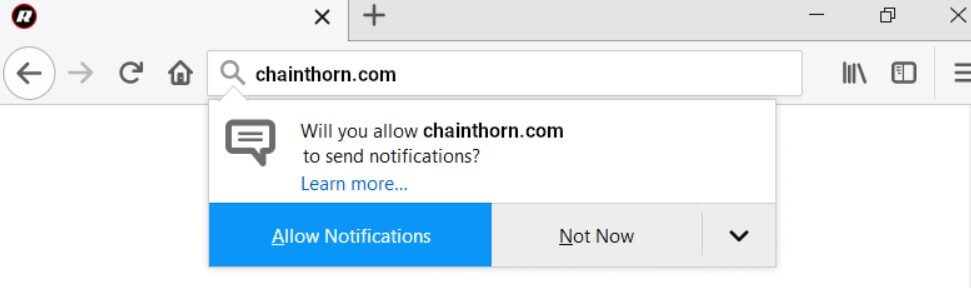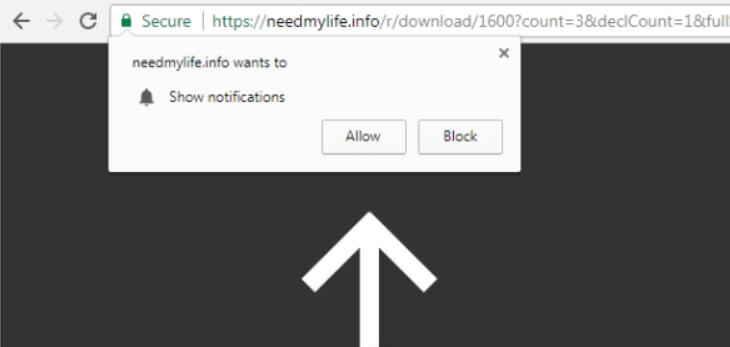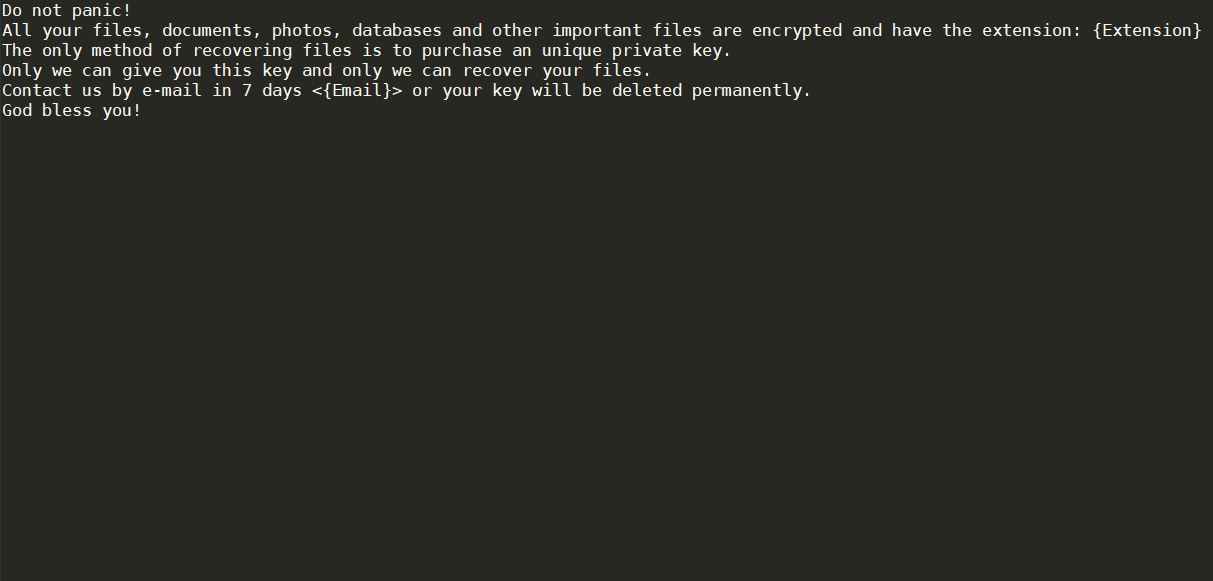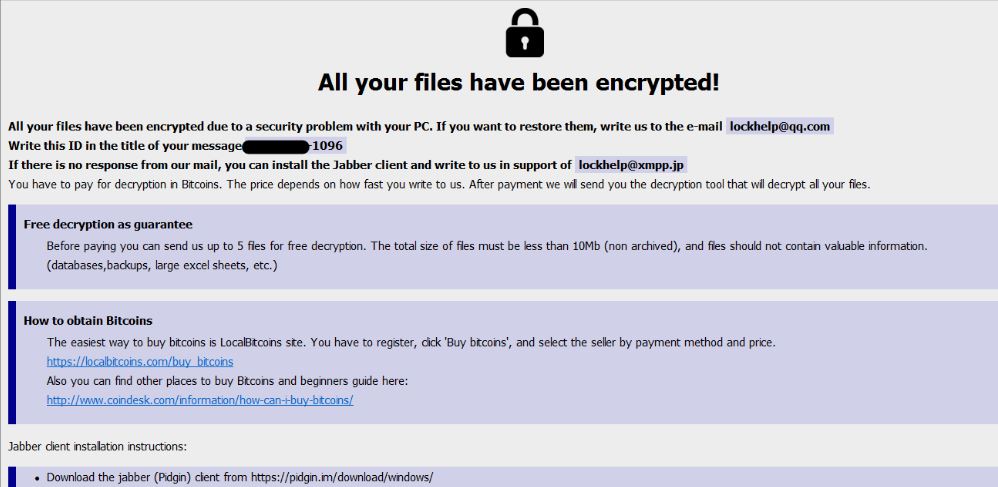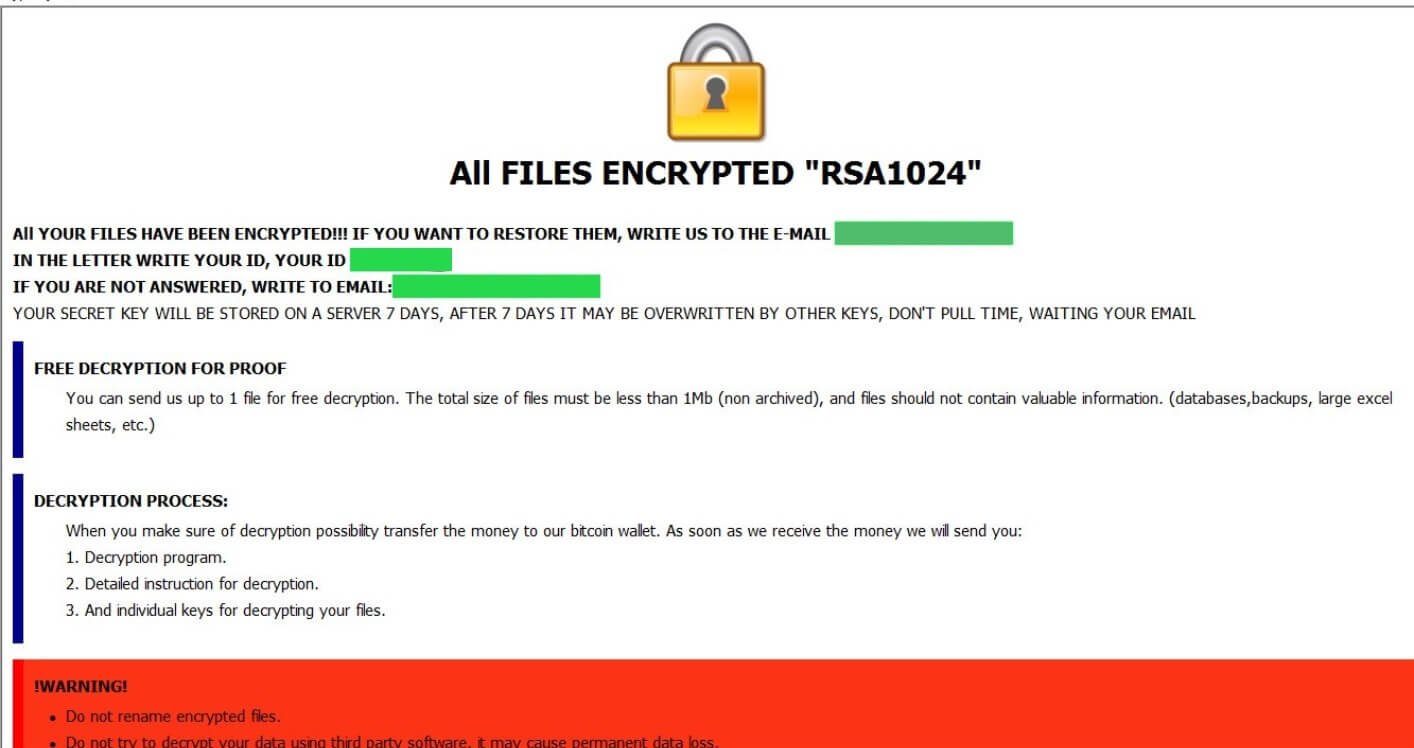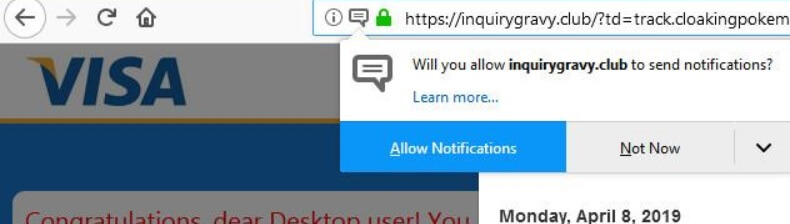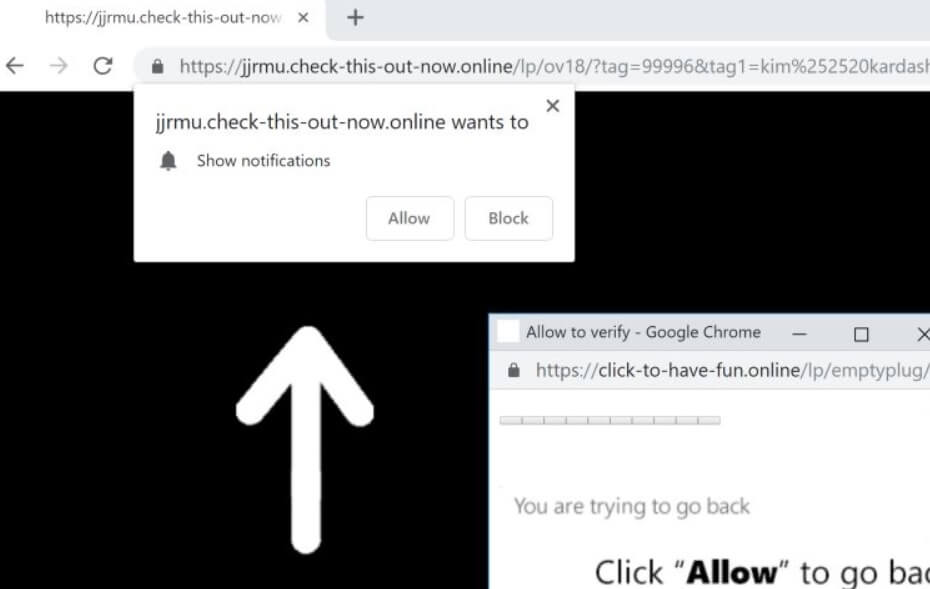
Remove Check-this-out-now.online Redirect
Check-this-out-now.online redirect can affect your browser. Check-this-out-now.online is a redirect, that will get inside your browser. Check-this-out-now.online will push redirects and pop-ads. Check-this-out-now.online is a malicious domain connected with redirecting URLs of websites containing spam, advertisements or even some sort…