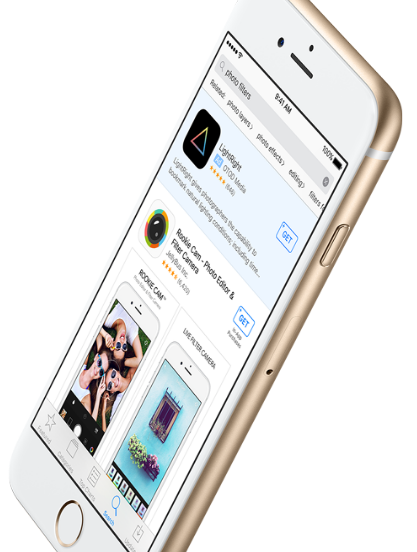
iPhone Users Will Now See Search Ads
If you’re an iPhone or iPad user (and an Apple follower), you may want to know that owners of the devices will soon see ads when using the Search option in the App store. The ads will appear at the…

If you’re an iPhone or iPad user (and an Apple follower), you may want to know that owners of the devices will soon see ads when using the Search option in the App store. The ads will appear at the…
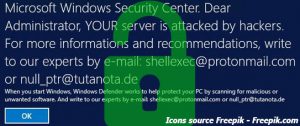
Ransomware virus that has been specifically designed to attack systems running OS’s for servers, like the Windows Server 2012 has been detected to cause infections and encrypt files on compromised server. ESG malware researchers have reported that this may be…

News broke out that the same gang which is behind the devastating Dridex banking malware was also reported to be behind other very famous viruses as well. The gang has initially begun to distribute CryptoWall, but this was just the…
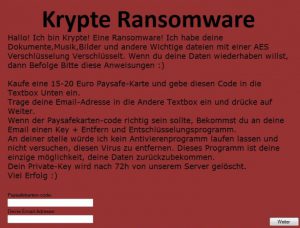
New version of the Razy ransomware virus, known by the name Krypte has been released and has begun encrypting files with what appears to be an AES cipher. The virus has been created exclusively for German users. The virus aims…
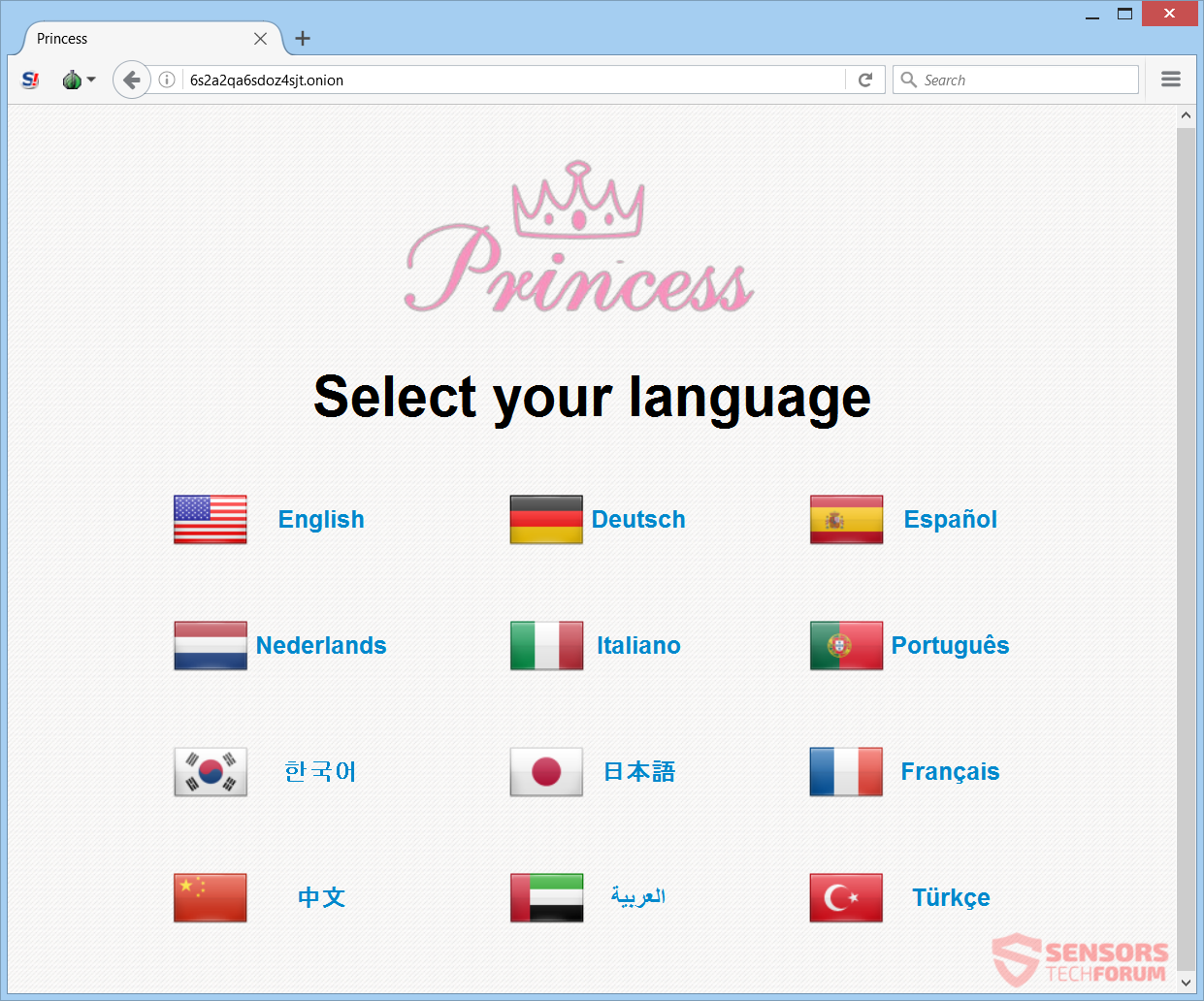
Princess Locker virus has recently been discovered by the malware researcher Michael Gillespie. The virus looks very much alike the Alma Locker ransomware. The methods of infection are still unknown, but since this could be a variant of Alma, the…

With the drone revolution aligned with the IoT (Internet of Things) more concerns arise regarding the security and proper usage of drones. The main scares to which drones are related are connected primary with collisions and crashes. But there are…

Locky ransomware continues to evolve. The new extension .ODIN is placed as an appendix to the original file extension names after they get encrypted. The cryptovirus seeks to encrypt nearly 400 different file types. As the ransom note states, data…

As with any other software which is coded by humans, there are also vulnerabilities in Apple’s latest operating system which is now available for an upgrade on the iPhone 7, iPhone 7 plus, iPhone 6, iPhone 6s, iPhone SE and…

Have you been wondering which today’s most prevalent cybercrime threats are? Europol has just released a vast, 72-page report called the Internet Organized Crime Threat Assessment which gives quite a detailed answer. Crime-as-a-Service According to Europol, the malware market has…

Google has just released two new tools for developers with the purpose to shield web domains from XSS scripting vulnerabilities. XSS, or cross-site scripting, is a common issue in cybersecurity. An XSS-powered attack takes place when malicious actors implement malicious…
Malware going by the name of BASHLITE has been created to cause a DDoS (Denial of Service) type of attacks by taking advantage of IoT devices, researchers report. This is not the first IoT malware that has been detected, but…

Changes in the exploit kit market indicate that currently RIG is the most deployed EK service. Apparently, RIG is taking the place of Neutrino. Since the death of Angler, the two exploit kits have been battling for the lead positon…
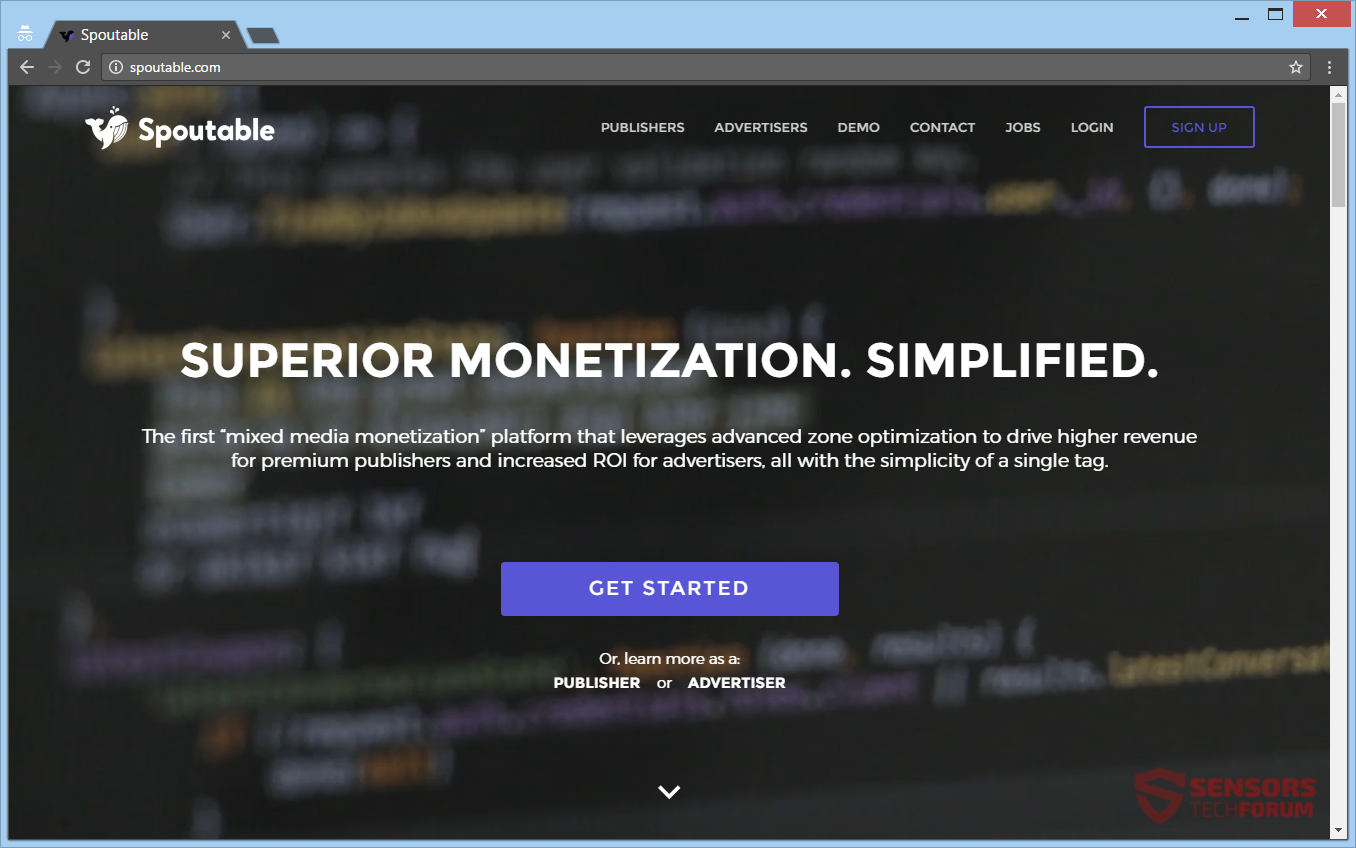
Spoutable.com is a website of a monetization platform. The website generates lots of advertisements and can redirect you to other websites and scams, so it is considered adware. The owners of such websites make some of their income from the…
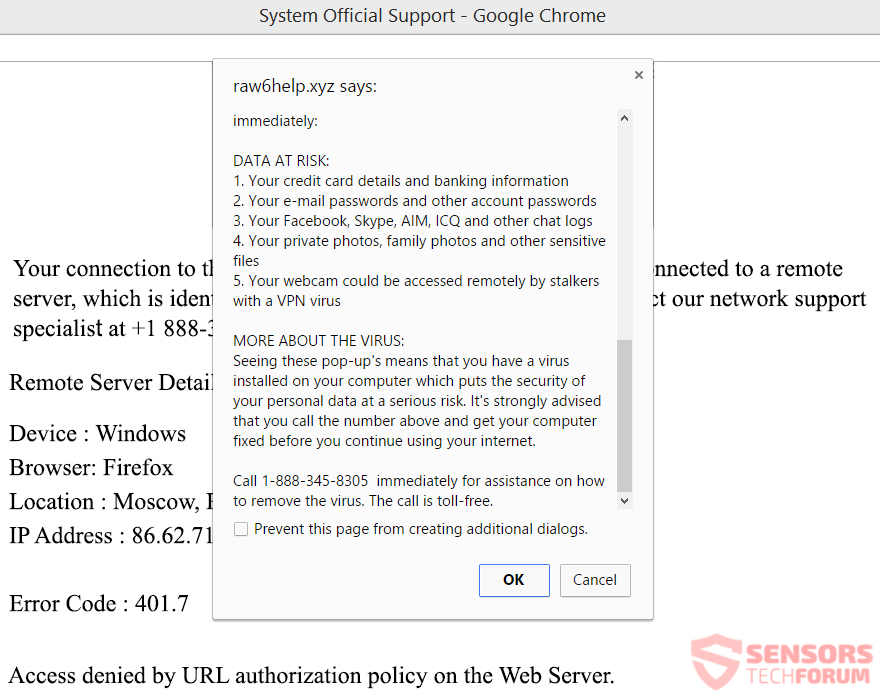
Raw6help.xyz is a website that is directly involved with a tech support scam. The site uses 1-888-345-8305 for the contact phone number. People that run this scam might call you from that number. You can experience endless redirects while browsing…

Virlock ransomware has apparently been updated and is now capable of propagating itself via the cloud. Hence, the ransomware can be spread negligently from one infected to another, eventually file-locking an entire network. This update seen in the code of…
OVH is a hosting company that has apparently been a victim of the biggest DDoS attack ever registered. The attack is said to have surpassed the DDoS on KrebsOnSecurity. A tweet by the company’s CTO, Octave Klaba, reveals that “you…
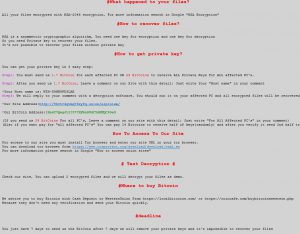
New variant of the Samas ransomware has been reported to demand the sum of 1.7 bitcoins after it uses RSA encryption to encipher files of infected computers, adding the .iloveworld file extension to them. The ransomware then drops a PLEASE_READ_FOR_DECRYPT_FILES_{number}.html…
Komplex is, according to security researchers at Palo Alto Networks, a new Trojan for Mac OS X, which is believed to be linked to the activities of Sofacy (also known as APT28, Pawn Storm, Fancy Bear, and Sednit), a Russian…

Android devices have become increasingly more secure and this is all fine and well, but what is the sense in malware when apps can request from users to accept almost insane permissions over the phone. The situation with some apps…
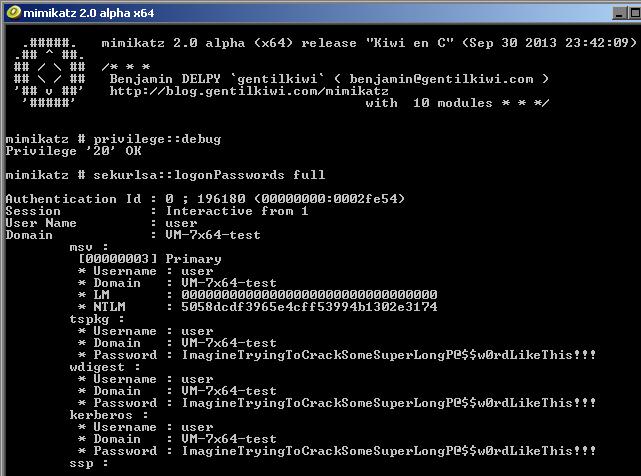
Windows Defender Application Guard for Microsoft Edge is Microsoft’s latest attempt to improve the security of its browser and respectively Windows 10. The new addition will run Edge in a lightweight virtual machine. Shortly said, the application is powered by…