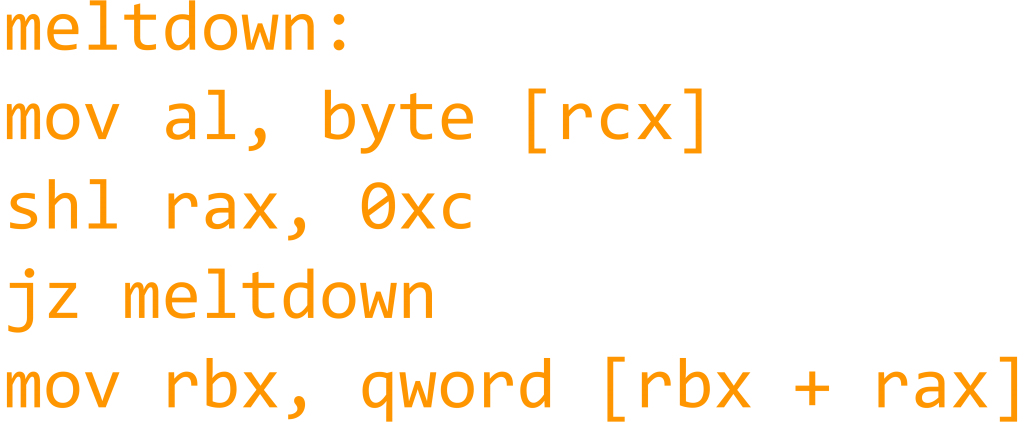
Security researchers discovered one of the most dangerous processor flaws called Meltdown and Spectre that affect almost all modern processors. The security vulnerabilities affect whole generations of computers and devices of all types that use the quoted chips. As a consequence the hackers can gain access to sensitive information that is being processed by the computers.
Meltdown and Spectre Vulnerabilities Exposed
The critical vulnerabilities were identified by several teams of experts including those from Google Project Zero and several large universities around the world. The flaws allow the attackers to break down the fundamental isolation between user applications and the operating system. The information that is being processed by the computers is therefore leaked to the attackers. A very large portion of all computer users is affected by the bug.
At the moment there is no way of detecting if a computer has been compromised by the hackers as the malware does not leave any traces in log files. Another major concern is the fact that security software (at this moment) are not able to effectively distinguish the Meltdown and Spectre exploits from regular applications. Warning signs about the infections can be produced if a piece of malware attempts to cause large-scale interventions or file manipulations. A proof-of-concept exploit reveals that the memory contents of the computer is revealed. Example data includes the following:
- Real-Time User Input — Continuous usage of the exploit may allow the hacker operators to extract the mouse movement, keystrokes and other user activities in a similar way to Trojans.
- Computer Data — In-depth information about the hardware components is gathered. The two exploits also allow the criminals to extract data from all running applications as well.
At the moment there is no evidence that the Meltdown and Spectre exploits have been used in the wild.
Which Devices Are Affected?
Affected computers include all form factors (desktop, laptops and cloud infrastructure) that includes Intel processors including the out-of-order execution function. In reality this includes every processor made by the company since 1995 except the Itanium and Intel Atom ranges before 2013. According to Google the two flaws also affect Android and Chrome OS devices. According to the tech giant AMD chips can also be exploited by the flaw. ARM Cortex-A A processors have been confirmed to be vulnerable as well.
The security experts also indicate that cloud service providers that use Intel CPUS and the XEN PV virtualization software are also affected. The reason for this is the fact that the containers rely on one host kernel, such includes are the likes of Docker, OpenVZ and LXC.
Google posted a detailed blog post that gives details on their products and services. Android devices running the latest security updates (Nexus and Pixel devices) should be protected from both vulnerabilities. The Google Chrome browser can be modified to mitigate the browser attacks by enabling the Site Isolation feature. The feature can be turned on by enabling the following flag:
chrome://flags/#enable-site-per-process
The upcoming Version 64 which is due to be released on January 23 will contain protection features against the exploit. Google Chrome OS instances running the latest security patches (version 63) are protected from the exploits.

Details on the Meltdown Exploit
The Meltdown vulnerability derives its name from the fact that it effectively melts down the security boundaries that are normally enforced by the hardware architecture of the computers. The flaw exploits side effects of the out-of-order execution capability which is part of all modern processors. This is a feature that reads the arbitrary kernel memory locations, in other words it allows the malware to gain access to all sensitive data including passwords and personal data. The security experts also note that the attacks are independent of the operating system and do not rely on any software vulnerabilities as the flaw is based on a low-level hardware design implementation.
The novel technique overcomes the memory isolation implementation completely and provides a very simple and easy method that the hackers can use to read the entire kernel memory of the compromised machines. The malware code exploits the side-channel information which is available on most modern processors. A subset of the characteristics associated with Meltdown illustrates the following capabilities:
- Low-level Access — The Meltdown exploit allows the malware operators to access the target hosts on a very deep level thereby bypassing all software and operating system security mechanisms.
- Virtualization Penetration — The security experts note that Meltdown can be used as an effective weapon against business and enterprise servers, as well as cloud services that rely on virtual machines.
- Compatible with All Modern Operating Systems — The proof-of-concept code has been found effective when reading the whole mapped memory on Linux and Mac OS X computers. The analysts report that Meltdown has also been successful to extract a large portion of the memory regions of Windows machines as well.
The Meltdown exploit can be remedied by applying a patch called KAISER which works for Linux, Mac OS X and Windows computers. At the moment it is under revision and most likely it will be sent upstream and applied by the relevant vendors and software companies in emergency/critical forthcoming updates.

Further Details on Spectre Exploit and Its Capabilities
The Spectre exploit functions in a different way by inducing the victim machines to speculatively perform operations that would not occur during standard application execution. The attack relies on two processor features: speculative execution and branch prediction. This is a performance optimization technique that is run by the CPU where it will attempt to guess what commands to run at the appropriate end addresses.
The attacks result in implementation violations that bypass computer security mechanisms. The experts note that this is part of the microprocessor code and represents a very serious issue. Vulnerable processors encompass almost all ranges from AMD, Intel and ARM which results in billions of vulnerable devices. The Spectre exploit is categorized as an entirely new type of security threat because of the fact that it employs a novel malware technique. The analysts discovered that there are two attack types that allow the hackers to gain access to sensitive hardware and user data:
- Native Code Attacks — The security experts crafted proof-of-concept applications that contain secret data within its memory access space. The malware was compiled and tested on lab computers. The results indicated that the Spectre exploit allows malicious users to leak sensitive information from the compromised hosts as well as execute dangerous code.
- JavaScript Attacks — The Spectre flaw can penetrate the browser sandbox environments and infect computer systems using JavaScript code. The security experts were able to demonstrate this by creating test malware that were able to successfully extract user data from the compromised hosts.
The Spectre exploit us much harder to exploit than Meltdown and as a result harder to mitigate. No permanent fix is available yet however several malware intrusion pathways can be secured using software patches.
Meltdown and Spectre Exploits Security Consequences
As these attacks constitute a whole new category of exploits the consequences are overwhelming. We already reported that the affected computers are a large part of all currently running machines. The fact that the intrusions in some cases cannot be detected makes it a very capable weapon in the hands of attackers. Fortunately no attacks are breaches have been reported yet. The Meltdown exploit can be remedied by applying the critical security patch and we are expecting the Spectre attack to be fixed as well.
The in-depth analysis concludes that hardware vendors must take into account the security risks of implementing such technologies. The experts propose the development of a long-term set of instructions that vendors should implement in their products in order to safeguard them from vulnerabilities. One of the proposed reasons for this is the fact that processor vendors focus more on performance optimization technologies. The usage of layers and complex code that interacts with components, device drivers and operating systems is stated as one of the most popular sources of such vulnerabilities.
How to Protect Yourself from the Meltdown and Spectre Exploits
All user software and operating system patches should be installed as soon as they are available. Unfortunately a complete solution is not yet available. However behavior-based detection tools can effectively prevent system corruption. This is possible due to the fact that advanced solutions include an advanced heuristic engine that can detect dangerous applications by using pattern recognition and other techniques. Now that the proof-of-concept code and signatures have been published to their databases the efficiency of these products is improved. We recommend that all users scan their systems with a professional-grade anti-spyware solution in order to detect any alterations or running virus processes.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter


