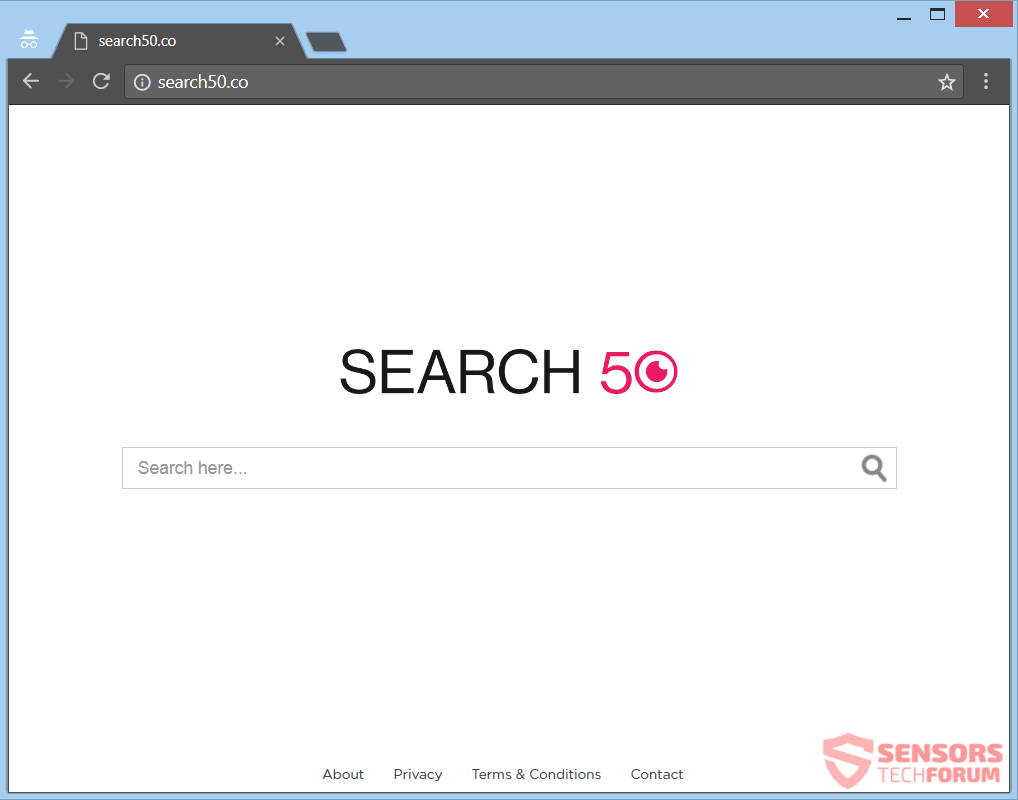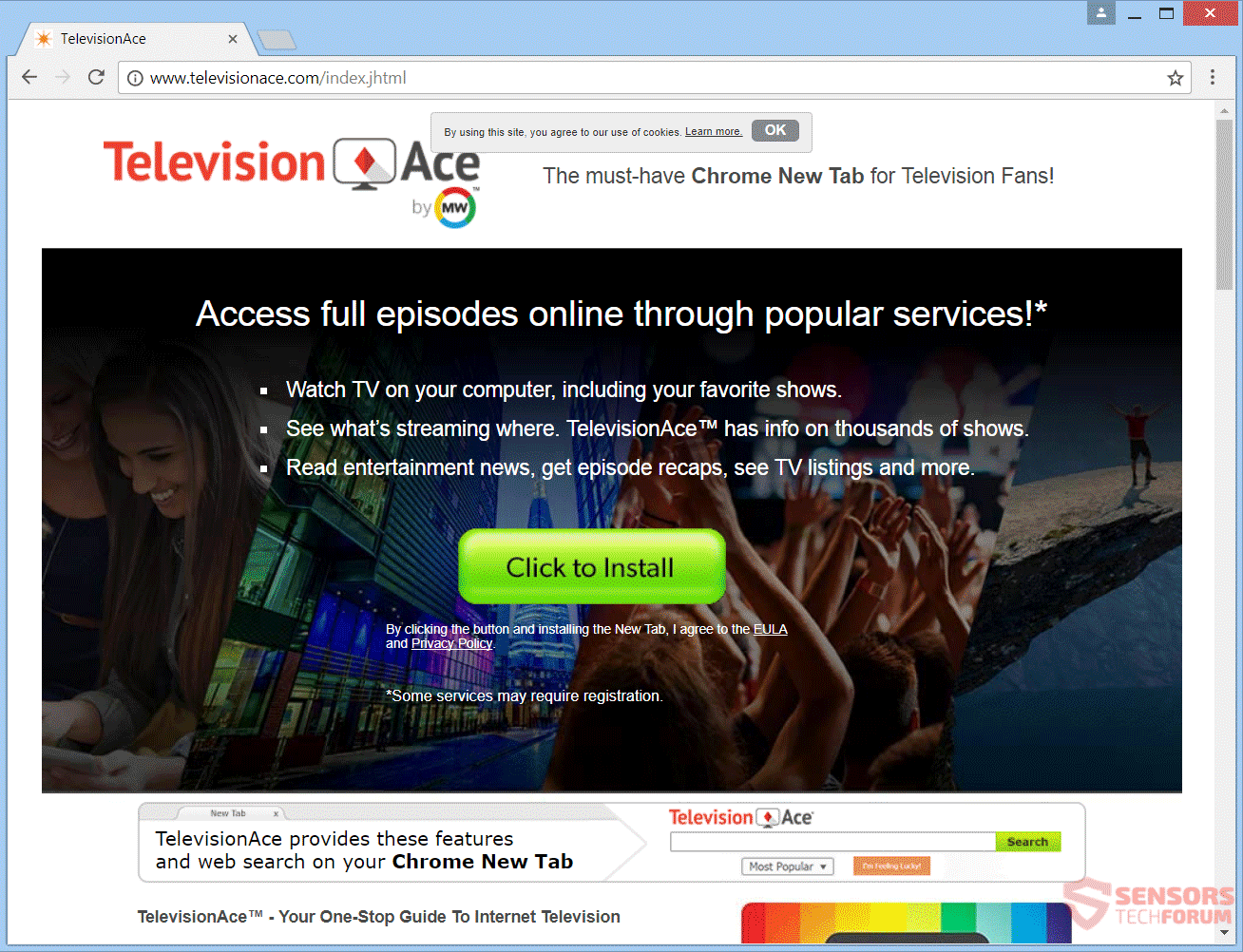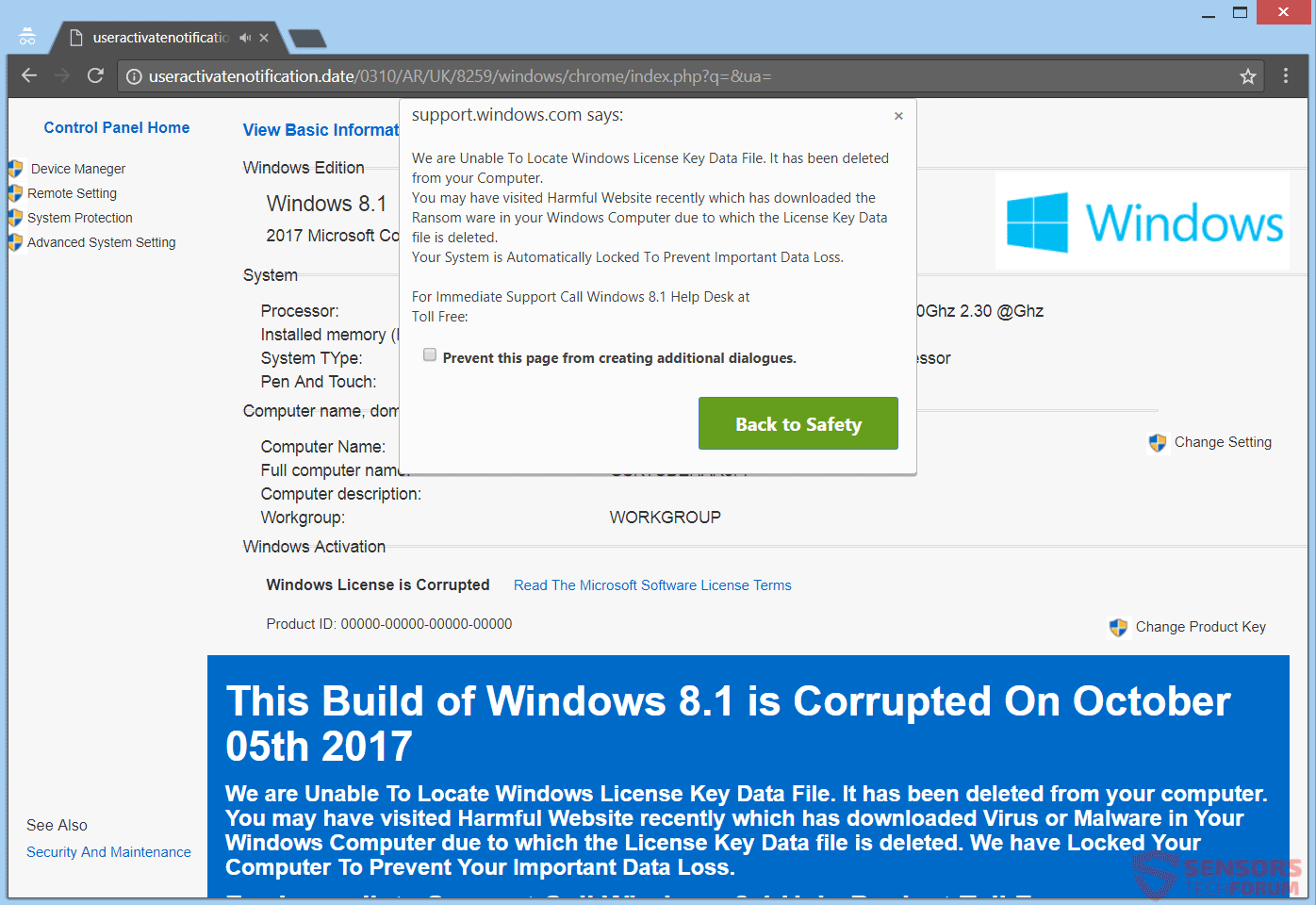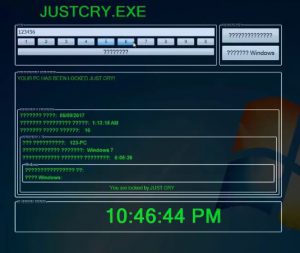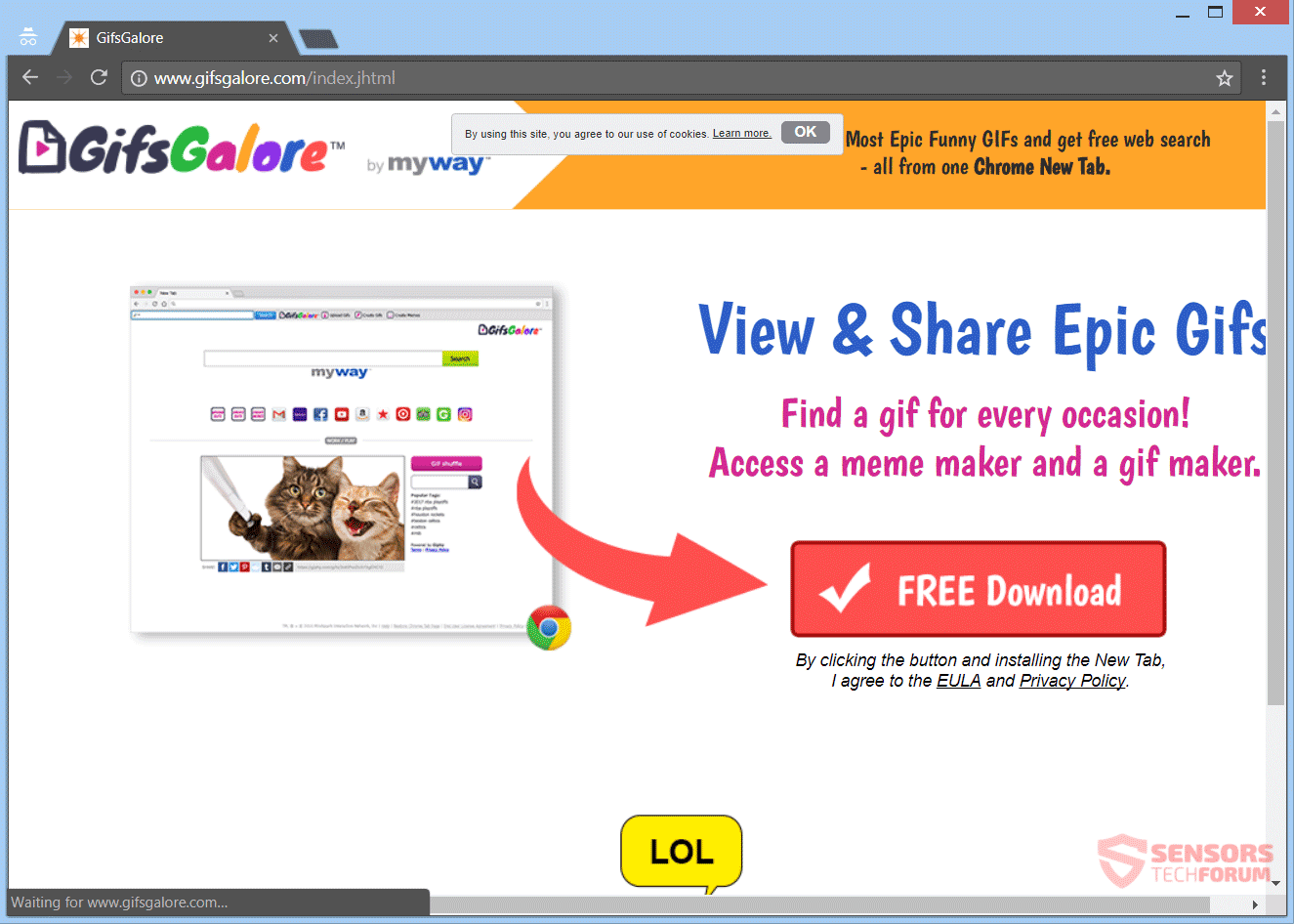
Apple Patch Remedies Critical High Sierra Vulnerability (CVE-2017-7149)
Apple released an emergency update that fixed a critical bug affecting the High Sierra operating system, specifically in the APFS volume management system. . According to security reports and the company a bug allowed the passwords to be revealed via…