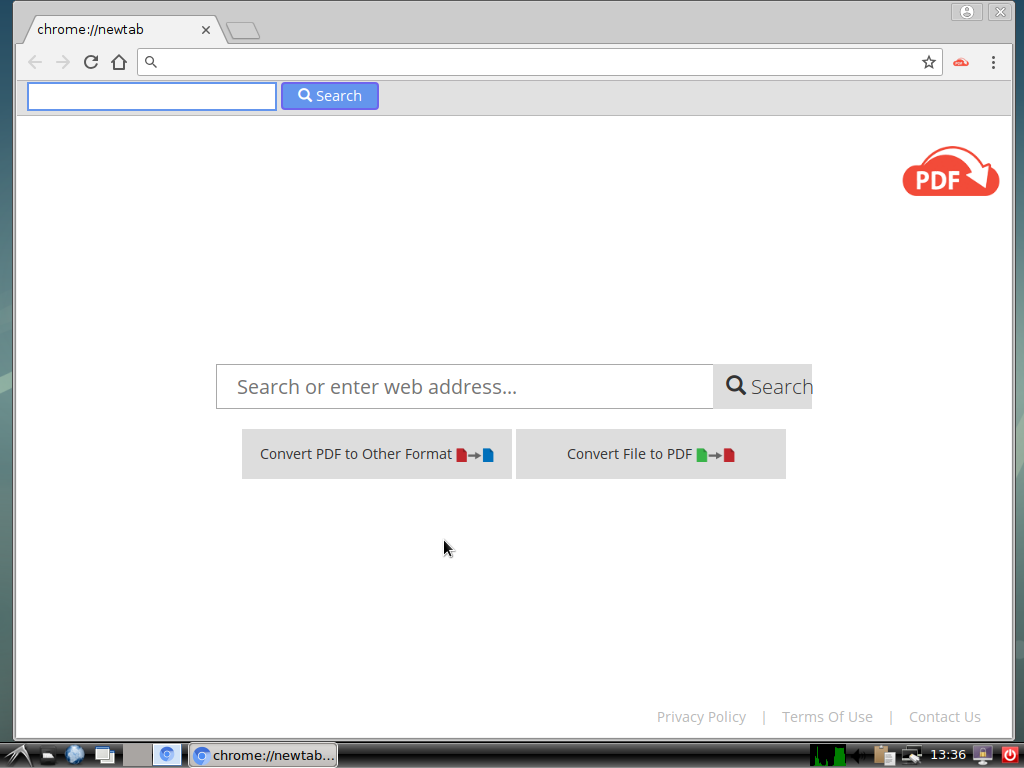
PDF Convert Tab Redirect Removal — How To Restore Your Browser
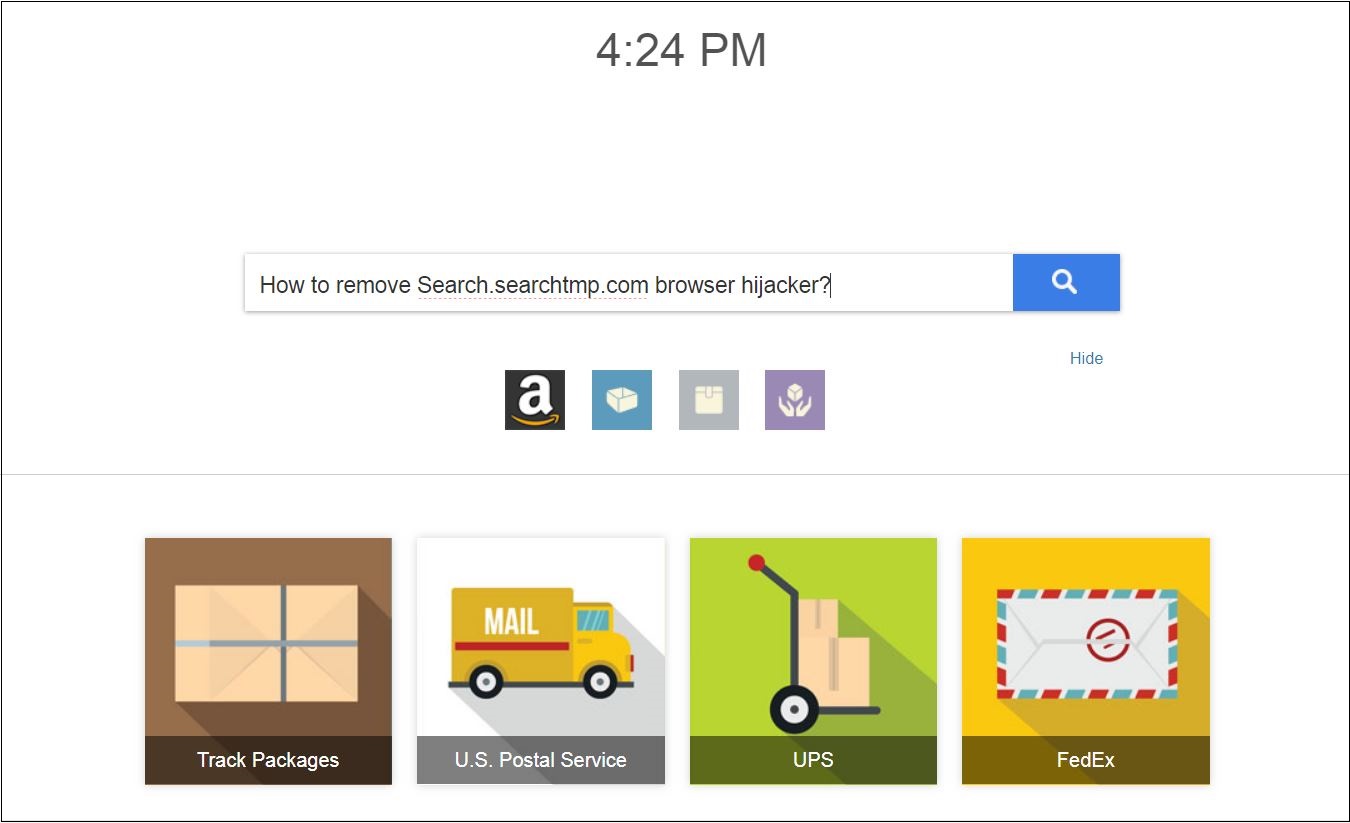
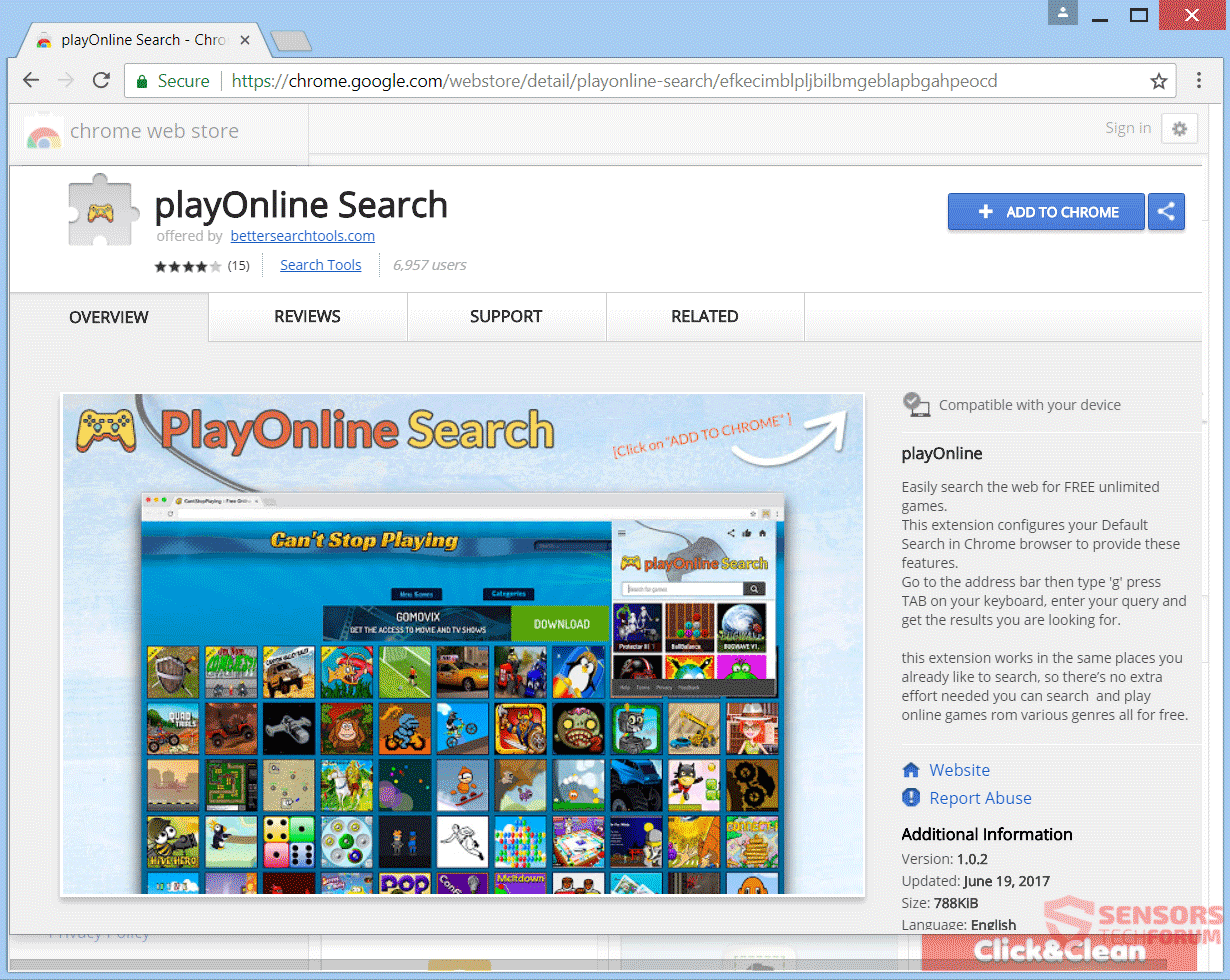
The article will help you to remove PDF Convert Tab fully. Follow the browser hijacker removal instructions given at the end of the article. The PDF Convert Tab redirect is a recently discovered browser plugin that can be used for…