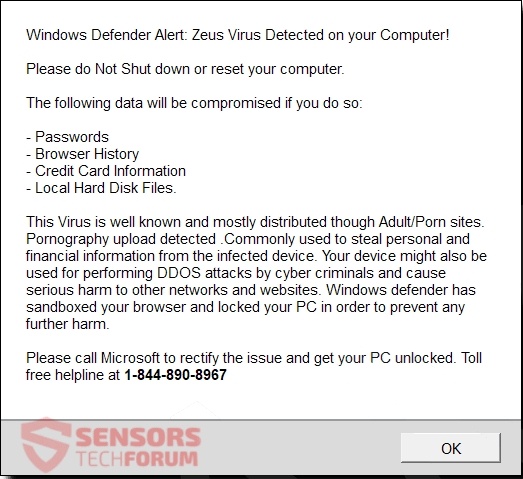
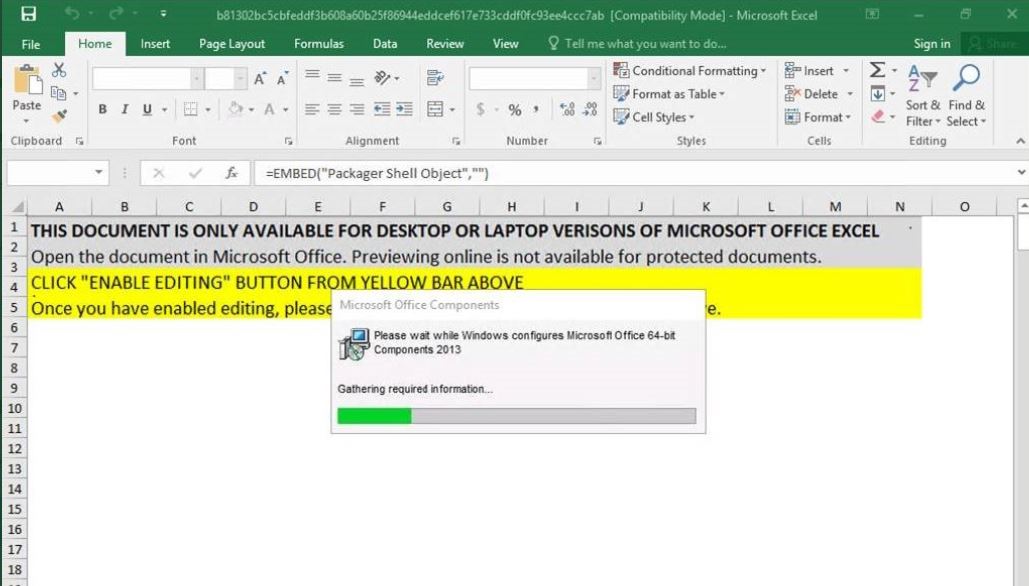
Corona-Virus-Map.com Fake Page Redirect – Removal Guide
What is Corona-Virus-Map.com ? Is Corona-Virus-Map.com a virus or is it safe? Just how to get rid of the Corona-Virus-Map.com malware from your computer system? Corona-Virus-Map.com Redirect A brand-new type of malware, pertaining to a google domain name has been…