Mac Optimizer Adware “Virus” – How to Fully Remove It from Your PC
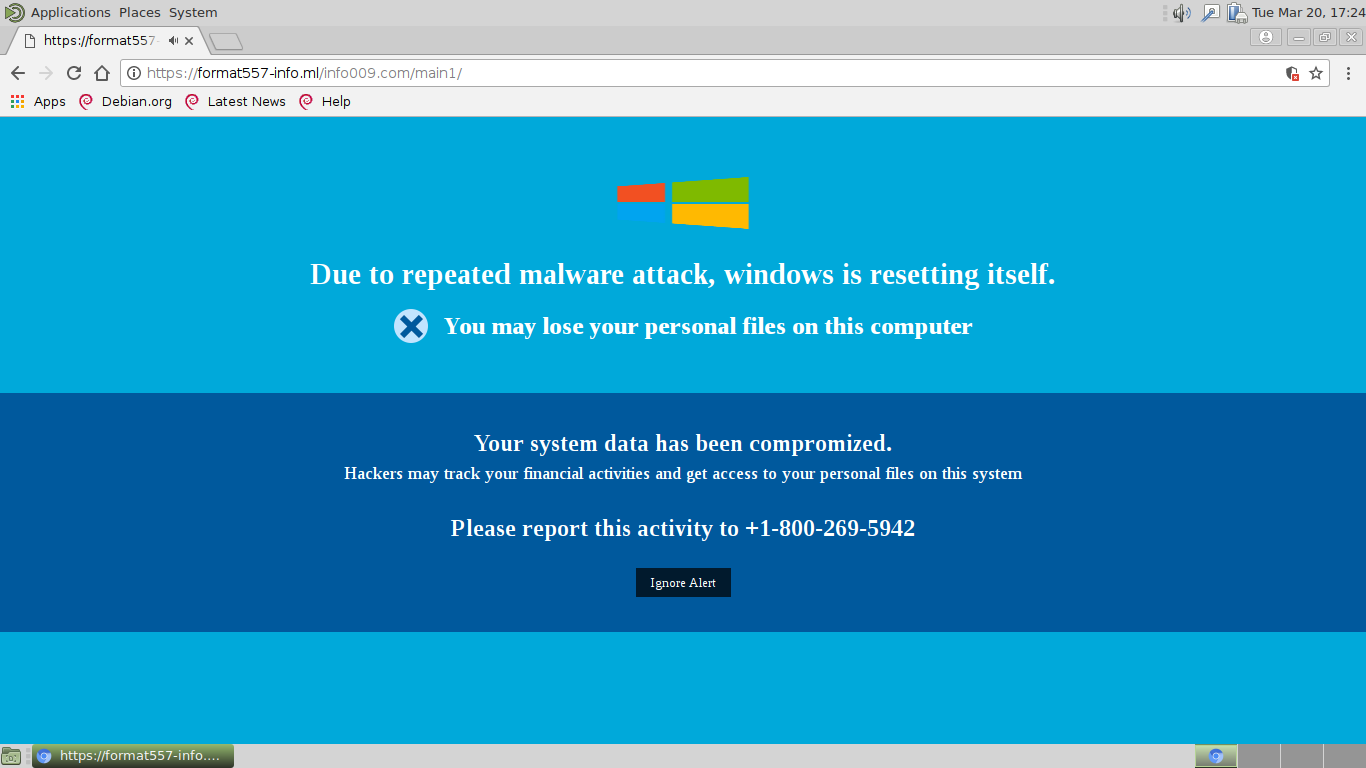
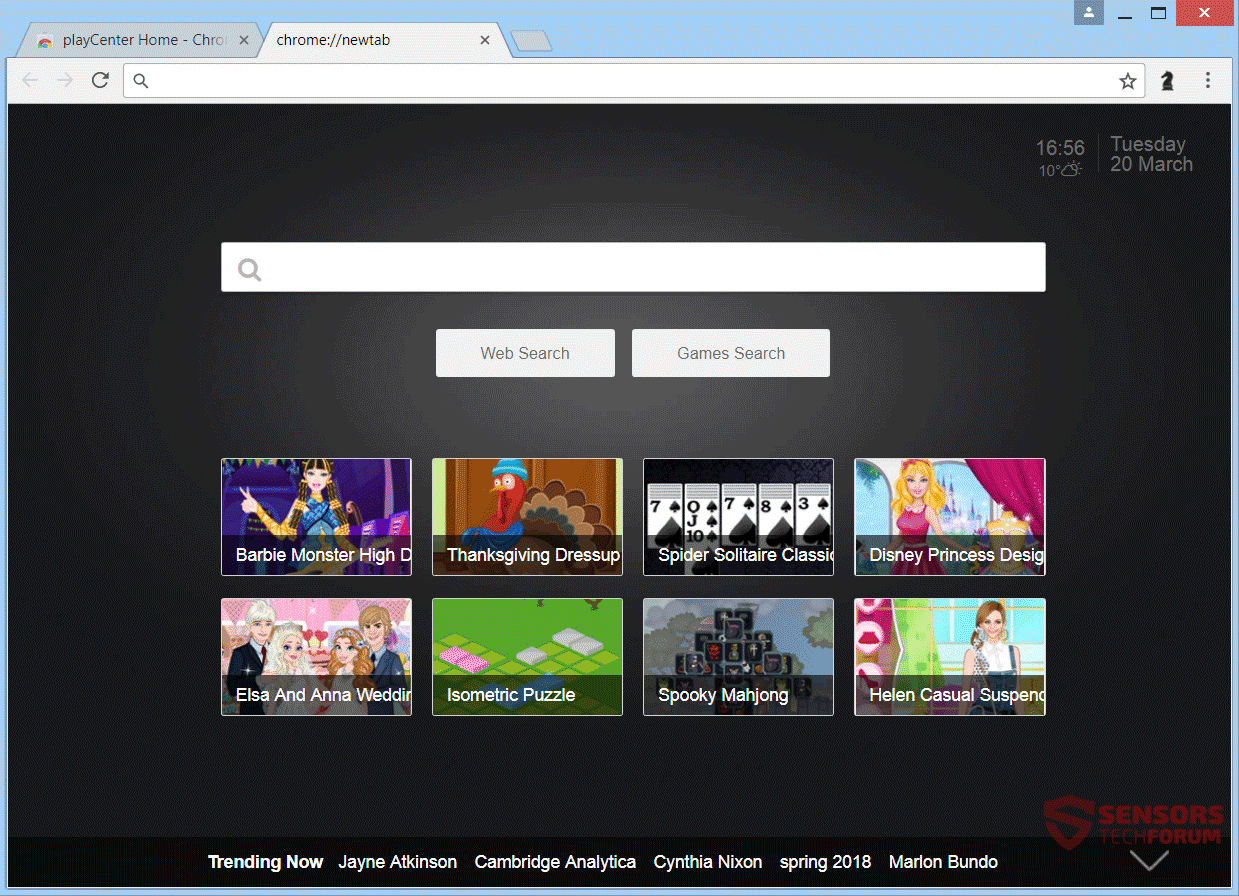
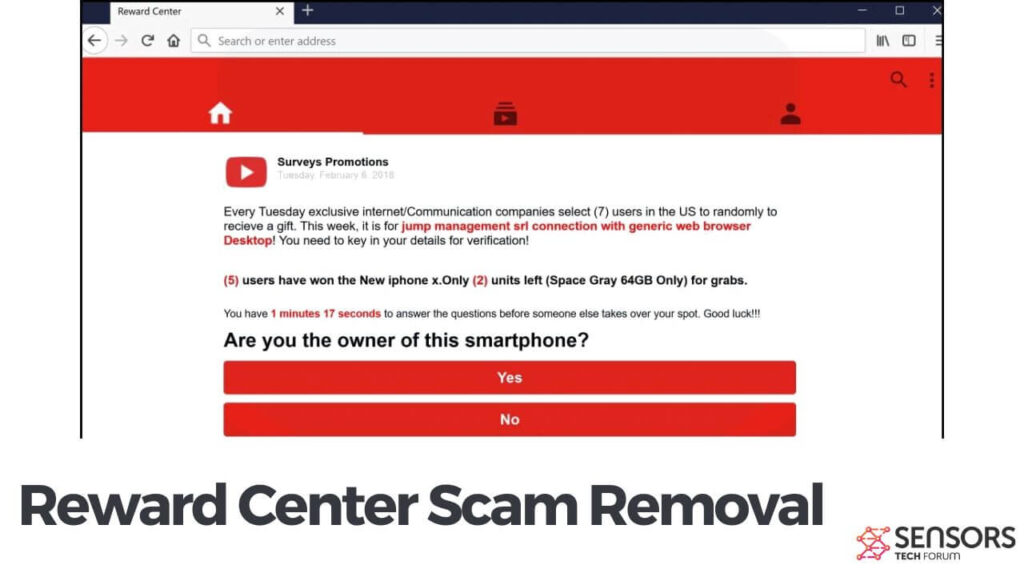
This article has been created in order to explain what exactly is Mac Optimizer and how to remove this unwanted program from your MacBook. Mac Optimizer is the type of software which you do not want on your computer. The…