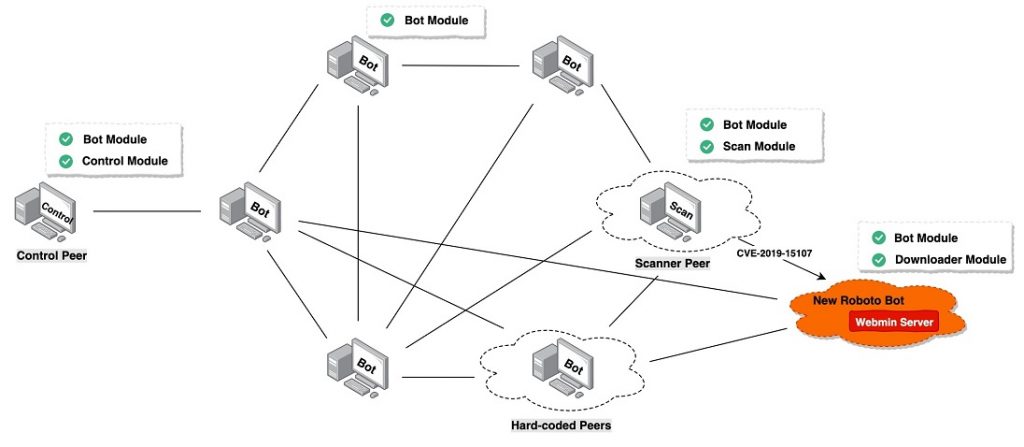
There’s a new botnet currently targeting Linux servers which are running vulnerable Webmin applications. The botnet has been called Roboto.
Netlab researchers were capable of capturing the Downloader and Bot modules of the botnet, and they believe that it also has a vulnerability scanning module and a P2P (peer-to-peer) control module.
Roboto was first observed in the summer, and its appearance is associated with the Webmin vulnerability, known as CVE-2019-15107. In August, it became evident that Webmin, a web-based application for system administrators of Unix-based systems (Linux, FreeBSD, or OpenBSD servers), contains a backdoor that could allow remote attackers to execute malicious commands with root privileges. A compromised system could later be used to navigate further attacks against the systems managed through Webmin.
Since CVE-2019-15107 is easy to exploit and affects a large number of systems, attacks based on it started shortly after the flaw was disclosed. Apparently, one of the first attacks based on this vulnerability was carried out by the Roboto botnet. The botnet has been targeting Webmin servers for the past three months, which is not surprising. Netlab security researchers say that the purpose of the botnet’s operators has been expansion and sophistication.
Roboto Botnet’s Functionalities
Netlab says that the botnet supports 7 primary functions, including reverse shell, self-uninstalling, collecting process network information and bot information, executing system commands, running encrypted files specified in URLs, performing DDoS attacks. However, that’s not all. The botnet also utilizes Curve25519, Ed25519, TEA, SHA256, HMAC-SHA256 and other algorithms “to ensure the integrity and security of its components and P2P network, create the corresponding Linux self-starting script based on the target system, and disguise its own files and processes name to gain persistence control.”
Even though Roboto has a DDoS functionality, it is not its main goal, and the researchers are still figuring out the botnet’s true purpose.
As for the peer-to-peer (P2P) structure, it is something rarely seen in such botnets. The only botnets that used this structure are Hajime and Hide’N’Seek. Initially discovered in October 2016, Hajime used unsecured devices with open Telnet ports and default passwords, and shared some similarities with Mirai. However, the main difference to Mirai is that Hajime was built on a peer-to-peer network, whereas Mirai used hardcoded addresses for the C&C server.
The Hide’N’Seek botnet also used a custom-built P2P communication module to spread itself. The botnet infected targeted IoT devices with weak security using a very complex infiltration module. It featured multiple stealth protection techniques which prevented security applications and services from discovering the malware infections.
It is worth mentioning that efforts to take down the Hajime botnet were not successful, and some say it is still active, with 40,000 infected devices daily. As for Roboto, its size is yet to be determined, but researchers believe it is not larger than Hajime.