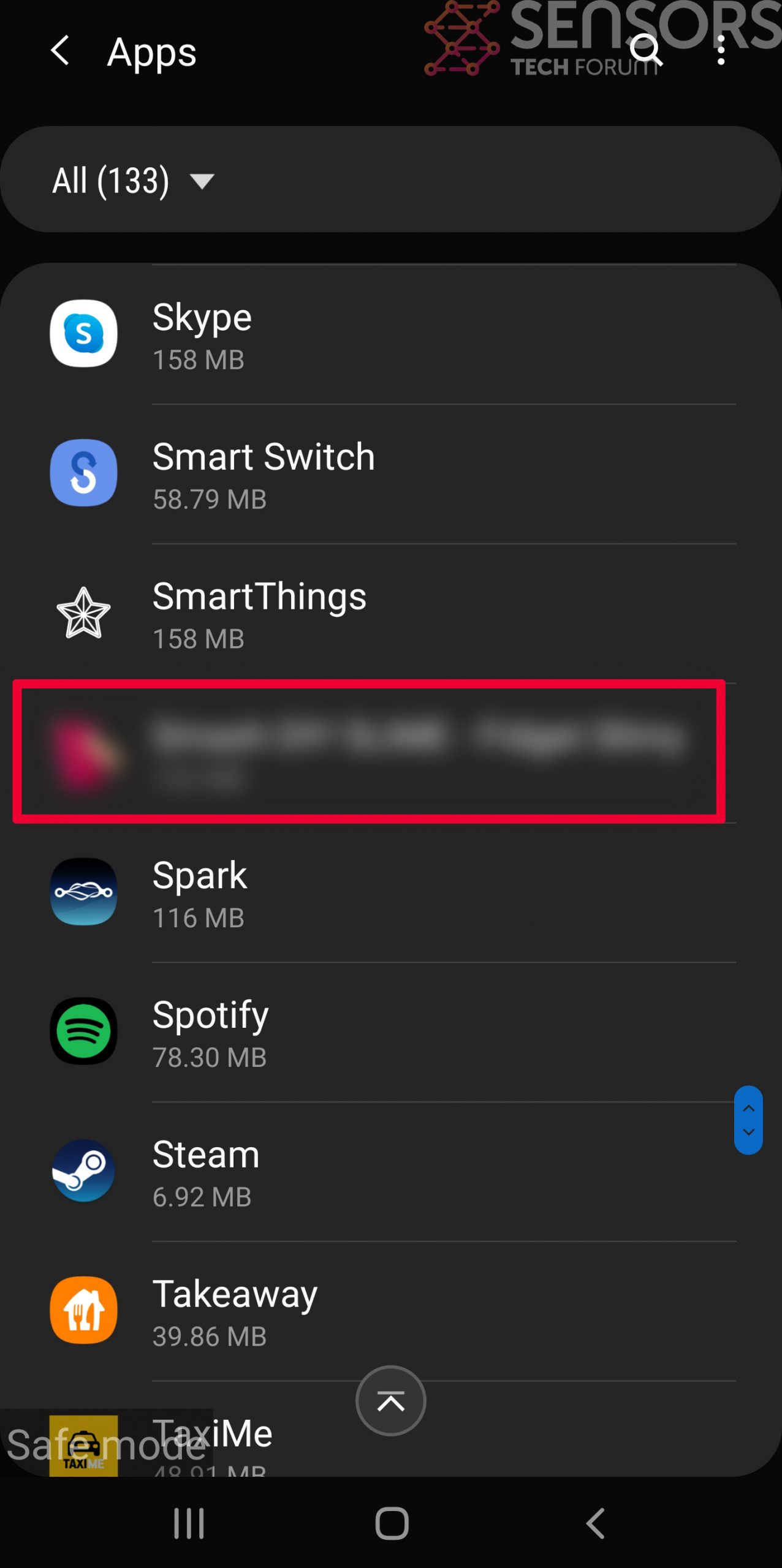
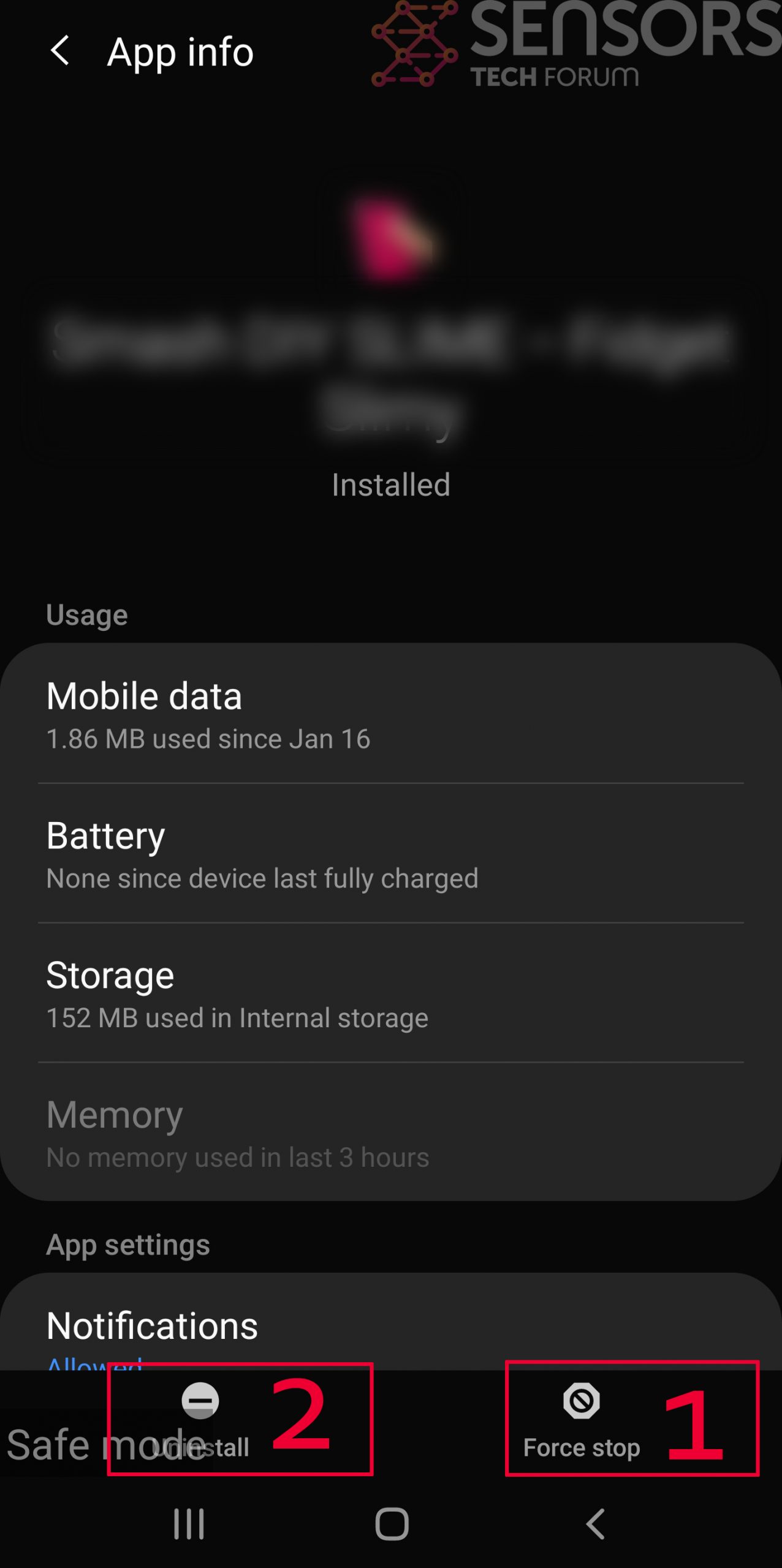
Step 3: Eliminate the App that Your Believe is the Virus
Usually Android viruses get masked in the form of applications. To eliminate apps, follow these mini-steps:
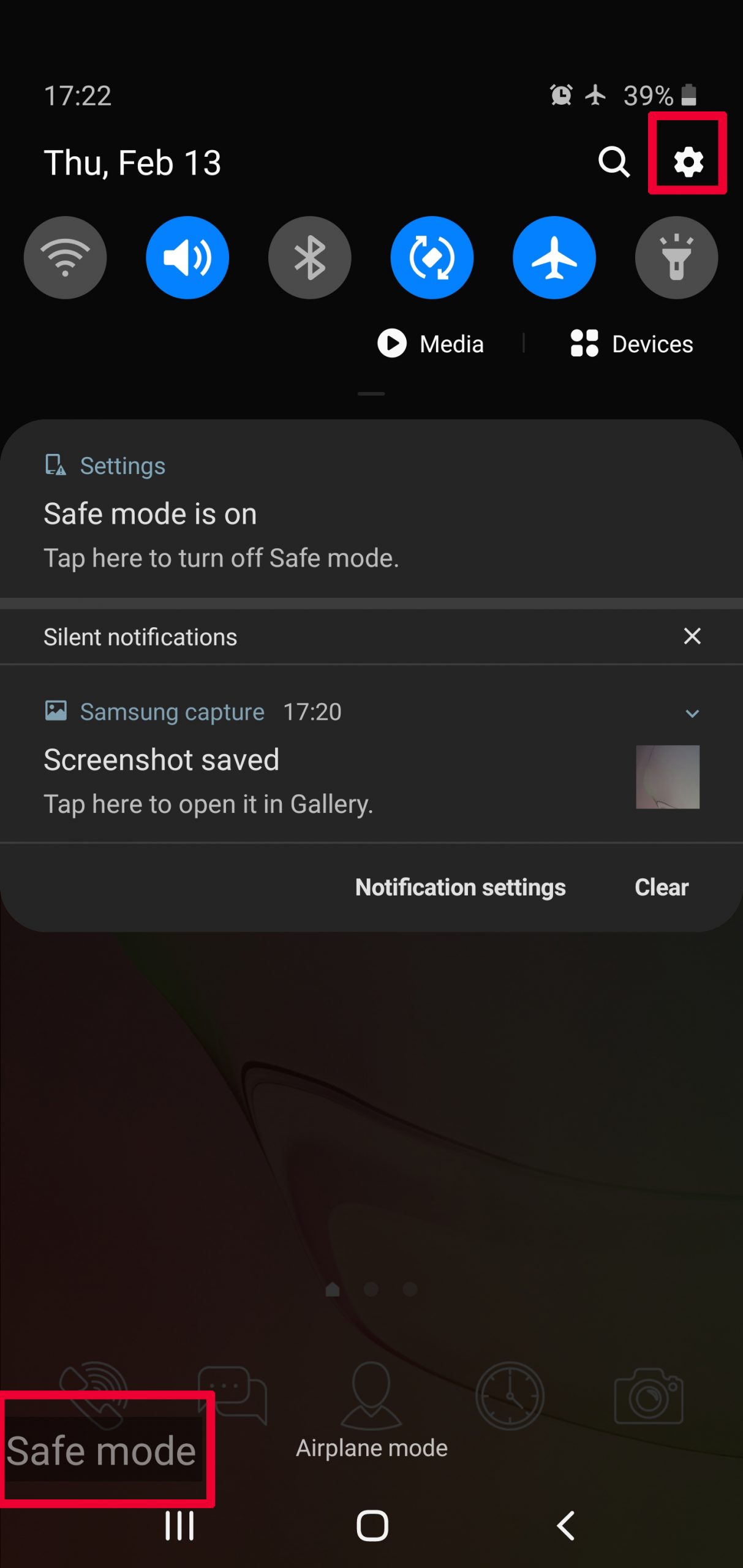
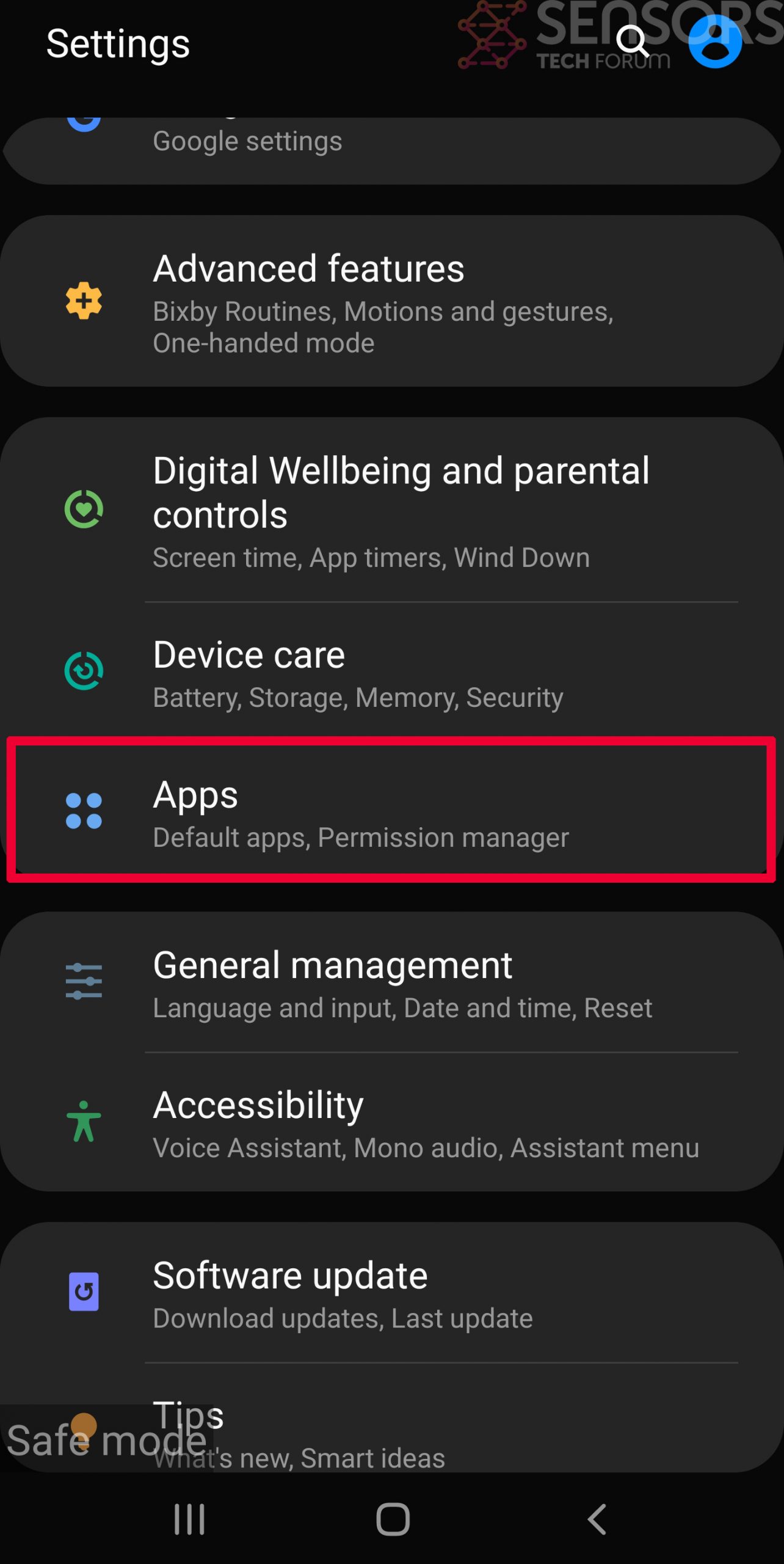
Step 4: Find Hidden Virus Files on Your Android Phone and Remove Them
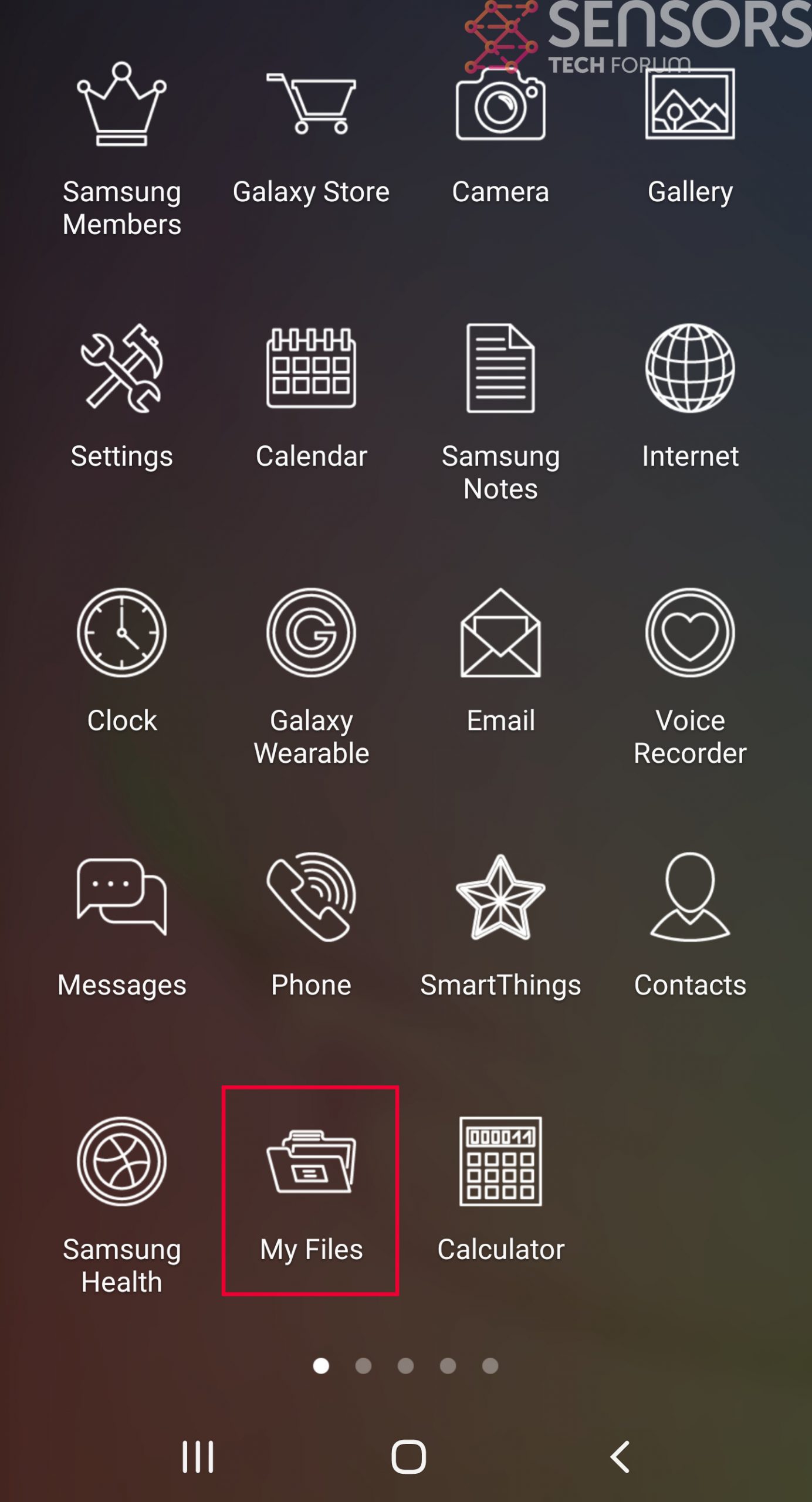
Simply locate the virus and hold-tap on the virus file to delete it.













