
File Extension UNKNOWN – How to Open It?
Each file has an extension, but every now and then you may come across a file in an UNKNOWN format. In such cases, it is a real challenge to identify the type of the file and find an application to…

Each file has an extension, but every now and then you may come across a file in an UNKNOWN format. In such cases, it is a real challenge to identify the type of the file and find an application to…

Shortly after the scandal with the nude celebrity pictures that leaked online, Apple has activated a 2FA (two-factor authentication) for iCloud. In the 2FA process user has to enter additionally a second passcode, which is dynamically generated and consists of…

For the majority of the Internet users, the browser is their connection to the rest of the Web. It is used to navigate to various webpages, allows users to follow links, and helps them explore basically everything the Web has…

Here are a few tips what to do, if you are wondering what could possibly be wrong with your computer when you cannot get your USB device to work. Something is obviously broken, but you have no idea if it…

Many critics question Microsoft’s lack of a decent platform for its MS Office suite on iPad tablets and different smartphones. Actually, Microsoft has numerous options of MS Office suitable for cell phones. They are just not completely featured versions of…
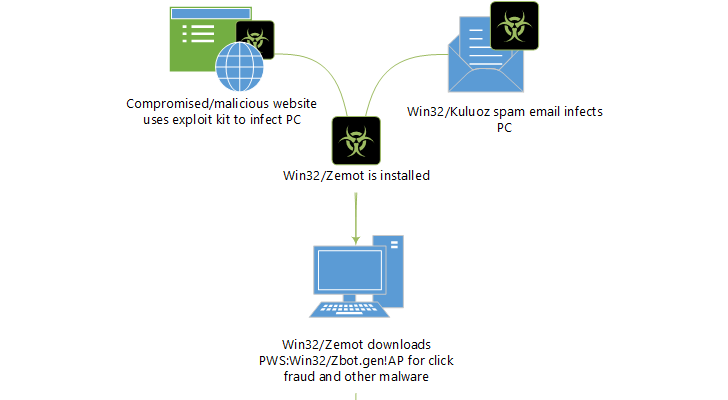
What Is Zemot? Zemot Dropper is a type of malware downloader. It is part of a complex network, which includes different malware types. Different variants of Zemot can be distributed with other malware as one dropper can spread many malicious…
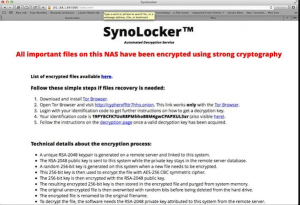
What Is SynoLocker and How Does It Work? SynoLocker is a file encrypting ransomware that targets Synology NAS (Network Attached Storage) devices. What this particular piece of ransomware does is to exploit vulnerabilities in the DSM operating system. It targets…

A campaign run on Twitter tries to lure users into landing on a phishing page which only goal is to get users’ credentials. It seems that either compromised Twitter accounts or bots are used to deliver a spam message with…

For some time now, Google has been trying to limit the security issues related to the numerous applications that get installed on Google Chrome along with the installation of various unverified extensions. It is mandatory for apps and extensions that…

Computer technology experts say that NFC is the next big thing that will be applied by the new mobile phones that are presented on the market. Though new to the users and yet to be adopted by the masses, the…
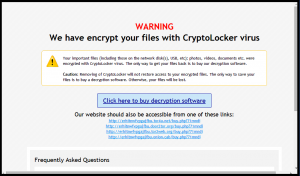
Finnish researchers Antti Nuopponen, Patrik Nisén and Taneli Kaivola of Finnish consultancy Nixu discovered how to decrypt the files that have been encrypted by the recently spread TorrentLocker ransomware without paying the required fee. All the user needs is the…

The details on the new upcoming iPhone 6 and Apple Watch were announced yesterday. Both devices will be equipped with Apple’s new contactless mobile payment system – Apple Pay. Apple Pay enables phone payments at points-of-sale without sharing credit card…
Dyre, also known as Dyreza and Dyranges by Symantec, is a malware notorious for pursuing banking credentials. Dyre is focused mainly on the customers of Bank of America and Citibank, RBS and Natwest in the UK, and Ulster Bank in…

A message on Facebook that appears to be from a person in the user’s friend list, invites people to click on a link that is supposed to show a video of two little human-like creatures. Many users trust the link…

After the naked pictures of several celebrities have leaked online recently, and the Kelihos botnet phishing campaign managed to take advantage of the users’ worries spamming them with fake emails and thus collecting their Apple IDs, the issue with the…

Earlier this morning, unknown cyber criminals have leaked over 5 million Gmail usernames and passwords on the Internet. The database containing the credentials appeared on a Russian Bitcoin forum. All the passwords are presented in a .txt file. How the…

Shortly after the iCloud accounts of numerous celebrities have been compromised, the cyber crooks behind the Kelihos botnet started a new phishing campaign, targeting the owners of Apple online accounts. Russian IP Used for the Alleged Purchase The Symantec Research…

Kyle and Stan – A brand new malvertising network has been affecting Windows and Mac users who visit popular webpages such as amazon.com and youtube.com since May this year. The cybercriminals use Yahoo, Amazon and YouTube domains to infect users…

After the successful law enforcement operation in late May that took the Gameover Zeus botnet down, CrypoLocker was almost crushed. Yet, new ransomware arises. Along with the Gameover Zeus network of infected computers, a ransomware campaign was compromised as well…
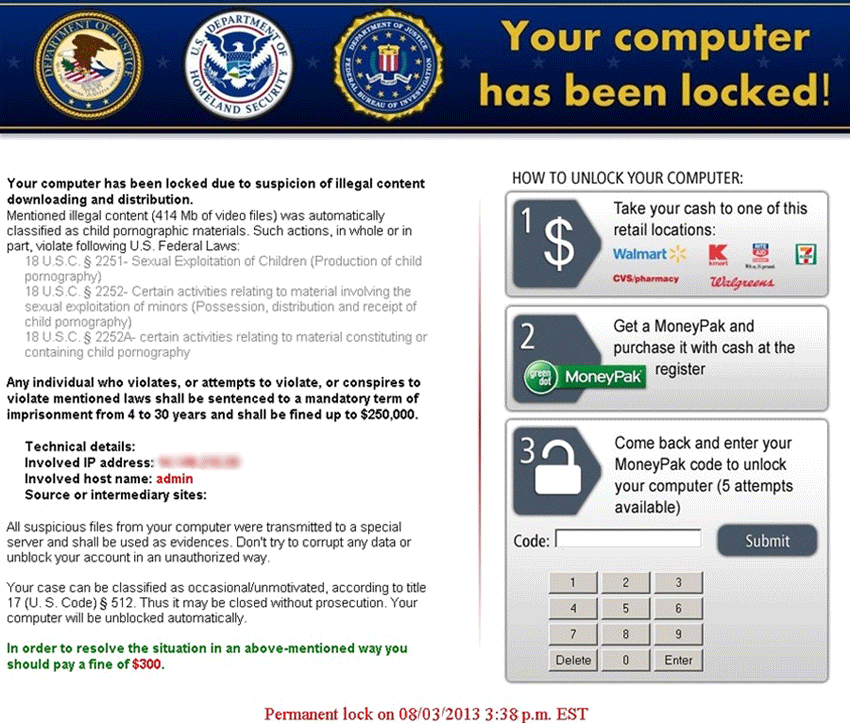
Kovter ransomware infections have increased significantly in the second quarter of 2014, report malware researchers from the Damballa security firm. On average, the daily incidents have been up by 153% between April and May this year. The ransomware has reached…