MacRansom and MacSpy are two samples of new Mac malware that has been created by the same person. That person is also offering the two pieces for sale via the malware-as-a-service model on two dark web portals. Potential customers and wannabe cybercriminals are instructed to get in touch with the author via a Protonmail address.
Researchers from AlienVault and Fortinet decided to contact the criminal so that they get the chance to analyze MacRansom and MacSpy. The very first thing that Fortinet researchers pointed out, however, concerns the wide belief that Macs are safe from ransomware and malware attacks.
“It is true that it’s less likely for a Mac OS user to be attacked or infected by malware than a Windows user, but this has nothing to do with the level of vulnerability in the operating system. It is largely caused by the fact that over 90% of personal computers run on Microsoft Windows and only around 6% on Apple Mac OS,” they explained.
So what are the specifics of the newly discovered Mac malware samples?
More about MacSpy
Apparently, MacSPy has two versions: a free basic version and an advanced one that can be bought in Bitcoins.
As for the malicious capabilities of MacSpy, the malware is a simple RAT/spyware that is designed to capture screenshots, record audio, steal photos, retrieve clipboard contents, steal browsing histories and download data, and had keylogging capabilities. The malware also communicated via Tor. As for the advanced version that is available against a certain price – it can retrieve any file or data from the victim machine. It’s also capable of encrypting the user directory, granting access to email and social accounts, among other things.
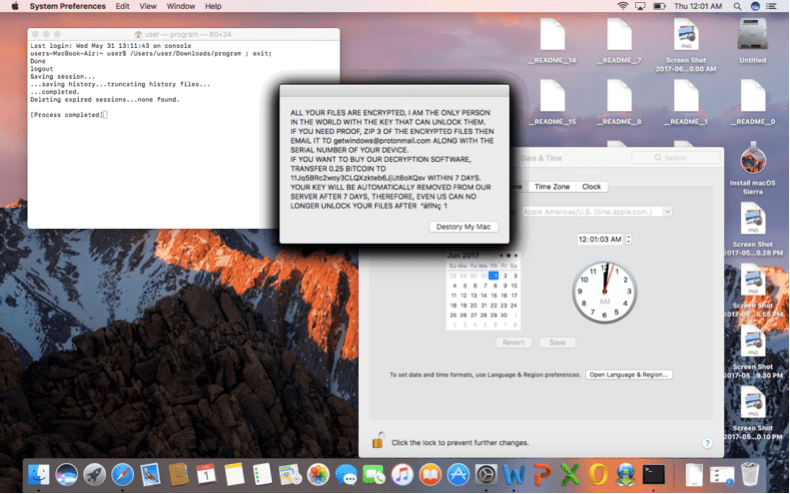
More about MacRansom
According to its developer, MacRansom uses unbreakable encryption. However, further details are not provided. Analysis by Fortinet researchers shows that the ransomware can only encrypt up to 128 files via a symmetric encryption with a hardcoded key. The developer has used two sets of symmetric keys: a ReadmeKey and a TargetFileKey.
“The ReadmeKey is used to decrypt ._README_ file that contains the ransom notes and instructions, while the TargetFileKey is used to encrypt and decrypt the victim’s files,” the researchers wrote, adding that:
A remarkable thing we observed when reverse-engineering the encryption/decryption algorithm is that the TargetFileKey is permuted with a random generated number. In other words, the encrypted files can no longer be decrypted once the malware has terminated – the TargetFileKey will be freed from program’s memory and hence it becomes more challenging to create a decryptor or recovery tool to restore the encrypted files.
In addition, MacRansom doesn’t have the capability to communicate with a Command & Control server for the TargetFileKey which means that there isn’t a prepared copy of the key to decrypt the files. “However, it is still technically possible to recover the TargetFileKey. One of the known techniques is to use a brute-force attack. It should not take very long for a modern CPU to brute-force an 8-byte long key when the same key is used to encrypt known files with predictable file’s contents. Nevertheless, we are still skeptical of the author’s claim to be able to decrypt the hijacked files, even assuming that the victims sent the author an unknown random file,” the researchers concluded.
What Do MacRansom and MacSpy Have in Common?
As mentioned in the beginning, the two pieces appear to have been coined by the same developer. MacRansom and MacSpy share the same anti-analysis mechanisms, and also use the same method to create a launch point so that the piece starts upon system restart.
Neither MacRansom nor MacSpy are digitally signed meaning that if a user downloads either of them and runs it, the operating system will display a warning stating that the program comes from an unidentified developer. The developer of the malware also tells users to gain physical access to the target machine in order to install and run it.