A new highly sophisticated APT framework used for spying purposes was recently uncovered by security researchers. The malicious framework has been in operation for at least 5 years but it’s the first time it’s been detected. The framework has been dubbed TajMahal.
“In the fall of 2018, we detected an attack on a diplomatic organization belonging to a Central Asian country. There would be no story here (diplomats and their information systems attract the interest of various political forces every now and again) were it not for the tool employed: a new APT platform by the name of TajMahal,” said Kaspersky Lab researchers who discovered the APT.
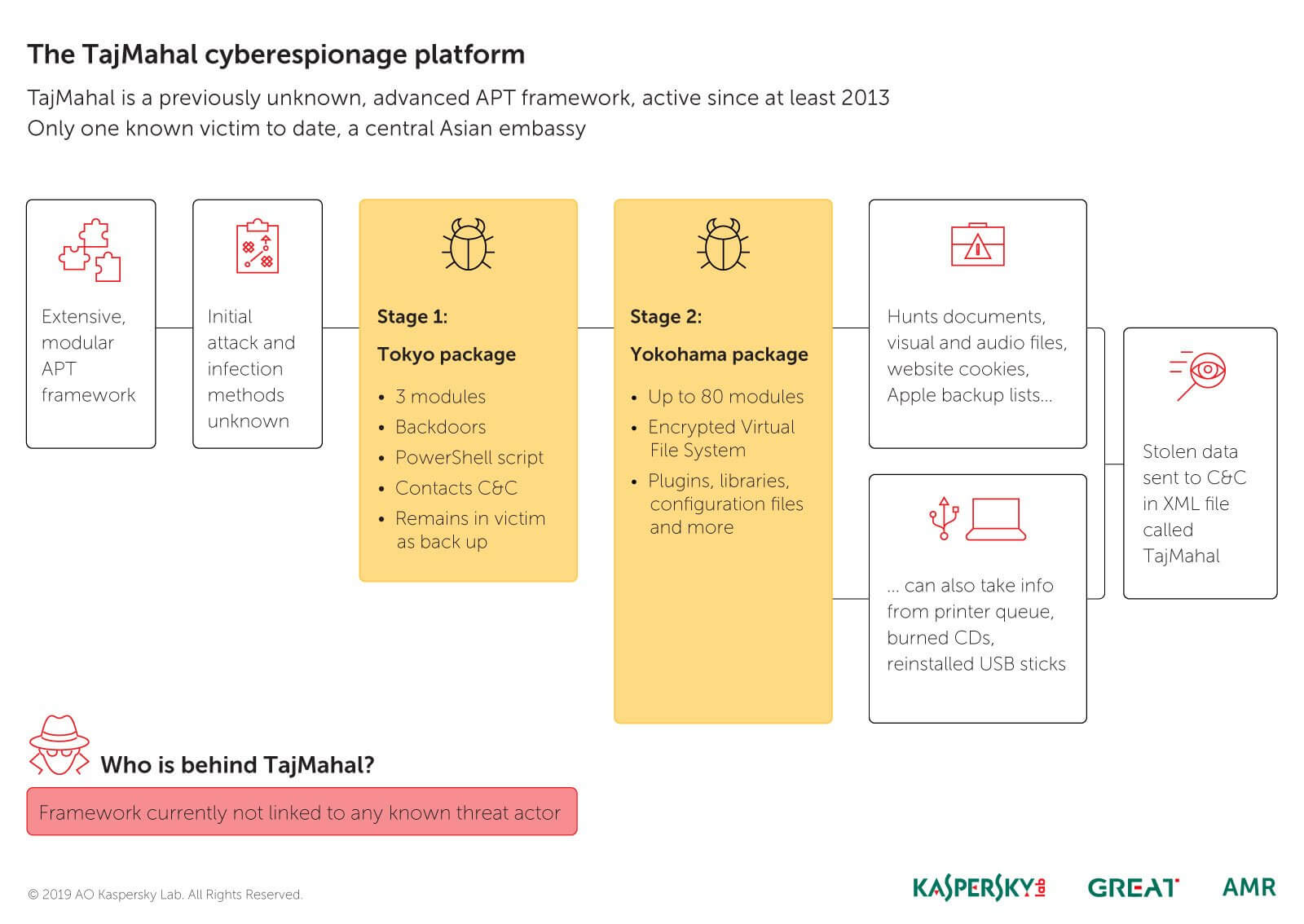
TajMahal APT Framework: Technical Overview
Shortly said, TajMahal is a highly sophisticated, high-tech spyware framework which features a vast number of plugins (80 malicious modules have been found so far), allowing for all kinds of attack scenarios using various tools, Kaspersky said. It appears that TajMahal has been in operation for the past five years. What’s very intriguing and troublesome in the same time is that only one victim has been confirmed to date.
TajMahal APT platform contains two main stages dubbed Tokyo and Yokohama which were detected on all infected computers that the researchers analyzed. Tokyo appears to play the role of the main backdoor which delivers the second-stage malware.
Note that Tokyo remains in the system even after the second phase starts, as it is most likely needed to operate as an additional communication channel. As for Yokohama, it is “the weapon payload of the second stage” which is designed to create a virtual file system complete with plugins, third-party libraries, and configuration files. It is capable of the following
– Stealing cookies;
– Intercepting documents from the print queue;
– Collecting data about the victim (including a list of backup copies of their iOS device);
– Recording and taking screenshots of VoIP calls;
– Stealing optical disc images made by the victim;
– Indexing files, including those on external drives, and potentially stealing specific files when the drive is detected again.
Here’s how the researchers depict TajMahal’s operation:
The technical complexity of TajMahal makes it a very concerning discovery, the researchers highlighted in their report.