What Is Malware?
Malware, a term that emerges from combining ‘malicious’ and ‘software’, represents a wide array of cyber threats designed to harm or exploit computers and networks.
Given its nature, malware poses a significant challenge to digitaxal security, affecting individuals and organizations alike. Recognizing malware means understanding that it’s not one but many different types of threats, each with its own method of invasion and damage infliction.

Quick Details
| Name | Malware |
| Type | Malware (Computer Virus, Trojan, Ransomware, Adware) |
| Removal Time | Around 15 Minutes to scan the system and detect any threats |
| Removal Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
Modern Malware Types
Nowadays, malware embodies one of the most significant cyber threats. From the simple viruses of the early digital era to the complex ransomware attacks we see today, malware has evolved. It now leverages sophisticated techniques to infiltrate systems, often without the user’s knowledge. This evolution has been driven by the digital age’s expansion, where the proliferation of IoT devices, cloud computing, and an ever-increasing online presence have provided fertile ground for cybercriminals.
The modern definition of malware extends beyond a simple malicious software. It now includes a variety of threats like viruses, worms, Trojan viruses, spyware, adware, and ransomware. Each variant has a unique method of attack. For instance, viruses attach themselves to clean files to corrupt systems, while ransomware locks or encrypts files, demanding a ransom for their release. Spyware secretly monitors user actions to gather sensitive information, showcasing the diversity in how these threats operate.
Despite the varied nature of malware, its end goals remain consistent: to steal, to damage, or to disrupt. Cybercriminals deploy malware through cunning methods such as email attachments, fraudulent links, or through compromised websites. Once inside a system, malware can execute its malicious processes, from quietly stealing data to overtly hijacking system resources. The stakes are high in the fight against malware, as the potential for harm spans from personal data theft to crippling major organizations’ operations.
Combatting this menace requires more than just awareness; it necessitates the use of sophisticated security solutions like SpyHunter. SpyHunter is designed to offer protection against the plethora of malware variants lurking in the digital shadows.
How the Different Malware Types Can Affect Your Computer and Privacy
Malware encompasses various forms of harmful software designed to infiltrate, damage, or disable computers and computer systems. Its impact on your computer and privacy can range from mildly annoying to catastrophically destructive. Understanding these impacts is crucial for recognizing the importance of proactive measures in cybersecurity.
The Immediate Impacts of Malware Infections
The moment malware makes its way onto your device, it begins its task, which could vary based on its type and the intentions of its creators. Here are common immediate impacts:
- Data Loss: Malware such as ransomware can lock you out of your own files or even wipe them completely, leading to significant data loss.
- Decreased Performance: Many types of malware consume system resources, resulting in noticeable slowdowns in performance and responsiveness of your device.
- Unauthorized Access: Some malware variants act as a gateway for cybercriminals, granting them unauthorized access to your computer and your personal information.
- Ad Pop-ups and Redirects: Adware can inundate your computer with unwanted ads, significantly hampering your browsing experience.
These immediate impacts not only disrupt daily activities but also expose users to further security risks.
Long-term Consequences of Ignoring Malware
Failure to address malware infections swiftly can lead to long-term consequences that extend far beyond initial inconveniences:
- Severe Data Breach: Over time, malware can steal more sensitive information, leading to identity theft and financial fraud that can tarnish your reputation and have lasting financial repercussions.
- Compromised Personal and Professional Information: Malware can gain access to personal emails, documents, and even work-related information that could be exploited for espionage or blackmail.
- System Instability: Continued malware activity can lead to system instability, frequent crashes, and eventual hardware failure, requiring costly repairs or replacements.
- Network Spread: Certain malware types, like worms, are designed to spread across networks, potentially compromising not just your own device but also those of your family, friends, or colleagues.
The long-term consequences underscore the importance of not just reactive but also proactive steps in guarding against malware. Utilizing comprehensive security solutions like SpyHunter can offer significant protection. SpyHunter actively monitors and removes malware, safeguarding both your computer’s performance and your personal privacy against the omnipresent threat of malicious software.
Addressing the immediate impacts and preventing the long-term consequences of malware infections require a blend of vigilance, education, and the right tools. By understanding the risks and implementing security measures, individuals and organizations can significantly reduce their exposure to malware’s harmful effects.
Malware Types You Need to Know About
Malware encompasses a variety of cyber threats including viruses, worms, spyware, and more. Each type has unique characteristics and impacts on the infected devices. Understanding these differences is crucial for protecting your digital space.
While all malware is designed to harm and disrupt, the way they infiltrate and damage systems can vary greatly. Let’s explore some of the most common and threatening types.
Viruses: The Oldest Form of Malware
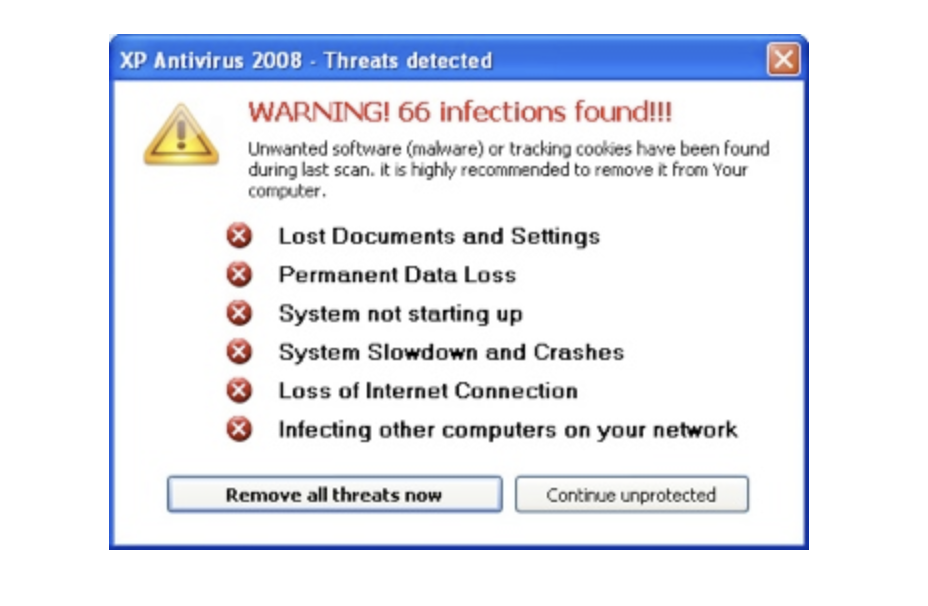
Viruses are infamous for their ability to attach themselves to legitimate programs and replicate. They spread by executing infected software, often corrupting files or systems in the process. Despite advances in security, viruses remain a persistent threat due to their evolving complexity.
Worms: Self-Replicating Threats
Worms spread across networks without the need for a host file, exploiting vulnerabilities to infect devices. Their self-replicating nature allows them to spread rapidly, causing widespread damage to networks and devices. The key to combating worms is maintaining updated systems and utilizing reliable security software like SpyHunter to detect and remove these threats.
Spyware: Silently Monitoring Your Activities
Spyware operates covertly, collecting data without the user’s knowledge. From keystrokes to browsing habits, it can expose sensitive personal and financial information to cybercriminals. Regular system scans with trusted security solutions are essential for identifying and removing spyware.
Ransomware: The Growing Online Extortion Scheme
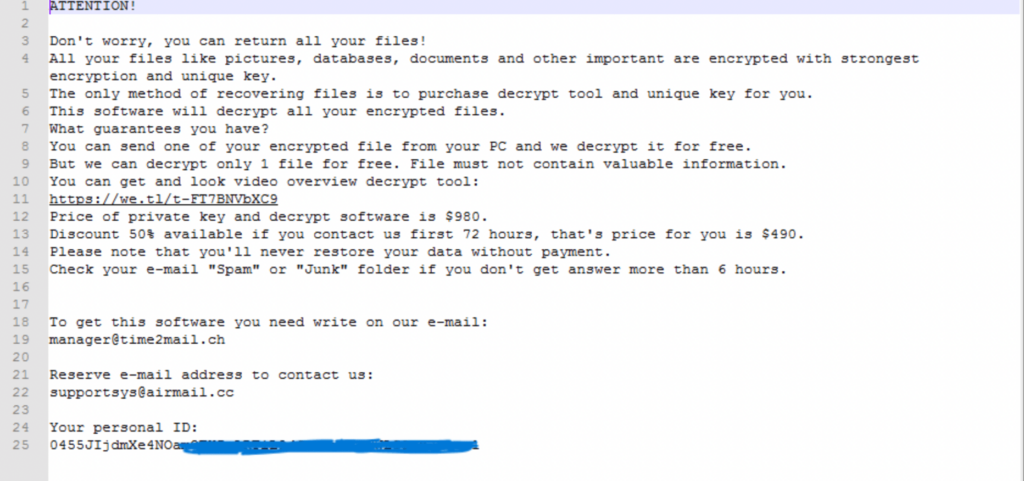
Ransomware locks or encrypts victims’ files, demanding payment for their release. It has become a significant threat to individuals and organizations, emphasizing the need for robust backup strategies and the use of security software like SpyHunter for early detection and prevention.
Adware: Annoyance or Threat?
Adware may seem less harmful as it often just displays unwanted advertisements. However, it can slow down systems and sometimes serve as a gateway for more malicious software. Ensuring your computer’s security settings are strong can help mitigate the risks posed by adware.
Trojans: The Deceptive Killers
Trojans disguise themselves as legitimate software to infiltrate devices. Once inside, they can execute malicious actions, from stealing data to installing other malware. Vigilance in downloading software only from reputable sources and employing comprehensive security tools are critical defenses against Trojans.
Rootkits: Deep Hidden Threats
Rootkits embed themselves deep within a computer’s operating system, giving attackers control over the affected device without detection. Detecting and removing rootkits require specialized tools and a deep understanding of the system’s workings. Utilizing a security solution like SpyHunter, known for its rootkit detection capabilities, is advisable for dealing with these sophisticated threats.
Understanding the characteristics and behaviors of these malware types is the first step toward securing your devices. Regular updates, cautious online behavior, and a reliable security solution like SpyHunter are your best defense against the diverse threats posed by malware in today’s digital environment.
Signs Your Device May Be Infected With Malware
Recognizing the early signs of malware infection can save you from potential data loss and privacy invasions. When malware sneaks into your device, it can manifest through various indicators. Paying attention to these signs ensures you can take timely action, potentially by employing solutions like SpyHunter for malware detection and removal.
Unusual Activities That Signal a Malware Infection
Malware infections often reveal themselves through odd or unexpected device behavior. Being alert to these symptoms can be your first line of defense against further damage.
Unexpected Ads and Pop-ups
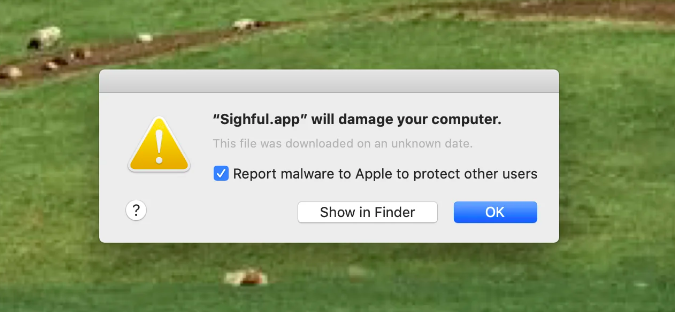
One of the most glaring signs of malware infection is the sudden appearance of ads and pop-up windows, especially those that appear without interacting with a web browser. These unwelcome intrusions can not only disrupt your computing experience but also pose a risk of further malware infections if clicked. Random or inappropriate pop-up windows can indicate adware, a type of malware designed to display or download advertising content without your consent.
Significant Slowdowns and Crashes
If your computer or device is experiencing slowdowns that are out of the ordinary, or if applications crash more frequently without a clear reason, it could be a symptom of malware. Malware can consume your device’s resources, leading to sluggish performance and system instability. This slowdown is especially noticeable if the device was previously operating at optimal speed and suddenly begins to lag or crash during regular operations. Routine tasks such as opening files, browsing the internet, or starting up your device become arduous and time-consuming.
Suspicious Hard Drive Activity
An unusual amount of hard drive activity, such as frequent, inexplicable whirring sounds or the hard drive light blinking excessively when the device is not being used for data-intensive tasks, may suggest a malware infection. This behavior could indicate that malware is actively running tasks in the background, modifying, encrypting, or transmitting data without your knowledge. In such cases, it’s vital to scan your system with a reliable security tool like SpyHunter to identify and eliminate the malware threat.
Being vigilant about these signs and taking immediate action can prevent the escalation of malware threats. Employing advanced security tools that offer real-time protection, like SpyHunter, is a proactive step towards safeguarding your device against the sophisticated malware types prevalent today.
The Journey of Malware: How It Finds Its Way to Your Device
Every day, countless devices are at risk of infection by malicious software, commonly known as malware. Understanding how malware penetrates systems is crucial for protecting your digital life. This journey into your device typically begins with seemingly benign interactions that hide a darker purpose.
Common Techniques Hackers Use to Deploy Malware
To safeguard your devices, it’s important to know the common techniques hackers use to deploy malware. Awareness is the first step towards protection.
Phishing Attacks: The Lure of Deceptive Emails
Phishing attacks are a prevalent method that cyber criminals use to spread malware. These deceptive emails masquerade as legitimate correspondences from trusted entities, tricking recipients into opening harmful attachments or clicking on malicious links. The simplicity of this tactic, combined with the sophisticated disguise, makes it dangerously effective. For those wondering how to fend off these attacks, the answer lies in vigilance and the use of reputable security software, like SpyHunter, which can detect and mitigate threats lurking in emails.
Malvertising: When Ads Turn Malicious
Another unexpected vehicle for malware is malvertising, a blend of malware and advertising. Here, lawbreakers exploit online ad networks to inject malicious ads into legitimate websites. Unsuspecting users clicking on these ads may inadvertently download malware onto their devices. Protecting yourself from such threats involves keeping your browser and its extensions updated and employing robust security solutions that can block malicious ads and websites, thereby keeping your browsing safe.
Drive-by Downloads: Unwanted Loads During Browsing
Drive-by downloads occur when visiting a website leads to the automatic download of malware, without any interaction from the user apart from navigating to the infected page. Attackers exploit security weaknesses in browsers, plugins, and software to execute these downloads, making it critical to maintain all software with the latest security patches. Implementing a multilayered defense strategy that includes the use of comprehensive security tools, like SpyHunter, can significantly reduce the risk of such stealthy infections by providing real-time protection against emerging threats.
Tools and Techniques for Spotting Malicious Software
Identifying malware requires a vigilant eye and the right tools at your disposal. Anti-malware solutions play a crucial role in spotting and neutralizing threats before they escalate. These solutions should be updated regularly to recognize the latest malware signatures and utilize heuristic analysis to detect novel threats. In addition, understanding the common indicators of a malware infection – such as system slowdowns, unexpected pop-ups, and unauthorized changes to system settings can prompt a timely investigation.
- Ensure regular system scans with updated antimalware software to catch threats early.
- Train employees on cybersecurity best practices and the importance of reporting suspicious activity immediately.
- Employ network monitoring tools to detect unusual traffic patterns or unauthorized data transfers.
- Keep all software and operating systems updated to minimize vulnerabilities that can be exploited by malware.
- Implement strong access controls and use multi-factor authentication (MFA) to reduce the risk of compromise.
Using SpyHunter for Comprehensive Malware Scanning and Removal
When it comes to comprehensive malware types detection and eradication, SpyHunter provides a robust solution tailored to the complexities of modern malware. Its advanced scanning engine is designed to identify and remove malware infections, including those that are deeply embedded within the system. SpyHunter’s regular updates ensure its effectiveness against both current and emerging threats.
- SpyHunter offers simplified detection and removal of malware, providing peace of mind for users across various experience levels.
- Its user-friendly interface allows for quick navigation and execution of malware scans, making it accessible for everyone.
- The integrated Spyware HelpDesk offers personalized assistance, demonstrating a commitment to resolving complex malware issues.
- Advanced heuristic techniques enable SpyHunter to detect new malware variants based on behavior and characteristics.
By integrating tools like SpyHunter into your malware defense strategy, you can ensure a higher level of protection against an ever-evolving digital threat landscape. It’s essential to complement these technical solutions with strong cybersecurity policies and ongoing education to create a comprehensive defense against malware.
Preventing Malware Attacks
Today, the threat of malware is more prevalent than ever, making it crucial for individuals and organizations to bolster their cybersecurity defenses. This guide will walk you through practical steps to mitigate the risk of malware infections, enhancing your cybersecurity posture.
Essential Tips for Enhancing Your Cybersecurity Posture
To effectively shield yourself and your organization from the myriad of cyber threats, it’s vital to adopt a comprehensive cybersecurity strategy. The following tips serve as a cornerstone for building a robust defense against malicious software.
Update Regularly: The Shield Against Vulnerabilities
One of the simplest yet most effective measures to protect against the different malware types is to keep all software and operating systems up to date. Software developers regularly release updates that fix bugs and vulnerabilities that cybercriminals exploit to launch malware attacks. Ensure automatic updates are enabled on your devices to maintain the highest level of security without the need to remember manually checking for updates.
Practicing Safe Browsing Habits
Safe browsing habits are your first line of defense in the prevention of malware infections. Avoid visiting websites known for distributing pirated content or ones that bombard you with pop-up ads, as these are often laced with malware. In addition, employ tools that block pop-ups and adware, enhancing your browsing experience while reducing the risk of accidental malware downloads. Remember, if a website feels suspicious or offers deals that seem too good to be true, it’s best to err on the side of caution and navigate away.
Email Safety: Avoiding Phishing Pitfalls
Phishing scams, where cybercriminals impersonate legitimate entities to trick you into disclosing sensitive information or downloading malware, are rampant.
Exercise caution with emails, especially those urging immediate action or containing unexpected attachments. Verify the sender’s legitimacy by checking their email address against known addresses for the entity they claim to represent. When in doubt, contact the entity directly using official contact information rather than links or numbers provided in the suspicious email. SpyHunter’s email scanning feature can serve as an effective ally, identifying and isolating potential threats hiding in email attachments or links, adding an extra layer of security to your digital communications.
Implementing these strategies will significantly enhance your cybersecurity posture, reducing the likelihood of falling victim to malware attacks. It’s crucial to stay informed on the latest cyber threats and continue educating yourself and your team on safe online practices.
Understanding the Impact of Malware on Mobile Devices
Malware, short for malicious software, represents a significant threat to mobile devices, including both smartphones and tablets. With mobile devices now integral to our daily lives, they have become prime targets for hackers seeking to exploit personal information or disrupt operations.
Malware can affect devices in various ways, from stealing sensitive information to displaying unwanted ads. The impact of malware goes beyond individual inconvenience; it poses serious security risks that can lead to financial loss and compromised data.
Are Smartphones at Risk of Malware Attacks?
Yes, smartphones are at risk of malware attacks and, in some ways, can be more vulnerable than computers. Mobile devices are always on and often connected to the internet, providing a constant opportunity for hackers. Android devices, in particular, are a popular target due to the open nature of their operating system and the ability to install apps from third-party sources.
However, even iOS devices are not immune, especially when jailbroken, which removes the protective barriers put in place by Apple.
Signs that a smartphone has been infected with malware include a sudden drop in battery life, increased data usage, unexpected ads or pop-ups, and unusual activity, such as calls or messages sent without the user’s consent. These symptoms can disrupt the user experience and, more critically, indicate that personal information is at risk.
Ultimately, understanding the threat of malware and taking proactive steps to protect your mobile device is essential in today’s connected world. By recognizing the signs of a compromised device and employing protective measures, such as using SpyHunter, users can significantly reduce the risk of falling victim to malware attacks.
Malware Types Evolution: A Look at Its Origins and Future Trends
The journey from the initial appearance of malware to its current state reflects a sophisticated evolution, highlighting a continuous battle between cybersecurity measures and threat actors. The origin of malware traces back to the early days of computing, with instances like the Creeper virus in 1971, which, although relatively harmless, marked the beginning of what would become a global challenge.
Since then, malware has diversified immensely, with variants such as viruses, worms, ransomware, and spyware becoming part of the cybersecurity lexicon. This evolution has been largely driven by the expanding digital landscape, offering both new opportunities and vulnerabilities.
The Ongoing Battle Against Cyber Threats
This ongoing battle is not only about developing more advanced defensive technologies but also about fostering a culture of security awareness among users. Phishing, one of the most common attack vectors, exploits human vulnerabilities, illustrating that the human aspect is as crucial to address as the technological one.
The future of this battle likely involves a combination of automated defenses powered by AI and machine learning, alongside continuous education on cybersecurity best practices for users. As malware becomes more sophisticated, leveraging everything from artificial intelligence to blockchain, the responses to these threats must similarly evolve.
Employing a security-first mindset, adopting a zero-trust model, and ensuring systems are regularly updated and patched will be key tenets in this ongoing battle. Significantly, tools that can adapt and respond to new threats in real-time, such as SpyHunter, will be vital in providing users and organizations with the means to protect against malware’s relentless evolution.
Ultimately, as we look towards the future, it’s clear that the fight against malware is a dynamic and persisting challenge. Staying informed about the latest threats and maintaining robust security measures are critical for individuals and organizations alike to mitigate the risks posed by this ever-changing threat landscape.
The Importance of Regularly Updating Your Malware Protection Tools
In the digital age, the threat landscape is constantly evolving. Malware creators are regularly developing new strategies and technologies to breach security systems. This relentless pace means that malware protection tools must also evolve to remain effective.
The importance of keeping these tools updated cannot be overstated. Regular updates ensure that your software has the most recent defenses against the latest threats. Just as a vaccine needs to be updated to combat new strains of a virus, so too does your malware protection need to adapt to the newest threats.
Why Staying Updated Is Crucial for Your Digital Safety
Your digital safety hinges on the strength of your malware protection tools. These updates perform several critical functions for your cybersecurity strategy. First, they patch vulnerabilities in the software that hackers could exploit.
Every day, vulnerabilities are found in even the most reliable systems. Updating your software seals these gaps and makes it harder for attackers to infiltrate your systems. Second, updates enhance the software’s ability to detect and neutralize new malware. Malware evolves rapidly, and yesterday’s defenses might not recognize today’s threats. Lastly, staying updated can improve the efficiency and stability of your protection tools, ensuring they run smoothly and do not become a hindrance to your daily activities.
Considering the importance of keeping your software updated, it’s clear why choosing a trusted and reliable anti-malware solution like SpyHunter is key. SpyHunter frequently updates its definitions and algorithms to stay ahead of threats, making it a powerful tool in the arsenal against malware.
Its ease of use means updates can be managed easily, ensuring you’re always protected with the latest advancements in malware defense without the need to become an expert in cybersecurity. Embracing such an effective tool offers peace of mind, knowing your digital life is safeguarded against emerging threats.
Ultimately, the goal is to maintain a secure digital environment where you can conduct your activities without fear of compromise. By regularly updating your malware protection tools, you’re taking a proactive step towards this goal. It’s a simple yet profoundly effective way to ensure your digital safety in an ever-evolving threat landscape.
Wrap-Up: Staying One step Ahead of the Evolving Malware Types
Protecting against malware isn’t solely the responsibility of security software – it’s a collaborative effort that involves education, vigilance, and the smart application of technology.
Firstly, the backbone of any robust defense strategy against malware lies in the adoption of protective tools. Software solutions like SpyHunter are pivotal in this aspect. They not only provide real-time protection against a wide array of malware threats but also offer features specifically designed to proactively identify and neutralize potential vulnerabilities before they can be exploited by malicious actors.
However, technology alone cannot guarantee safety. Human actions play a significant role in either enabling or preventing malware infections. This is where the concept of user vigilance and education becomes indispensable. By fostering an environment where every user is aware of the signs of malware, understands the risks associated with reckless online behavior, and knows how to use protective software effectively, the chances of falling victim to malware attacks can be significantly reduced.
To embody this proactive stance, organizations and individuals should focus on the following areas:
- Regularly Update and Patch Systems: Ensure that all software, especially operating systems and antivirus programs, are kept up to date. Patches often contain fixes for security vulnerabilities that could be exploited by malware.
- Employ Strong, Unique Passwords: Simple or reused passwords can easily be cracked by hackers, granting them access to personal or sensitive information. Use complex, unique passwords for different accounts, and consider using a password manager to keep track of them.
- Utilize Security Awareness Training: For organizations, implementing regular training sessions to educate employees about the latest phishing techniques and social engineering tactics can fortify the human element of cybersecurity.
- Adopt a Zero Trust Approach: Never assume that your network is entirely secure. Limit access privileges based on users’ roles, verify identities rigorously, and monitor network activities for any signs of suspicious behavior.
In conclusion, while the fight against the various malware types may appear daunting, equipping oneself with the right tools like SpyHunter, coupled with a vigilant and educated approach to online behavior, can vastly improve your defenses. Remember, in the landscape of cybersecurity, knowledge, and preparation are both as valuable as any software solution. By staying informed and cautious, we can collectively stand a better chance against the ever-evolving threat of malware.




nice article, thank you! can I quote you in my school paper?
In times like these, it feels extremely unfair that computer users are constantly bombarded with so many online threats! thank you for the educational read!