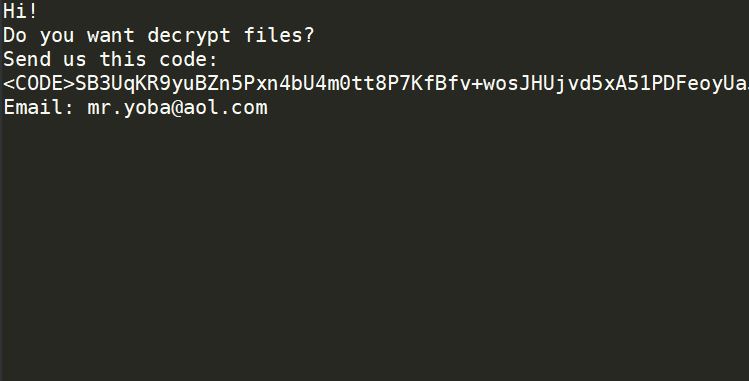
Remove Yoba Virus (.yoba File) — Yoba Ransomware
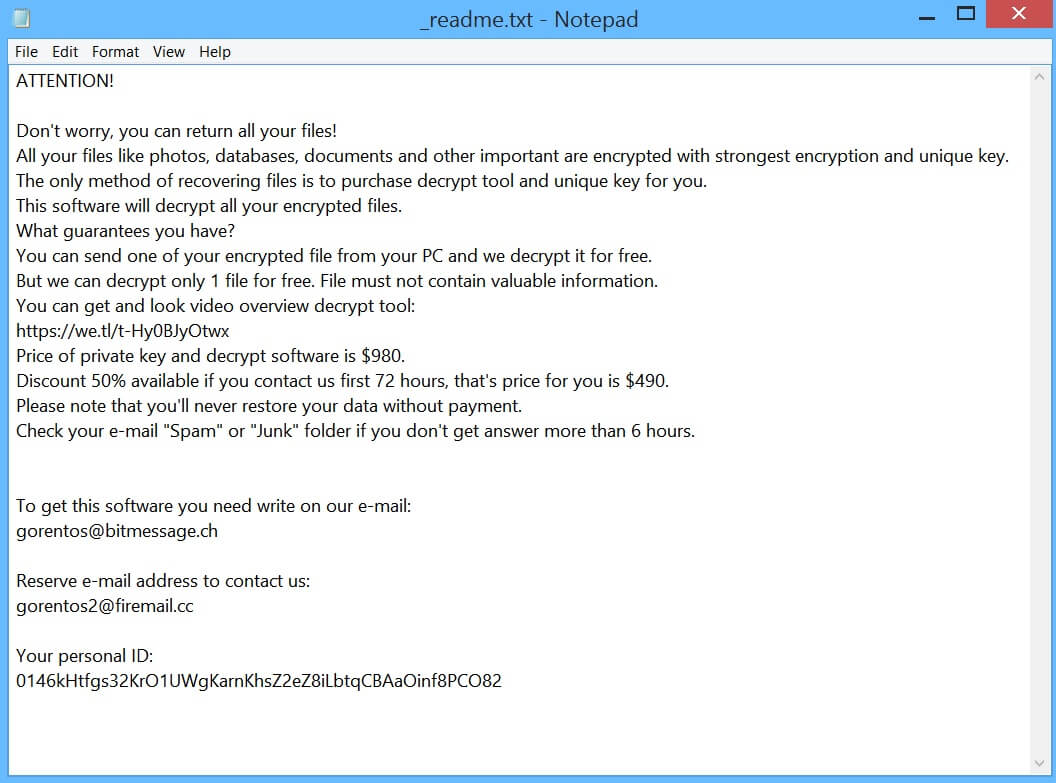
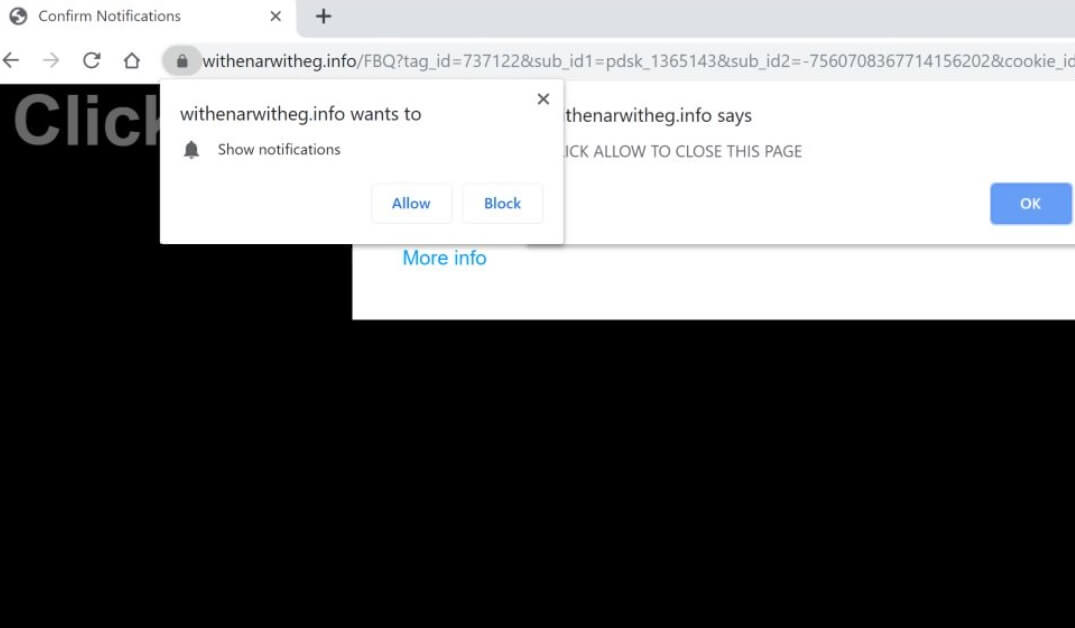
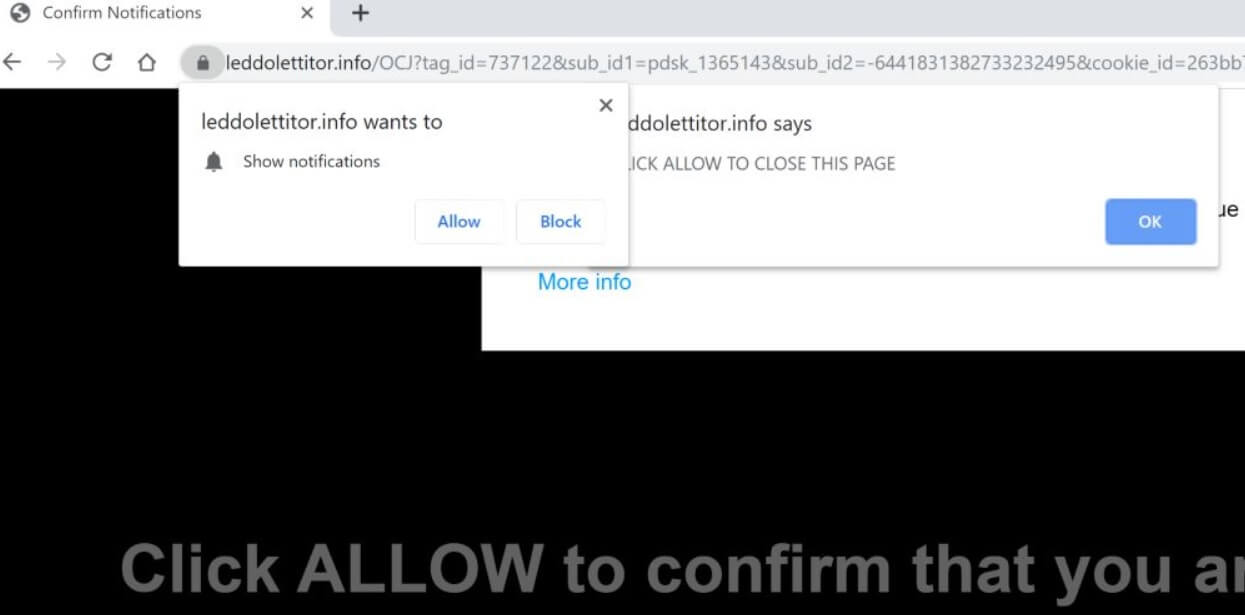
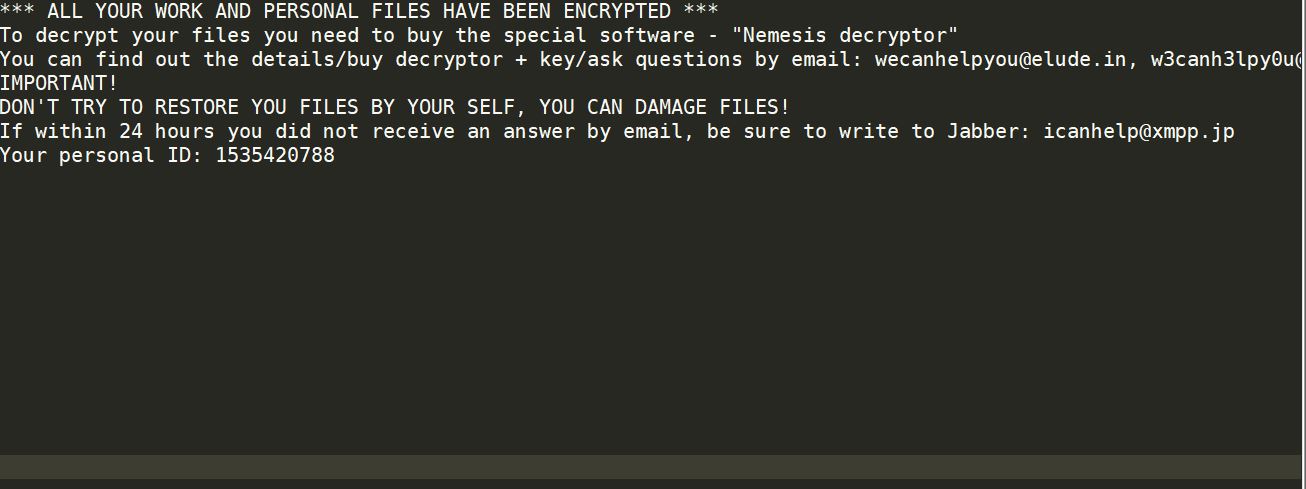
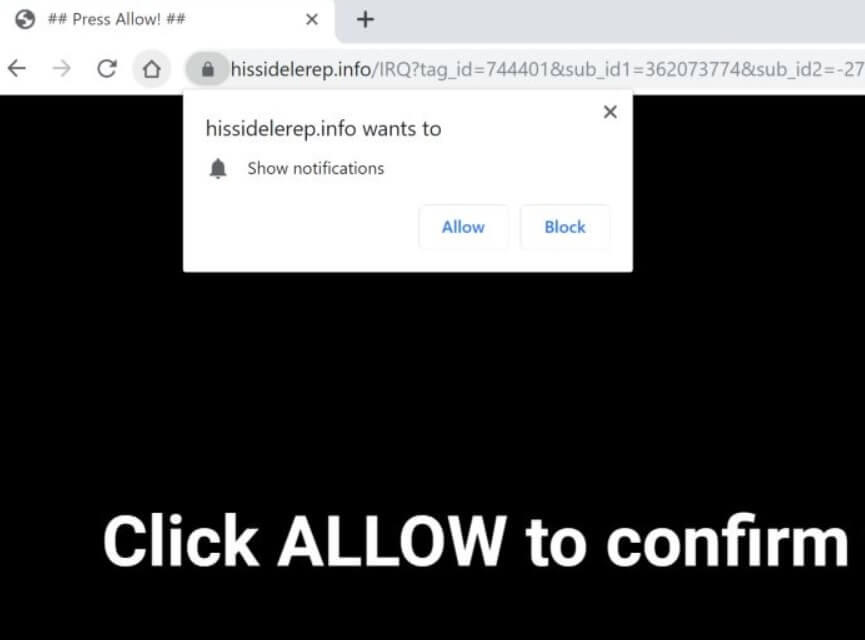
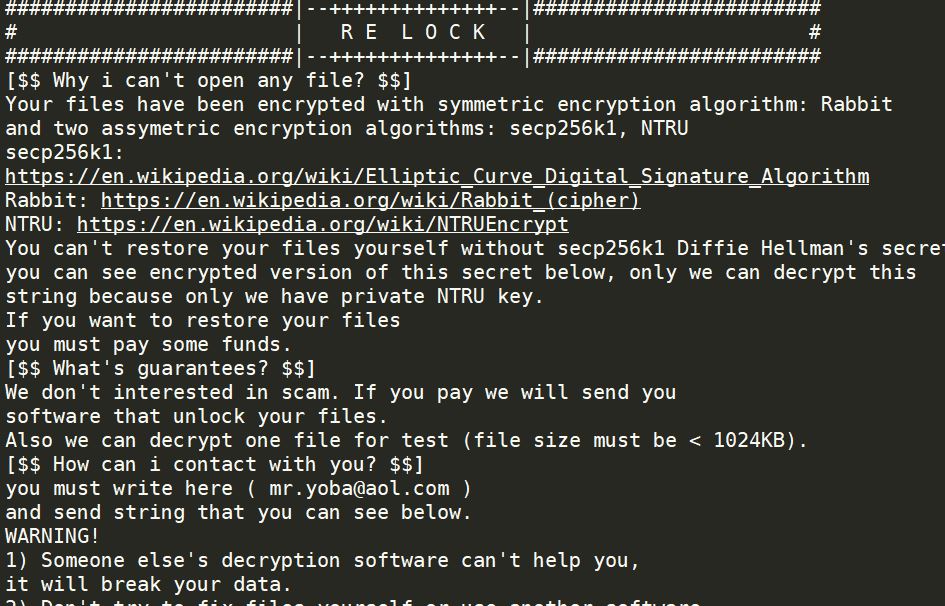
What is .yoba Virus .yoba Virus is also known as .yoba ransomware and encrypts users’ files while asking for a ransom. The .yoba Virus is new ransomware malware which should be removed as soon as possible after the infection has…