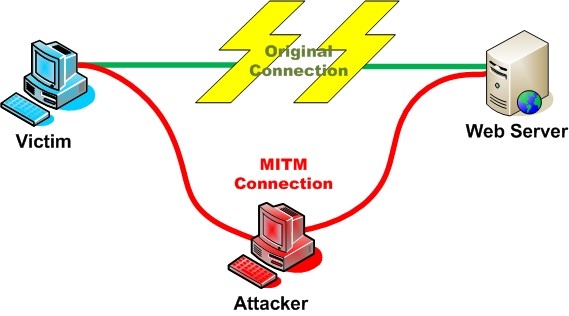
A new type Man-in-the-Middle (MitM) attack called “DoubleDirect” is spreading over the Internet these days. What the attack does is redirecting traffic of wireless connections from big web-site domains like Facebook, Google, Twitter, to malware-infected sites. Falling on such the hackers can steal certificates, credentials and other personal data, as well as infect with malware their victims.
DoubleDirect Working Method
The new malware was found by Zimperium security company researchers. Its technique is the divert the route tables of the Internet Protocol Control Messages (ICMP) from one host to another. The protocols are being used as routers to direct the users’ machine to a better way for a specific spot on the Internet.
“DoubleDirect uses ICMP Redirect packets (type 5) to modify routing tables of a host. This is legitimately used by routers to notify the hosts on the network that a better route is available for a particular destination”, Zimperium researchers wrote in a post on the subject.
Subjects to the Attacks
Subject to the attack are devices with iOS (including 8.1.1.), OS X (including Yosemite) and Android (including Lollipop) which usually accept redirecting routes by default. The attack is not working on Windows and Linux though because they do not allow traffic redirection.
Usually redirecting the ICMP can be done either while sending, or while receiving data over a wireless connection but it cannot be applied to both. The new thing in DoubleDirect is that it can perform the MitM attack simultaneously for both which makes it quite dangerous for the infected machines.
Analyzing the attack, the Zimperium researchers proved that the hackers perform a DNS research prior the attack to determine what IP addresses the victim visits. The next step they perform is sending the protocol messages to all IPs found. The attack is known to be active in 31 countries by now – Algeria, Australia, Austria, Bahrain, Brazil, Canada, China, Colombia, Egypt, Finland, France, Germany, Greece, India, Indonesia, Iraq, Israel, Italy, Kazakhstan, Latvia, Malta, Mexico, Netherlands, Poland, Russian Federation, Saudi Arabia, Serbia, Spain, Switzerland, United Kingdom and the United States.
Corporate networks are vulnerable to these attacks as well, and the researchers have presented a simple tool for the DoubleDirect attack detection. You can check it out here.