.fmoon Files Virus – Remove MOON DECRYPTOR (+ Restore)
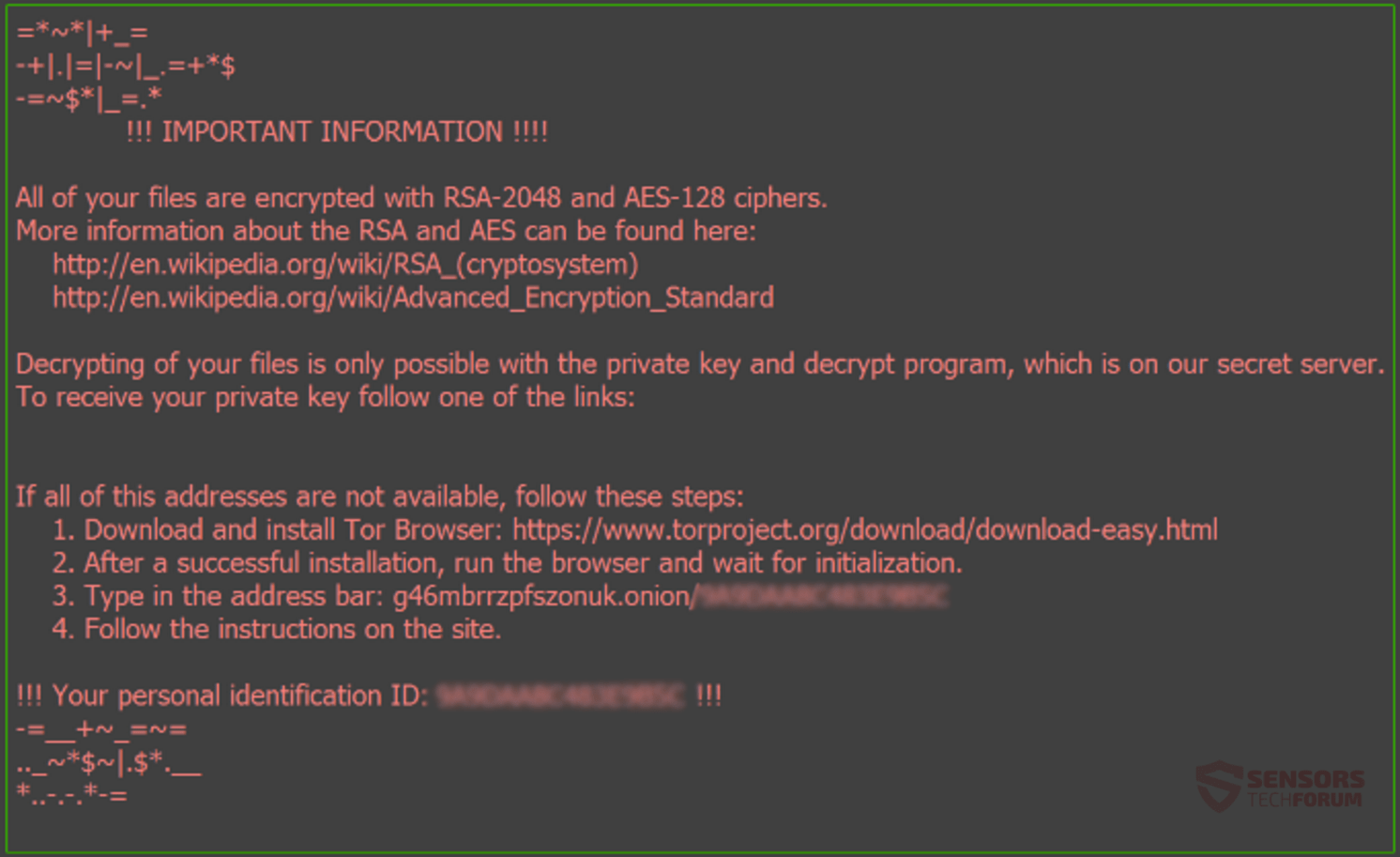
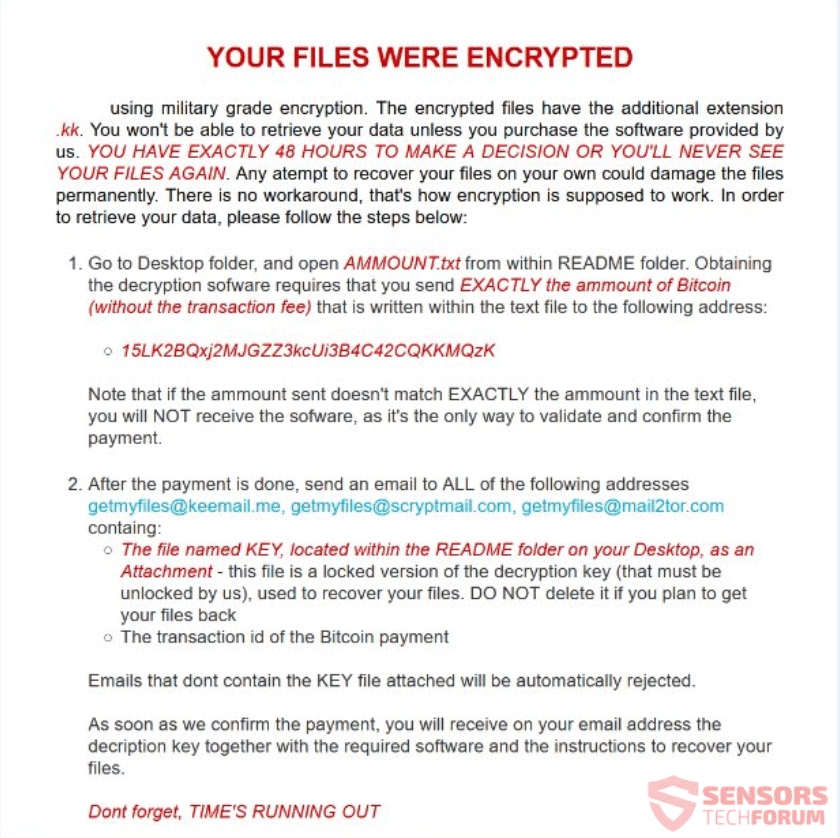
This article aims to help you remove the MOON DECRYPTOR ransomware virus from your computer and restore files that have been encrypted with the .fmoon file extension added. A new ransomware virus, calling itself MOON or MOON DECRYPTOR has been…


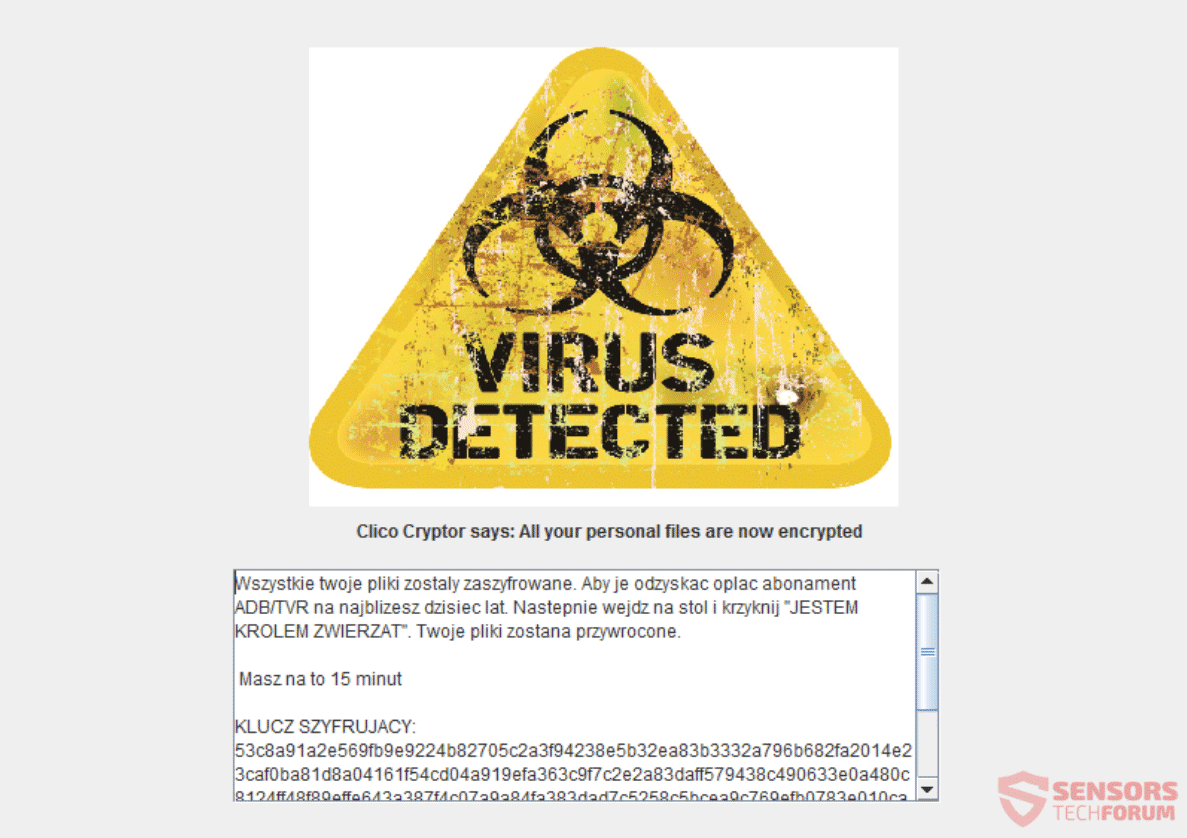

![Zalupaid Virus Removal – Restore .Encrypted[Payfordecrypt@protonmail.com] Files](https://cdn.sensorstechforum.com/wp-content/uploads/2017/08/stf-zalupaid-virus-zalupka-ransomware-encryptedPayfordecrypt@protonmail.com-files.png)