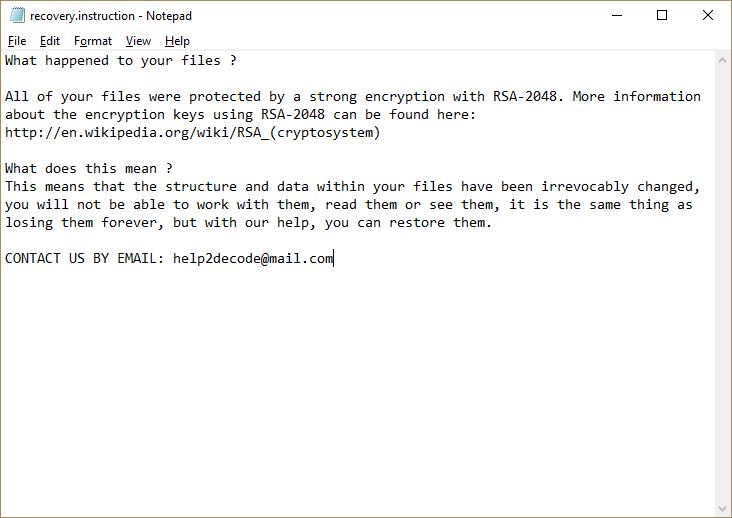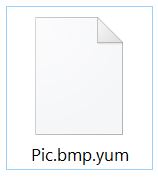
.yum Files Virus – How to Remove It
This article has been created to explain what is the .yum file ransomware and how you can effectively remove it from your computer. The .yum file ransomware is the type of virus whose main idea is to slither onto your…