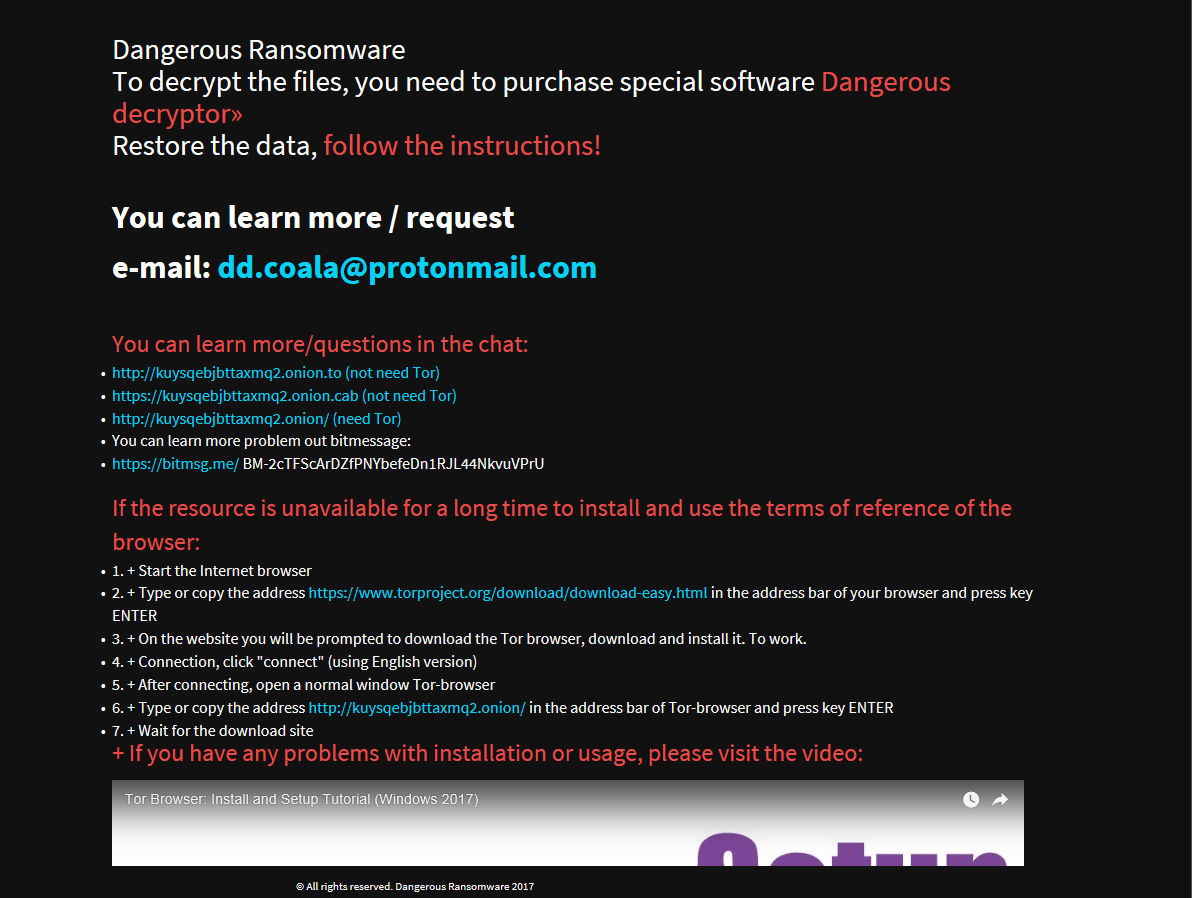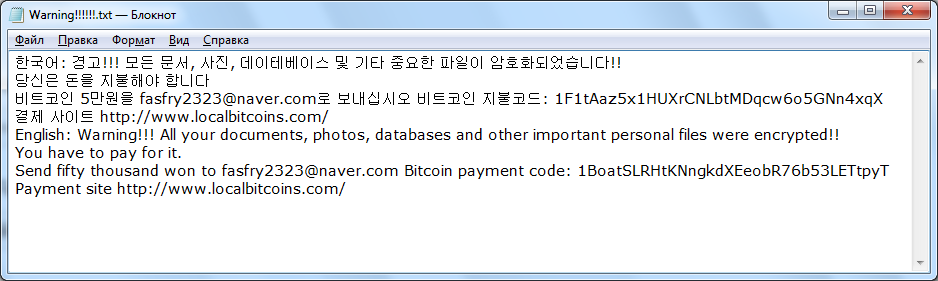
Digmine Facebook Messenger Miner Malware – How to Remove It
This article has been created to explain what exactly is the Digmine malware threat and how to remove it from your computer permanently. Malware has evolved dramatically especially with the latest cryptocurrency trend and new type of viruses that are…