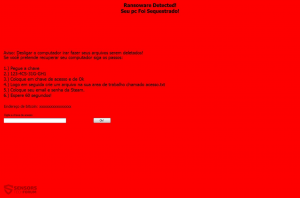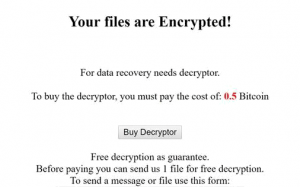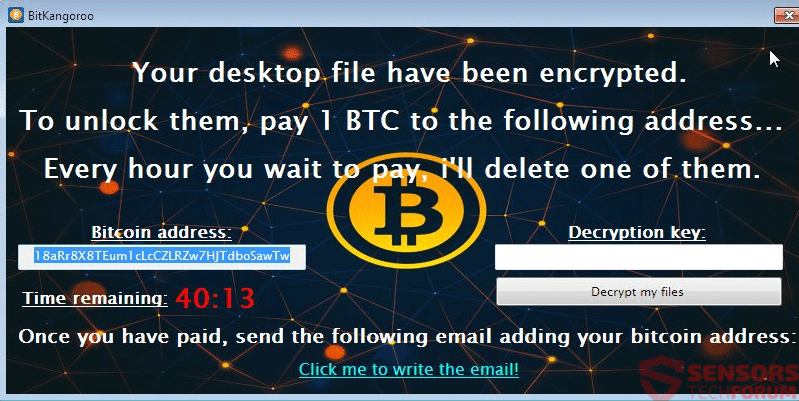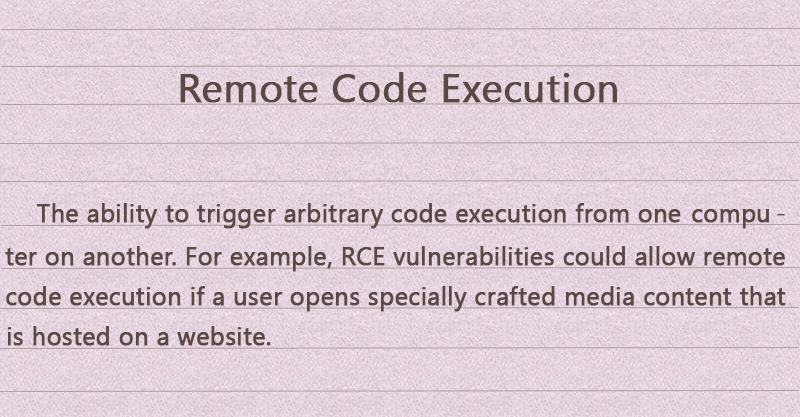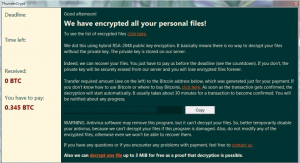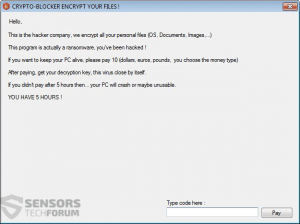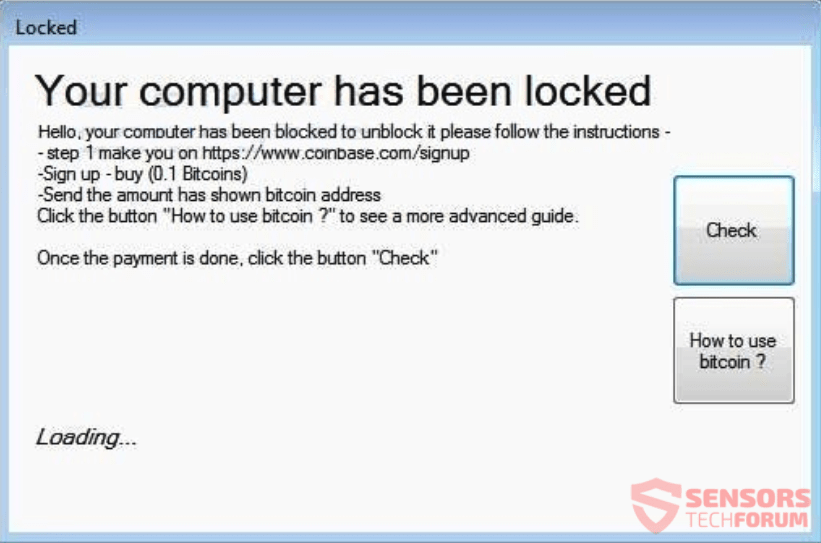
.UIWIX File Virus Restore Files
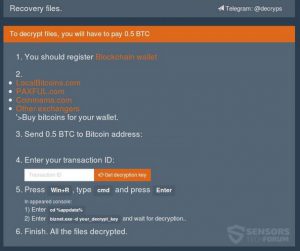
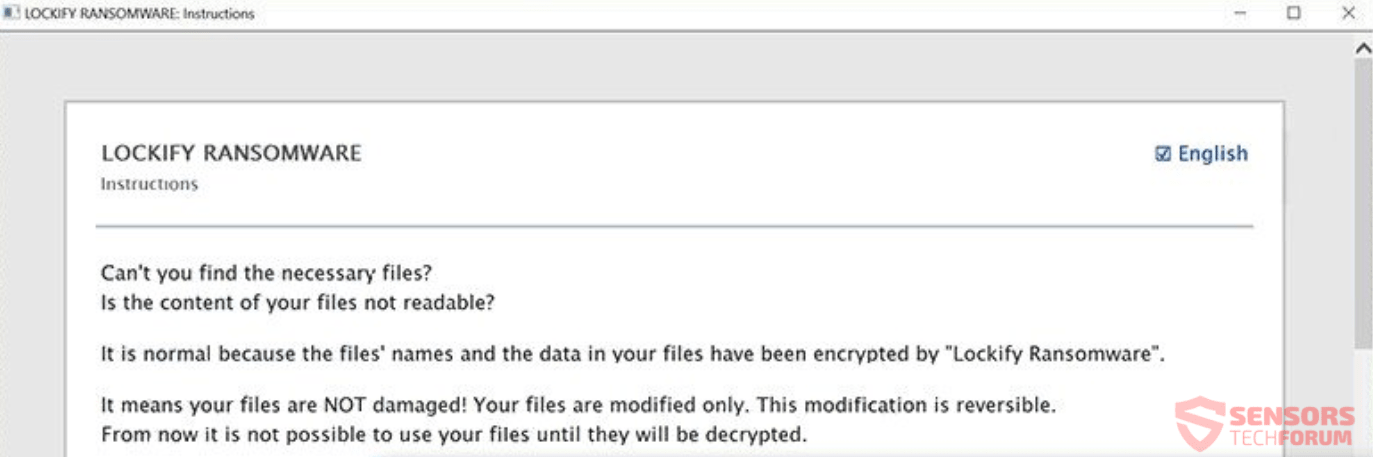
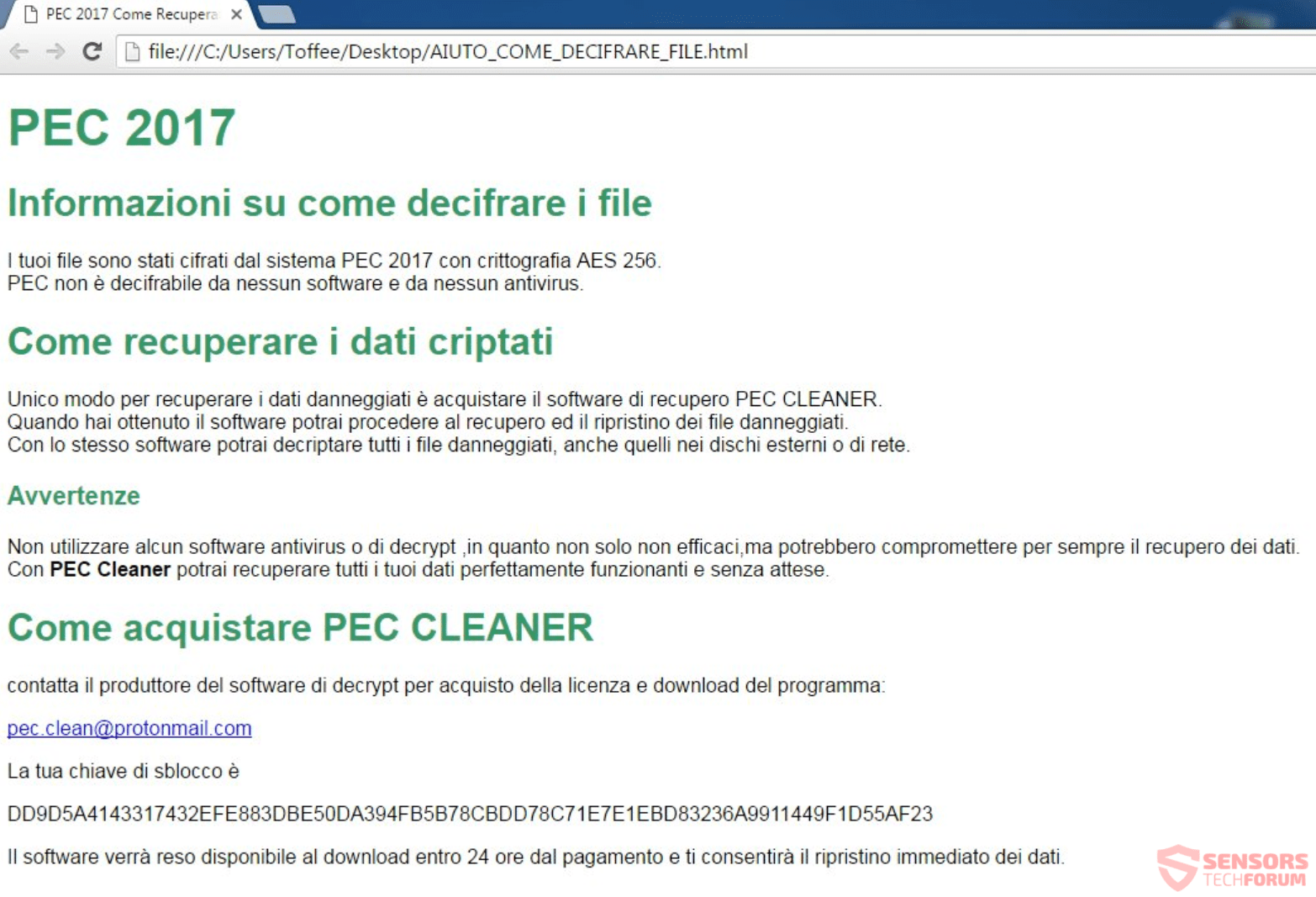
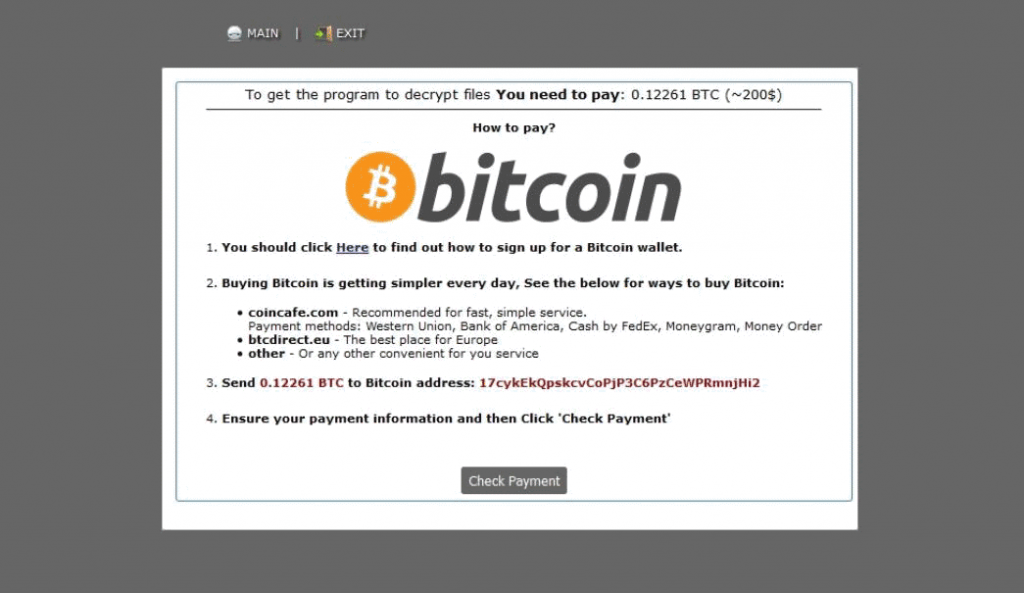
Article, designed to assist in how to remove .UIWIX ransomware infection from your computer and restore encrypted files. New ransomware infection has been detected at the beginning of May 2017 by malware researchers. The virus uses the .UIWIX file extension…