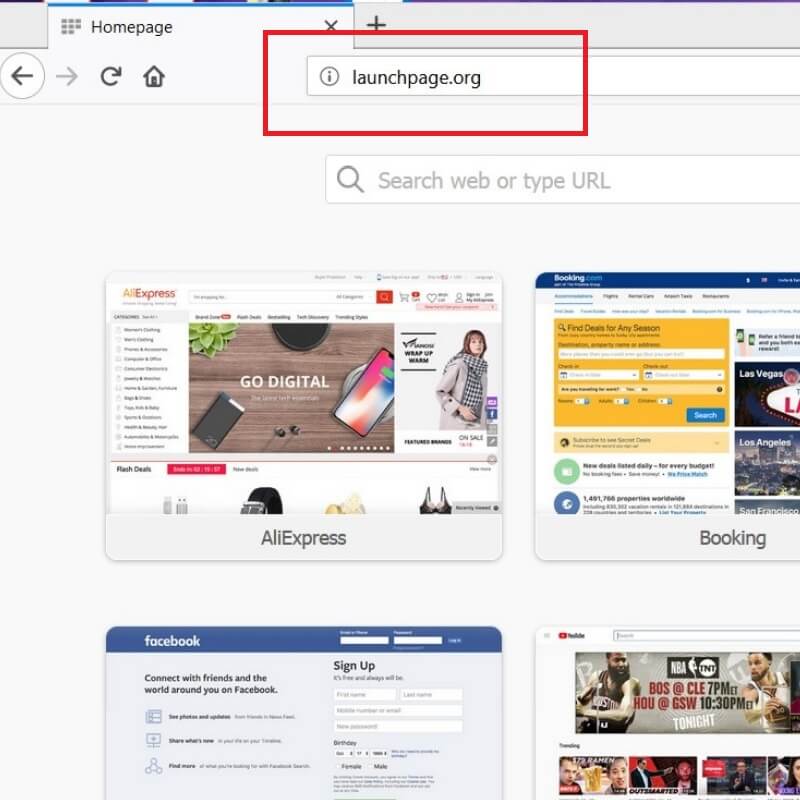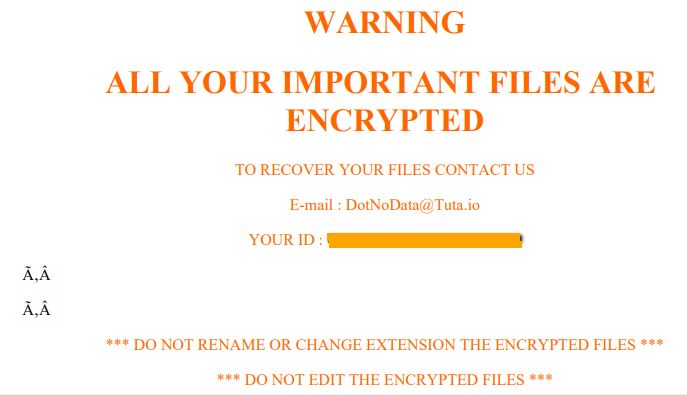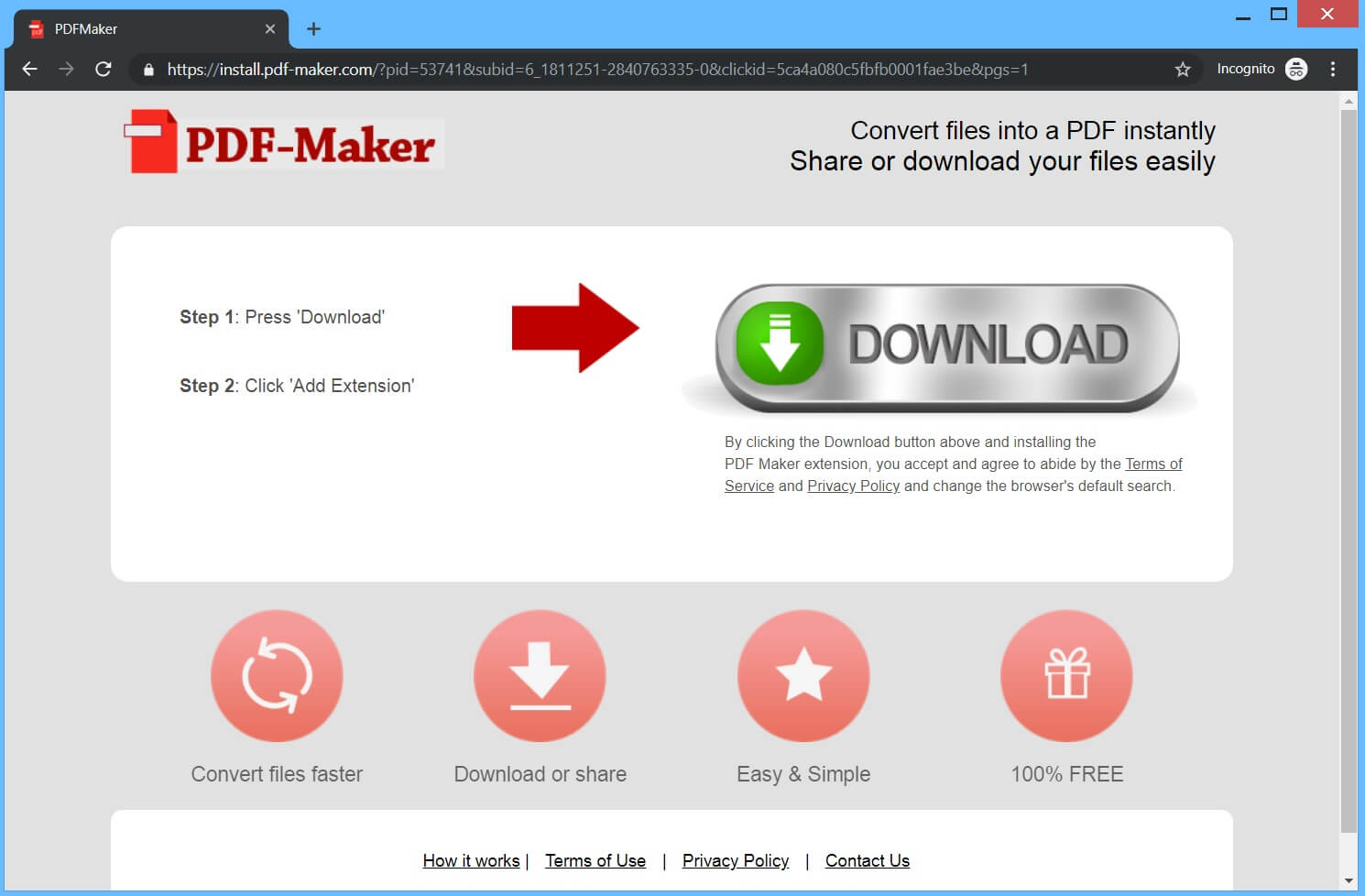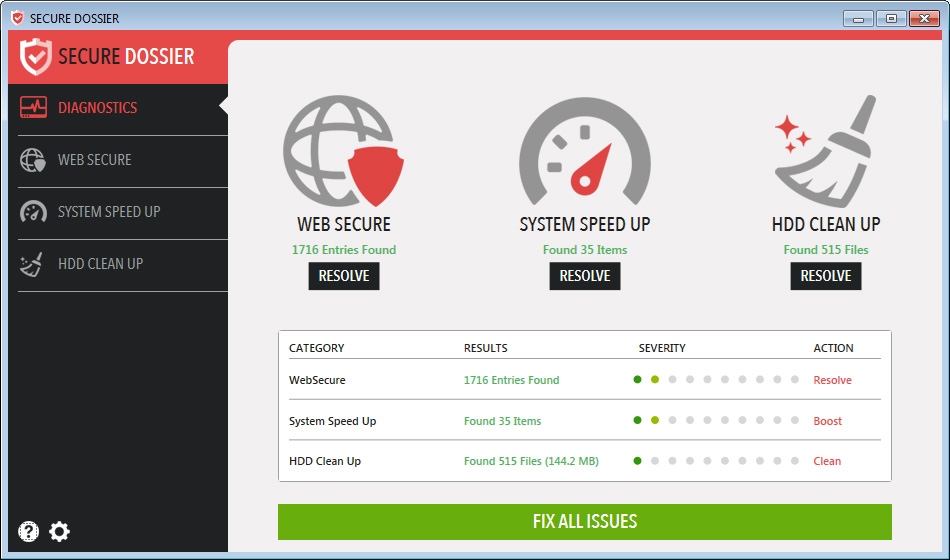
Remove Wajm.icu Redirect
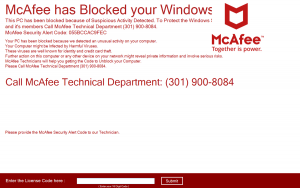
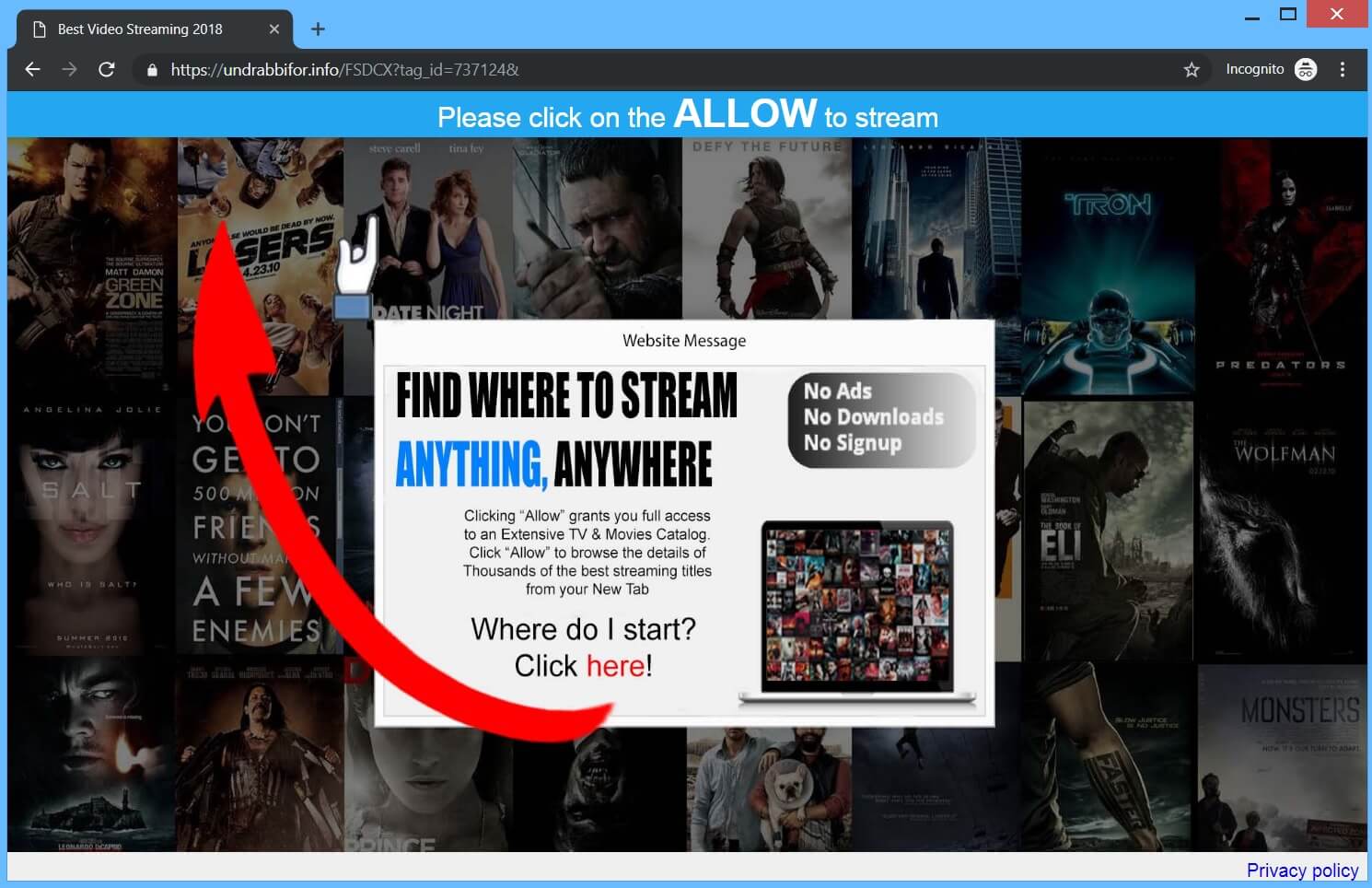
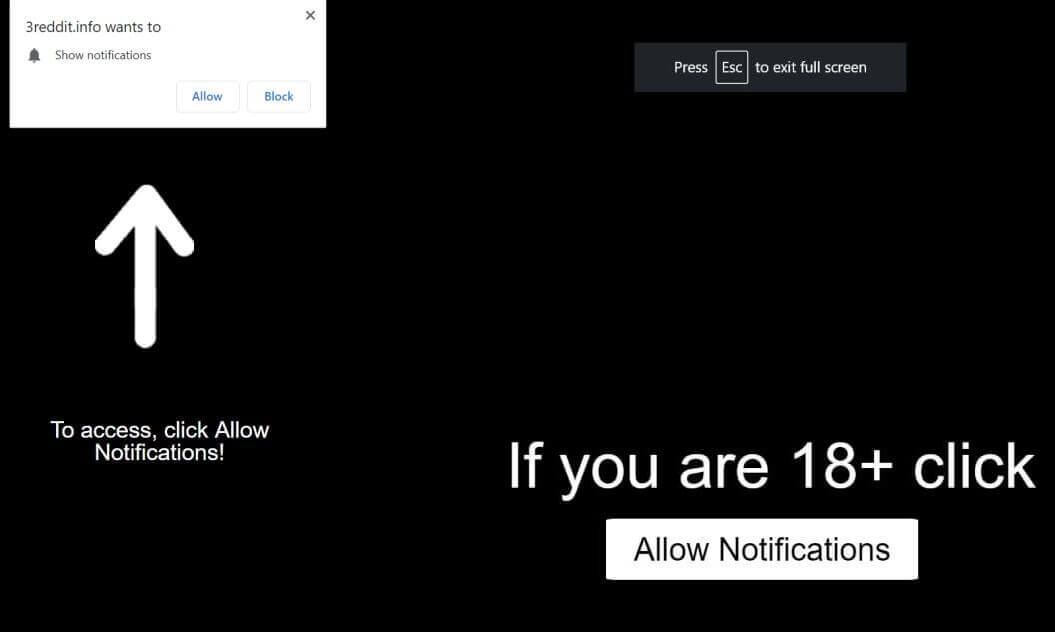
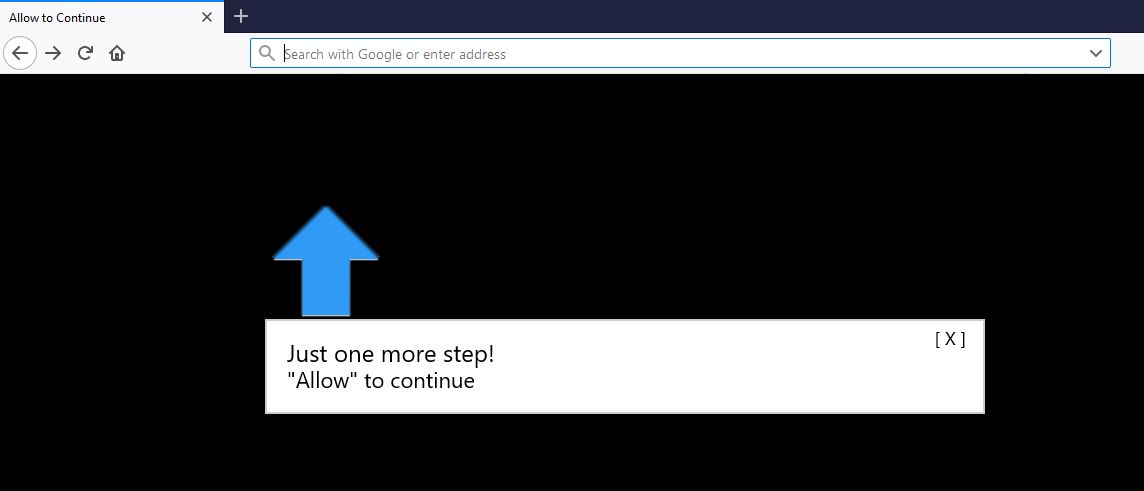
What is Wajm.icu redirect page? Which program causes Wajm.icu redirect redirects? How to remove the unwanted program, causing Wajm.icu redirect redirects from your computer? The Wajm.icu redirect is a new browser redirect and malware site which has been reported to…