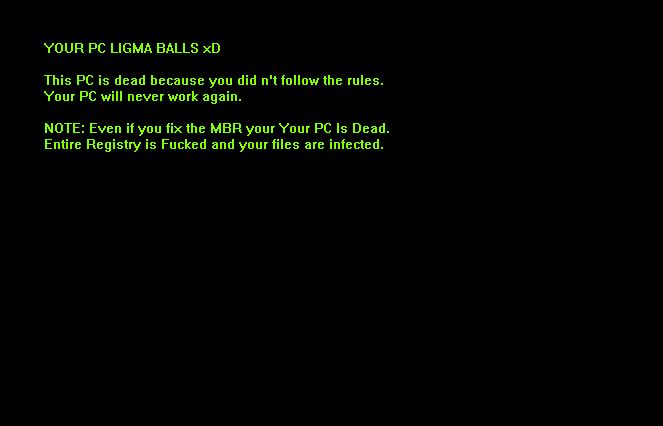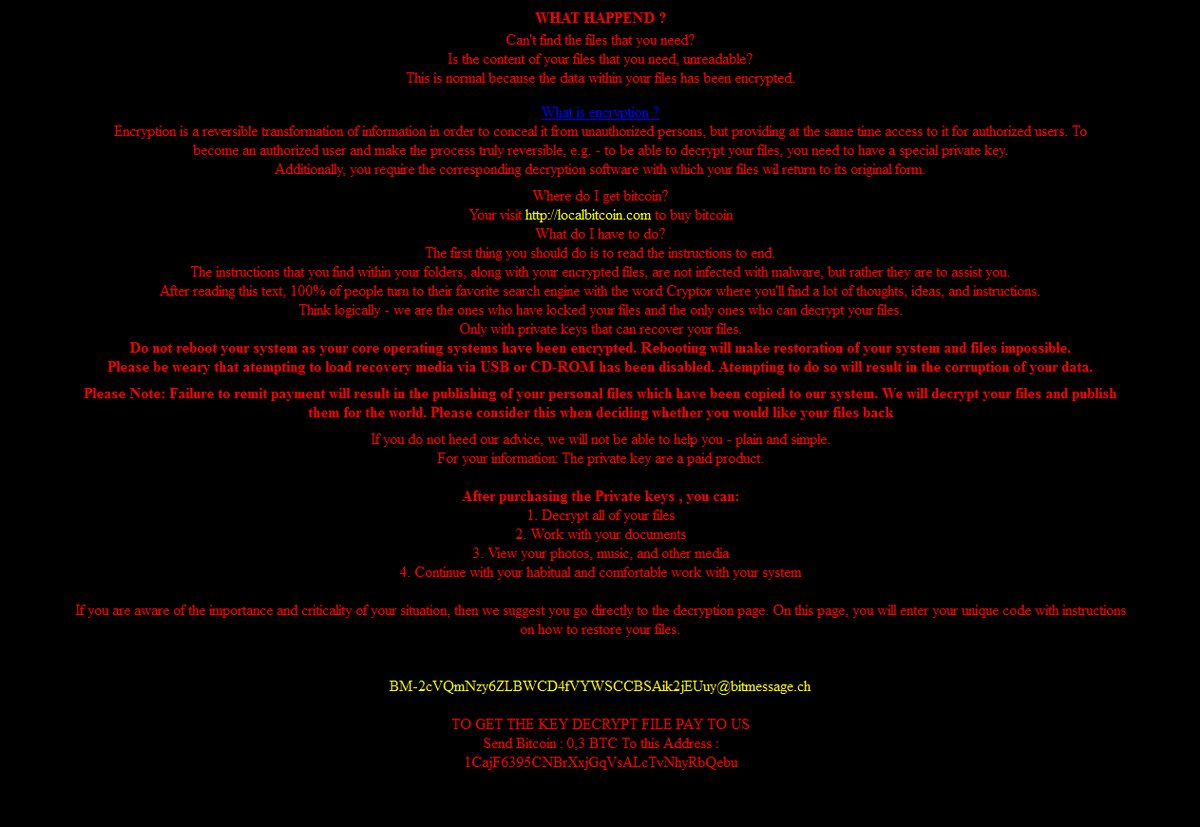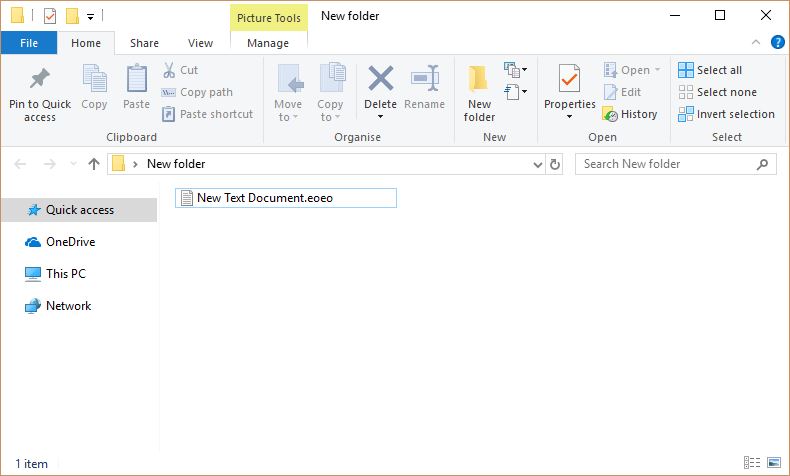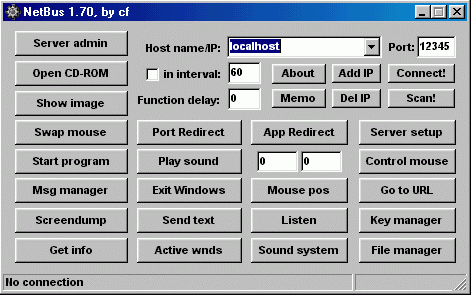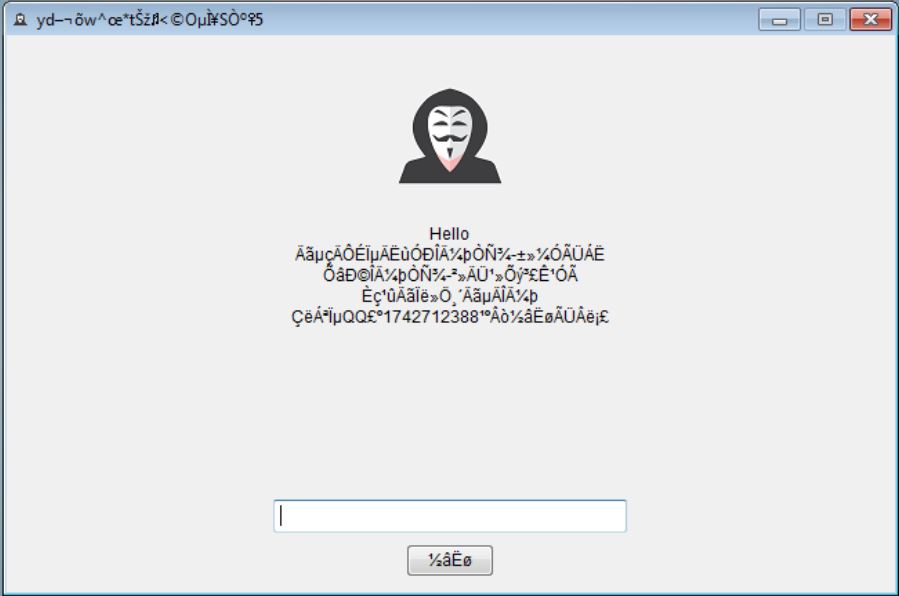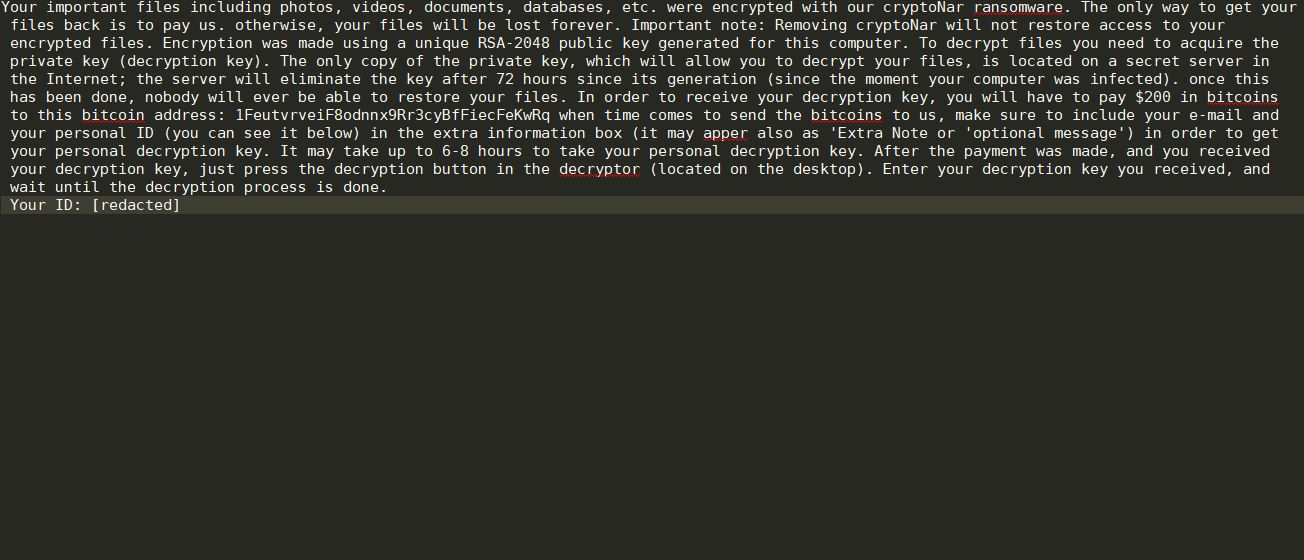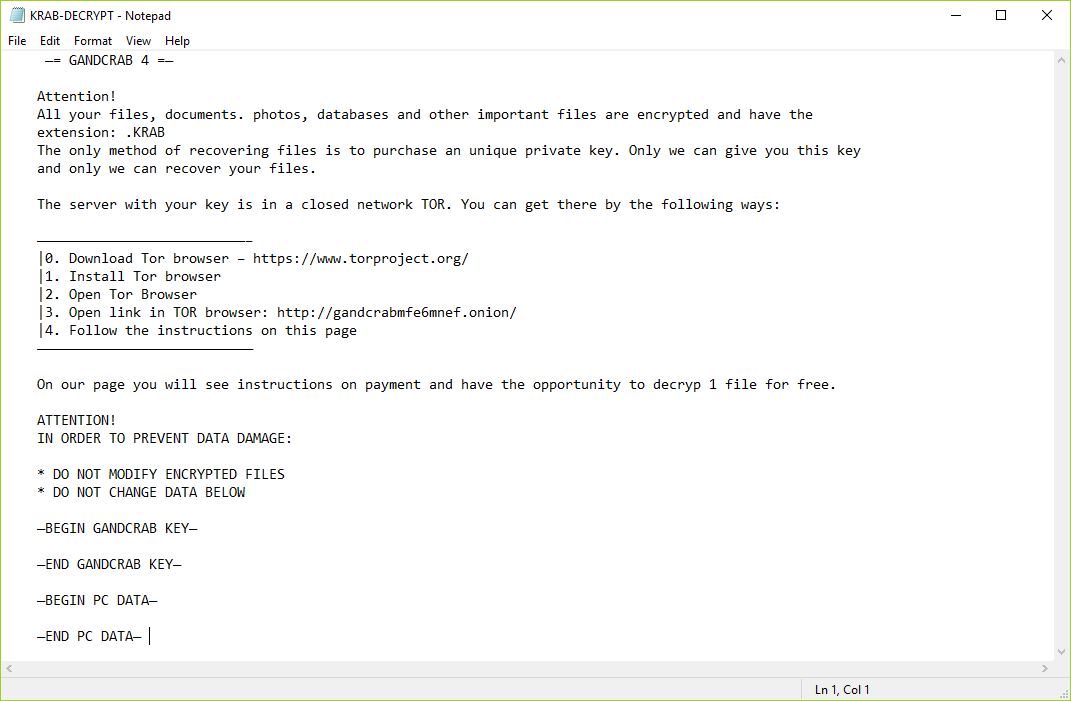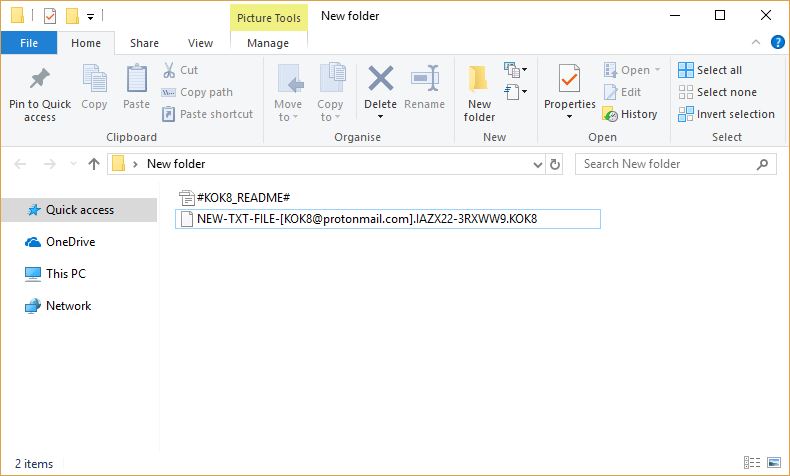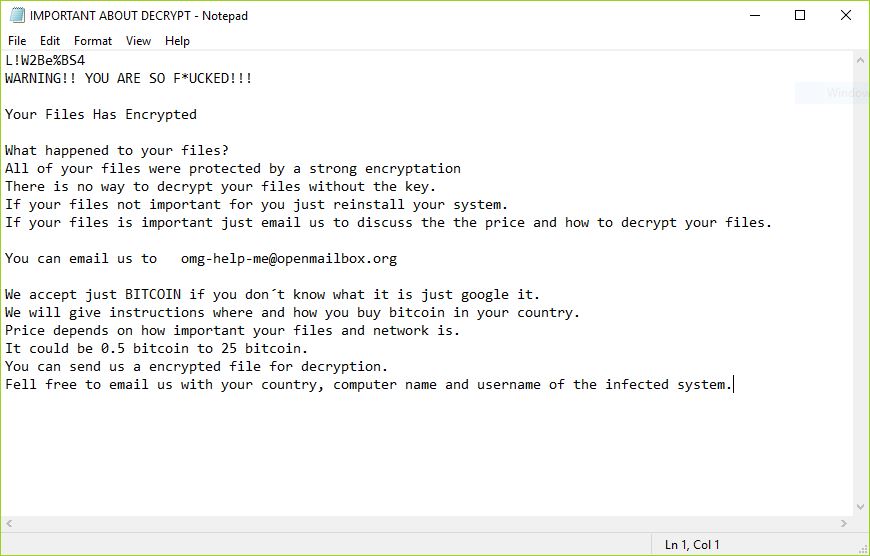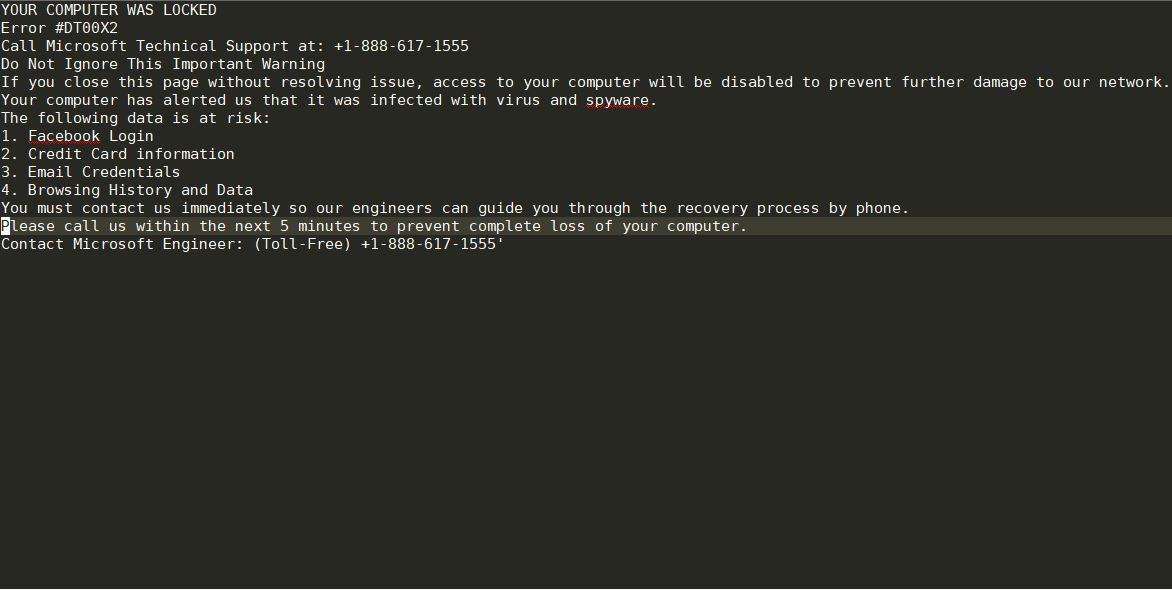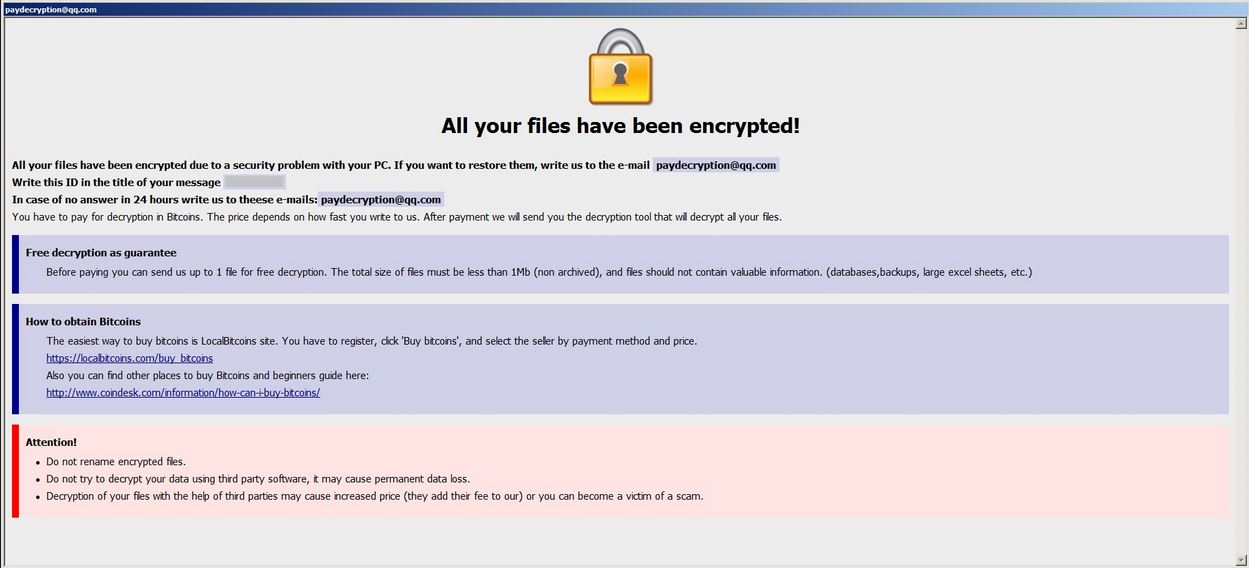
Remove Dharma Virus — Restore .brrr Files
The .brrr Dharma virus samples are a recent campaign delivering a new iteration of this ransomware family. According to the security analysis they use the same behavior pattern the previous versions. Our article provides an overview of the virus operations…