
There are many articles out there that have tips and tricks to protect your smartphone, and most of them tend to offer different protection software for a smartphone or just tell you to update often, but not a whole system of apps and tips that can be combined for increased protection. This got us into thinking how can we protect a given smartphone as best as we can. This is why we created the following article which includes extended instructions on how to protect your smartphone device from prying eyes, even from someone who has access to it physically. And if you follow these safety tips and turn them into your habit and never neglect them, you will be sure to have a more protected smartphone in the future.
We have separated this article into several key areas of improvement of a smartphone device. These areas include:
- Privacy protection.
- Protection from malicious software and hackers.
The areas of improvement which we will focus on grasp primarily the three primary types of device OS’s that are out there – Windows Mobile, Android OS, and iOS. We will suggest a variety of tips and tricks improve those devices using different apps for each and every device out there. Read carefully, if you are interested in improving your phone’s security the proper way.

The Privacy Protection Area
When it comes to privacy, all we can talk about is Apps, Cookies and other tracking technologies used by legitimate software to pry on your device. If you are sensitive regarding this subject, then several key applications can help you protect your device from privacy invasive apps. These apps may be legitimate ones, but there are also those applications that take advantage of the phone’s privacy to extract critical information from it and use it for malicious purposes. According to research at Statista the number of apps available at App stores are becoming over 2 million, and this is a vast number to control when newer and newer apps come out. There have been even cases of fake apps for both Android and iOS devices in the past, and there were multiple users infected. So what do we do to protect ourselves?
Android
Checking Apps
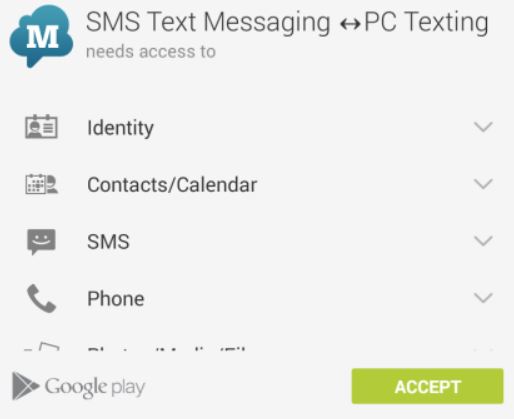
Regarding Android, it can be said that it is the most targeted set of devices out there. There are many privacy invasive apps that request different permissions. One way to manually check for those permissions is before you install a given app. What Google PlayStore does is it checks the applications every time before their installations and displays to you what they want from you if you scroll down to read more about the app before installing it.
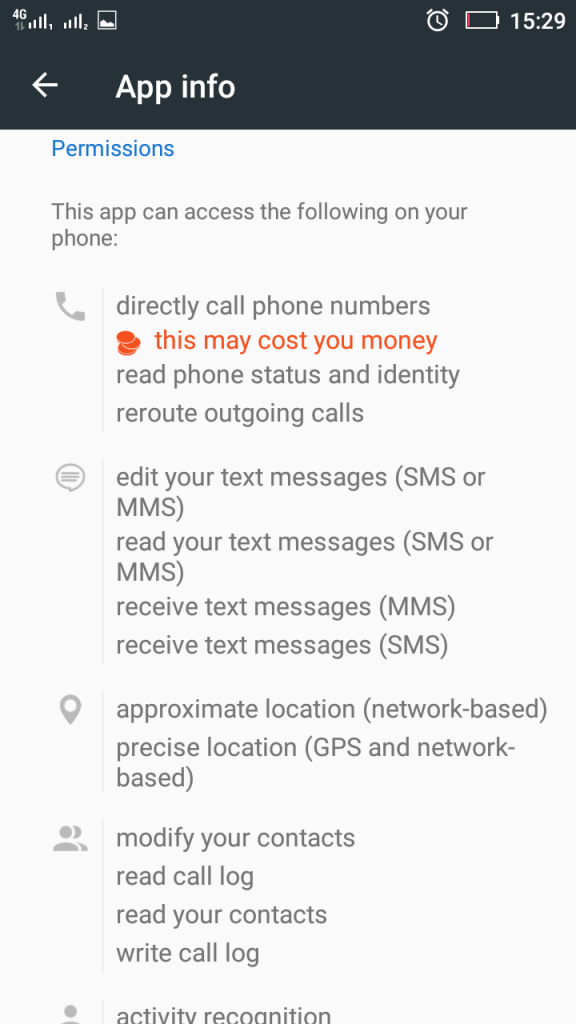
Here is where you have to make a decision and check the app online for other user opinions and reviews of the app to know whether to trust it or not. However, many Android devices come with embedded “recommended” apps in them which are typically called bloatware. Such bloatware apps are useful for you, but in many cases, they are demanding either too much information or to use a registered version which costs money. To check an app that has already been installed on your computer for invasive permissions, you should visit the Settings of your Android device and locate the Apps management setting. It will open all of your apps. Since it will separate them on different tabs, make sure to go to “All” tab to see all apps.
From there, you can simply select an app that you believe is bloatware and see what type of permissions it requests from your Android device:
Make sure to select the apps that you want to clear out of your phone carefully. If you believe an app is truly useful for you and you have checked the app for legitimacy online (Google), there is no need for deleting it.
But this is not by far the best method to check apps, because, generally it is slow. This is why there are apps created to easily this situation. BetterGuard Mobile can easily scan your Android device for apps that are privacy-invasive and recommend to you such apps for deletion. Since the software only checks privacy, it is up to you to decide whether to delete the apps or not.
The Connection Settings
Another issue with privacy for Android is that the device is also exposed to something else, besides apps – it’s own connection, the main problem for many other devices out there. There are numerous scenarios in which hackers can simply take advantage of your smartphone. Take “the evil-twin”, for example. This type of attack involves creating a duplicate twin wi-fi network in a public place, where it is unsecured. For example, if you are in a Café and the Wi-Fi network is called “Café”, the duplicate network has absolutely the same name and nobody bats an eye that it is a fake one. Once you connect to Wi-Fi, because you do not want to exceed your data usage, obviously, it is already becoming too late for you. Everything you browse online, your passwords, your accounts, everything can be subjected to attacks. This is why it is important to take serious measures against these attacks.
One method of protecting your connection is to use a VPN service. However, the sole term VPN nowadays brings shadiness to security. Recently, researchers have established that over 38% of VPN apps may track the privacy of the phone. This is why we recommend using a trusted application, like oVPN for example, which offers not only a service but also a solution for most operating systems out there.
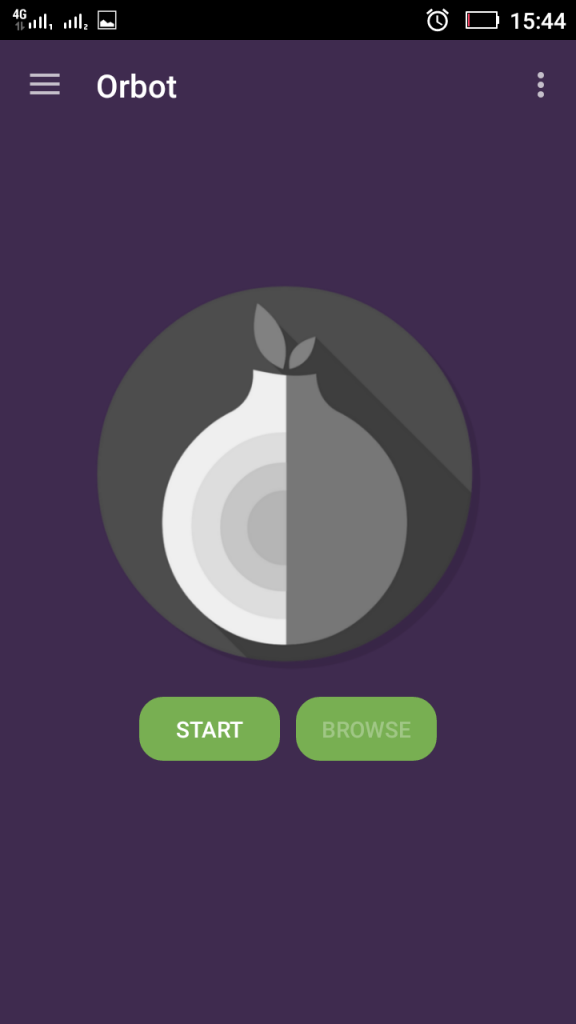
Regarding privacy of your connection, besides VPN, there are also other types of applications which you can take advantage of. Let us not forget something used by experts like Edward Snowden and many criminals out there – the randomness of the TOR network. The benefits of using TOR is that your online data passes through random machines, called nodes to anonymize you completely. And as you may have already guessed, there is a tor app, called OrBot for Android devices which completely anonymizes them. The app is very incognito while running, and there is minimal delay in the internet speed while using it.
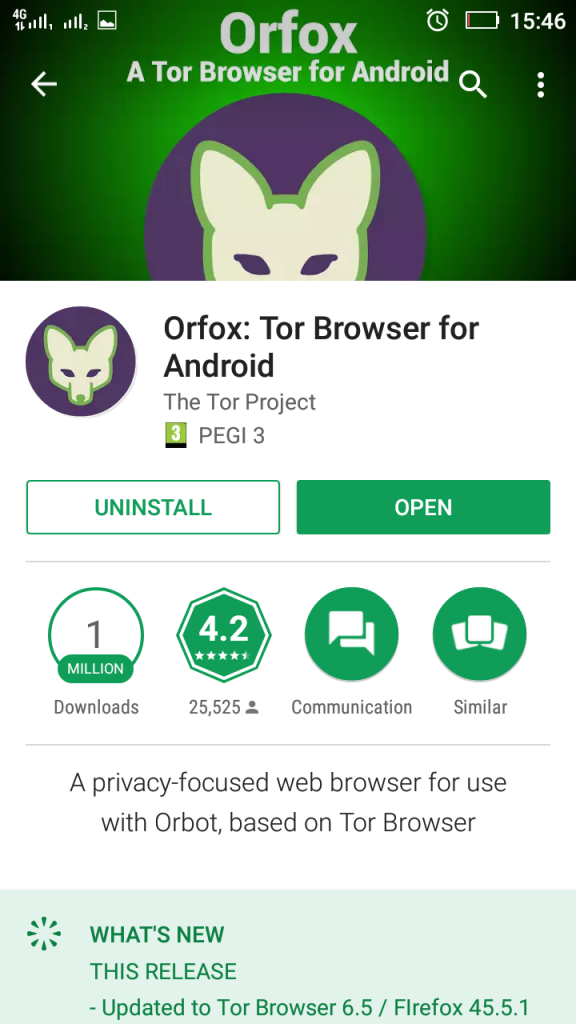
The downside of the Orbot application is that even if you use it to browse anonymously online, some websites still require cookies and can still track your device. But, be aware, you can also use the Orfox browser, if you have the tolerance for waiting for a web page to load for a minute and to perform multiple CAPTCHA types of checks, you can go ahead and download it from the PlayStore:
Apple iOS
Regarding Apple’s latest iOS, things concerning privacy are rather simpler. This is because of the sandboxing in the iOS and the higher security of the devices. The phone has custom features that allow you to custom check every app and disable the permissions you do not want it to track you with. This can simply be achieved if you get to Settings of your iOS device and then scroll down to find the apps that are installed on the iPhone itself.
In addition to this, in proximity to Android devices, the apps can also be checked before downloading from the AppStore. There were cases of false apps in the AppStore that compromised iOS devices regarding privacy, so this is why it is also necessary to install a privacy protection application for iOS. One suggestion with a relative good online rating is called AdGuard – an app that not only protects you from advertisements but also cares about your privacy as well.
But apps are not as far as we are going to go, regarding privacy. There are also some settings that the latest iOS 10 has and that you can modify to further lock down the device. One of those settings is the “Add Widgets” panel which you can modify on your IOS device to turn off which apps you would like to show information on your locked screen. This may prevent even someone who has stolen your phone to know more information about you or even unlock the device by taking advantage of bugs in widgets.
For further privacy and security, you can also switch of some of the features which you can access from the home screen of your Apple device. If you get to Settings – Touch ID & Passcode and then scroll further down, you will see multiple areas on your lock screen amongst which you can choose to turn off.
Another thing you can disable is Touch ID and fingerprint unlocking and enable a strong passcode instead if you value Privacy a lot.
Furthermore, you can also stop the location tracking on your iPhone by accessing Settings – Privacy – Location Services–System Services. But for this to happen, you have to forget using any apps involving location too. You can also clear your location history for more privacy features.
If you have your AppStore connected to your account, you can also set to require a confirmation from you every time purchase from the AppStore has been made in your name.
As far as iOS goes, these settings should be sufficient to improve your privacy but bear in mind that you can also find other methods to protect it as well.
Windows Mobile
Windows 10 mobile has many advanced features, and in some Windows devices, the device can even become a computer if you plug it into a docking station and an HDMI to USB cable on a monitor. We have several suggestions on how to help you protect the privacy of your Windows 10 mobile device if you are sensitive on the subject.
One important tip is to stop any notification pop-ups from your Windows 10 Mobile device. These pop-ups can be cut out if you go to Settings-Systems_notifications and Actions. From there you can select each setting for each app, including the displaying of notifications.
Another cool trick is to lower the screen time out to a minimum, in case you get careless (drunk) and leave your device after using it. The minimum for this is 30 seconds. The setting can be changed by going to System – Personalization – Lock Screen.
If your Windows Mobile device has support for the feature Glance Screen, there is a method to change it’s settings too. You can go to Settings – Personalization–Lock Screen again. And from there you can change its settings from “Choose an app to show detailed status” option.
There is also another option that can further help you out in modifying the privacy of your device. You can restrict the way how some applications on your device use the Microphone, in case you do not trust them. The Settings-Privacy-Microphone menu can modify this.
Another setting which you can also change is to completely switch off the motion data of your device from the Privacy – Motion data setting.
Another information that is collected by Windows is the speech and typing data. This can be stopped if you turn off the “getting to know you” feature.
Similar to Android and IOS, you can also modify what exactly is used by different applications on your phone from the previously mentioned Privacy settings menu.
Some applications tend to follow the behavior of the user via a service for Windows Mobile devices, named Advertising ID. If you turn it’s settings off, you can further increase the privacy of your device.
The final suggestion by experts at Windows Phone Area(https://www.windowsphonearea.com/10-tips-protect-privacy-windows-10-mobile/) is to minimize the usage data. You can set it to Full all the way to Basic, and of course, it is recommended to be the basic option.

The Protection from Malicious Software and Hackers Area
This segment of the research is a bit more simplified as most of the security issues originate from the privacy. However, we have also paid great attention to it, because there are numerous ways by which you can still become infected. There are many phishing websites, messages on social media with web links that cause a malicious redirect and force infect the device and many many other methods with which hackers can infect your computer.
Android, Windows Mobile, and iOS
It is with pain to write about Android security in general because while these devices are the most frequently met in the world, they are also the most targeted by malware via fake apps, web links, and even phishing websites. So how to protect yourself from this, besides having an antivirus and frequently updating your Android device? There are numerous ways to do this.
Usually Android has several security features built in, and those features can be used extensively to increase security. And with the newer Android 7.0 Nougat, those features have now increased.
One way to protect yourself on your Android device is, of course, choose an advanced antivirus program that is active at all times on your device. Avast, for example, offers many solutions at once in it’s mobile app which is completely free in the Google PlayStore, AppStore and Microsoft Store. And the app does not restrict your network traffic in any way too.
But an app is not protection, and we know it. This is why you need to change your behavior and think the opposite of what a cyber-criminal would do. This means checking every app before downloading it online and never opening malicious web links on your Android device. If you do not trust someone you are chatting with, it is also advisable to avoid any web links sent to you or check them in online services like VirusTotal.com before actually opening them.
Another way to protect yourself is if you avoid connecting to any Public Wi-Fi networks at all. Even though they are safe, if someone has access to them, they can compromise your device through this.
Another useful tip for your mobile device is checking your IMEI code. The IMEI code can track if your phone is under surveillance by malicious software or note. To check the IMEI code *#06#. It will show you the ID. The ID is typically 15 digits. If the ID is more than it’s typical number, then your device may be invaded. The original IMEI can also be found on the inner side of the Phone itself if you remove the battery.
Another interesting thing, if you have an Apple device is to check it for a suspicious app that can be installed by someone who has had physical access to the phone. The app has been reported by experts are GoHacking(https://www.gohacking.com/iphone-spy/) website to be colled SpyStealth App and once installed, this app runs in the background and is hidden. From there you can be monitored for calls, messages, chat activity, location, social media and the other usual.

Conclusion on Smartphone Security
Smartphones are devices for which spy agencies would kill a person to have a couple of years ago. They are electronic devices that have many features which have already proven their usefulness to us in many situations. They have become part of our lives. And we, as people, really need to be more educated on how to protect our daily activity with those devices. Because, one day, we may be sorry that we didn’t do it, but then it will be too late.
These are not all the tips and tricks for protecting smartphones, but if used together, they can increase the protection on your mobile device, somewhat. Or you can simply be like Eugene Kaspersky (CEO of Kaspersky™) and go old school:
We have suggested some methods here, but we would like to hear what you think on the matter. In the event that you are interested in the subject, please leave us a comment down below and let’s discuss it.






I dialed *#06# on my samsung edge and the IMEI appeared to be like this 000000000000000/00. Does it means I am really invaded?