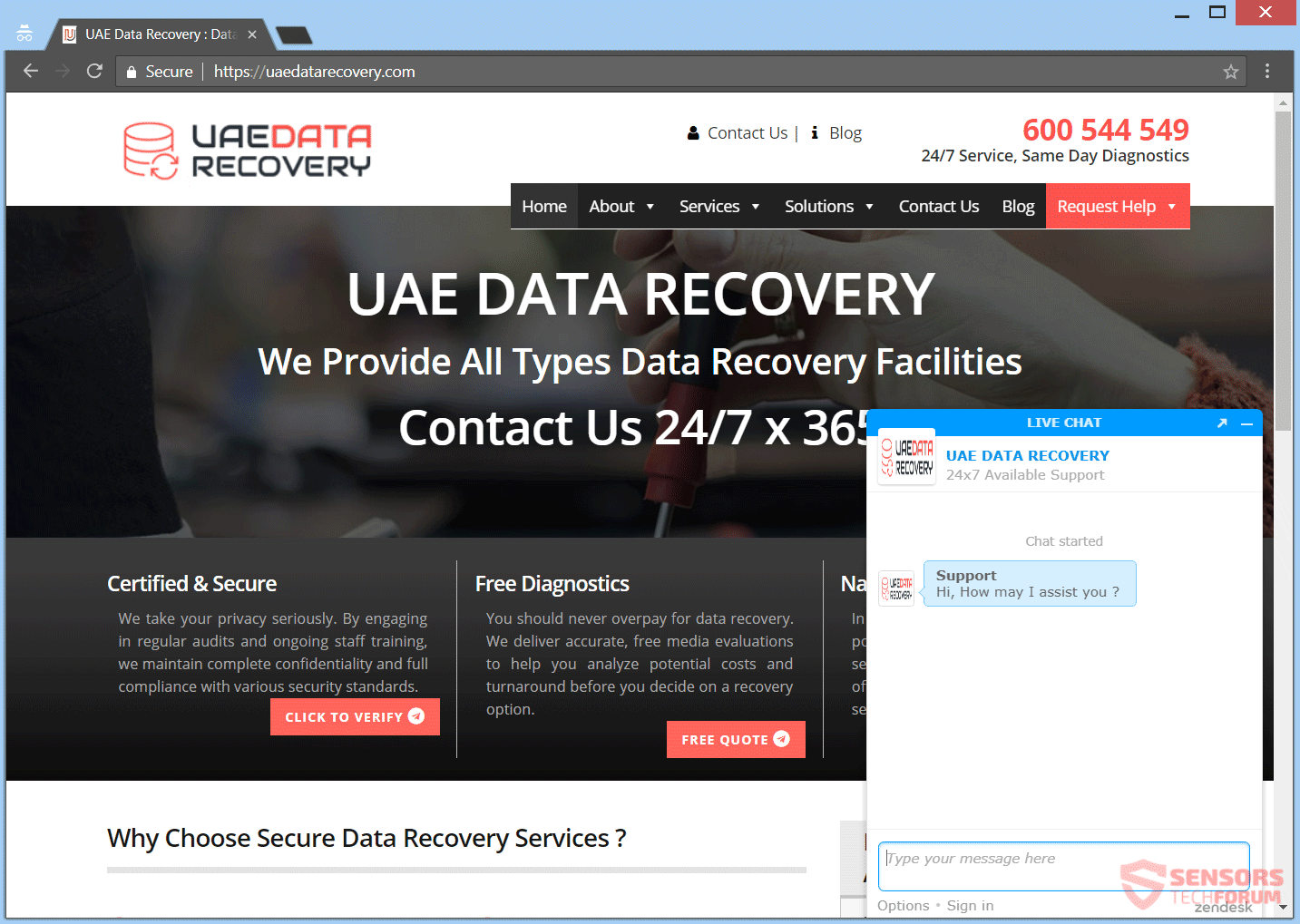
Remove UAEdatarecovery.com Scam
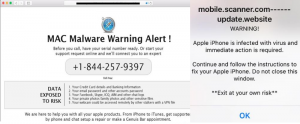
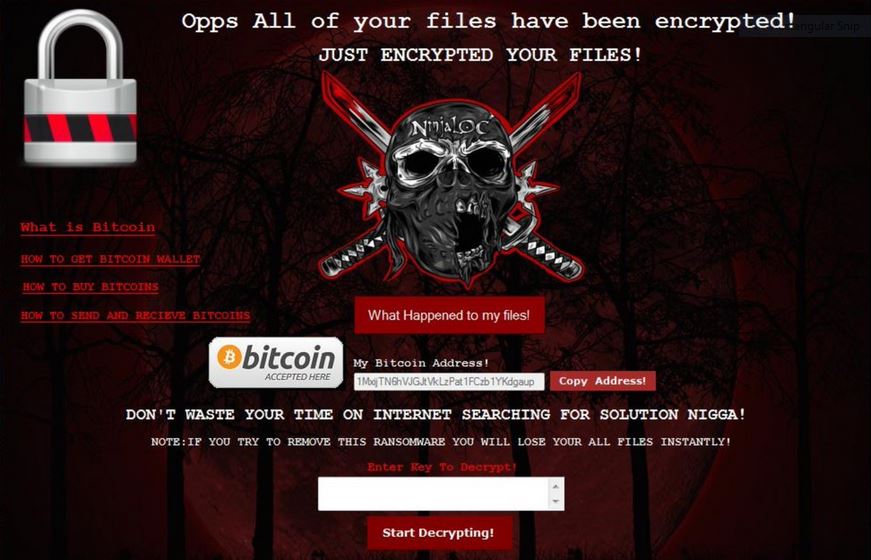
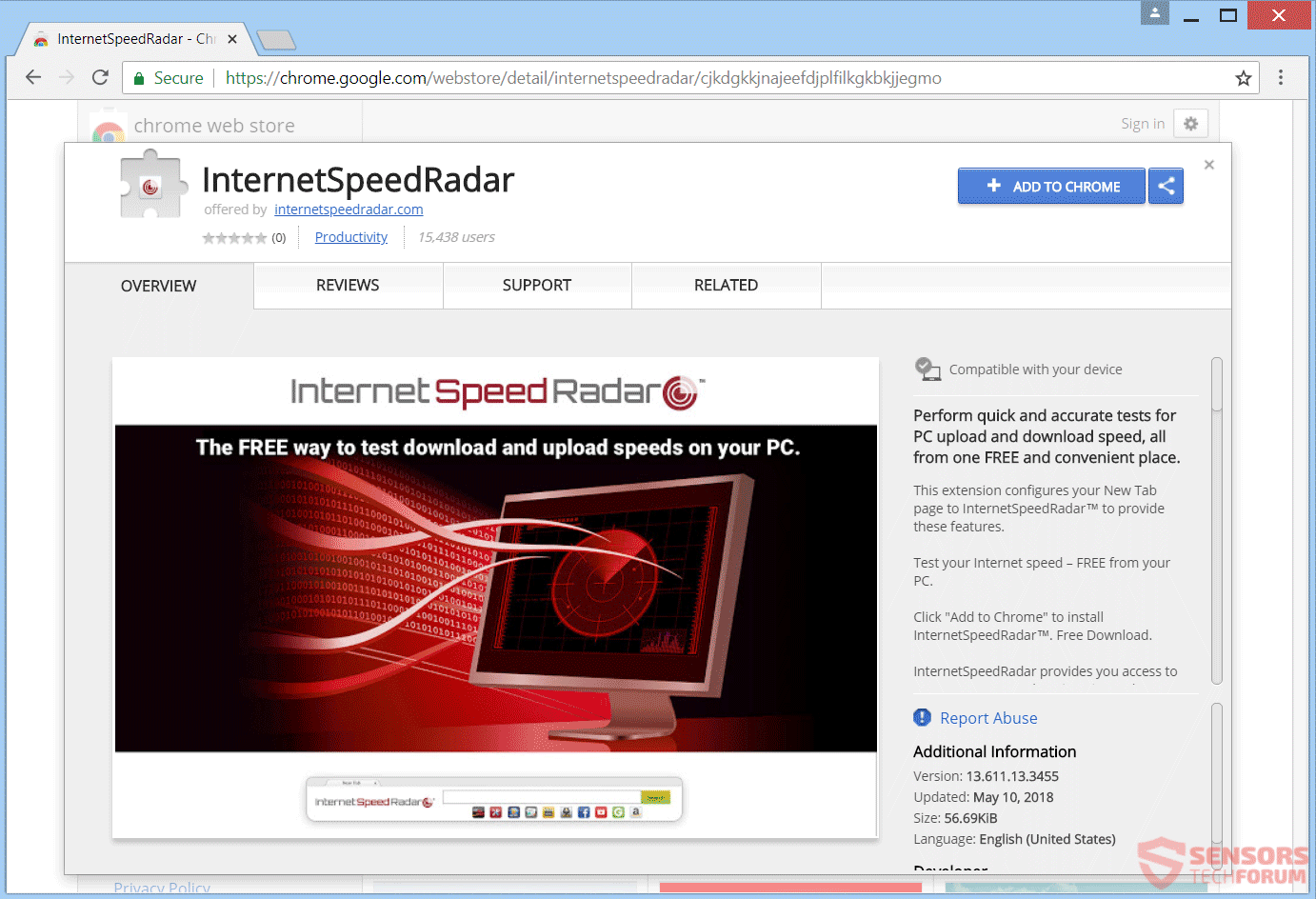
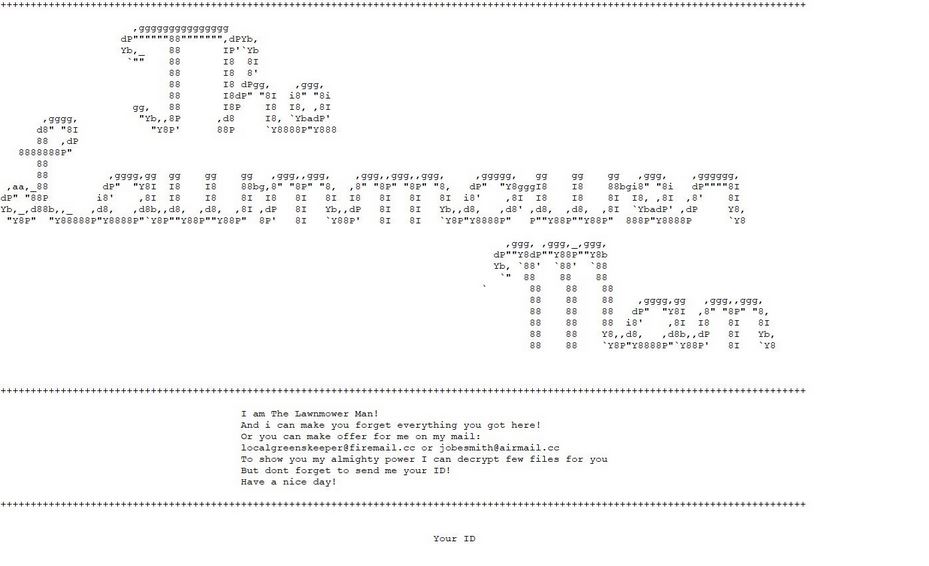
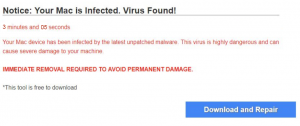
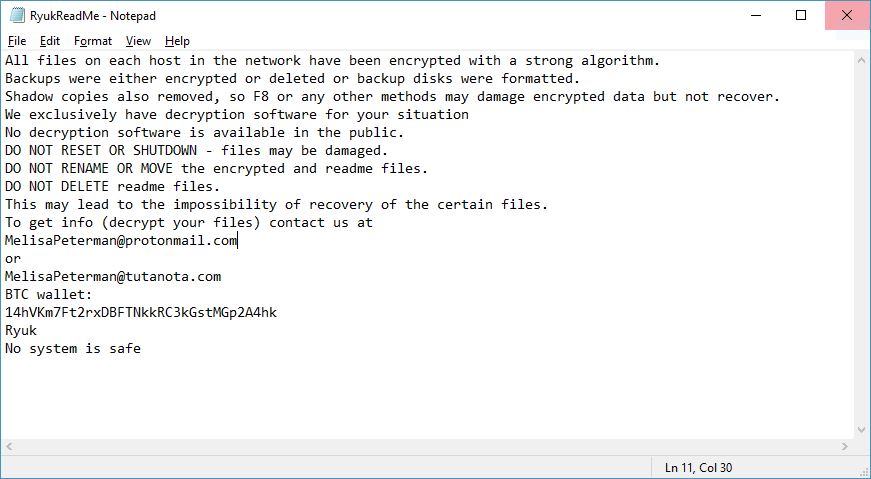
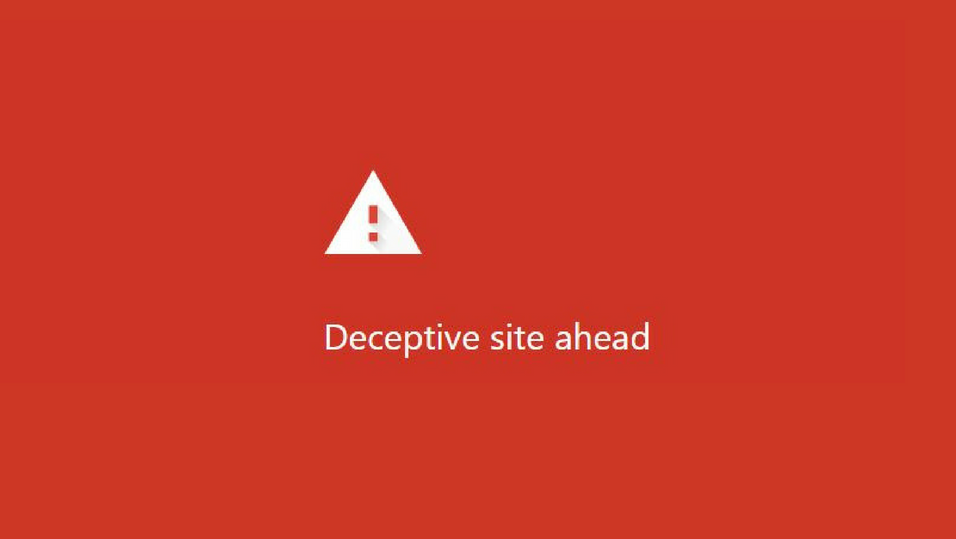
This article will help you remove UAEdatarecovery.com fully. Follow the tech support scam removal instructions provided at the end of this article. UAEdatarecovery.com is a website which is connected to a tech support scam and hosts it on that Web…