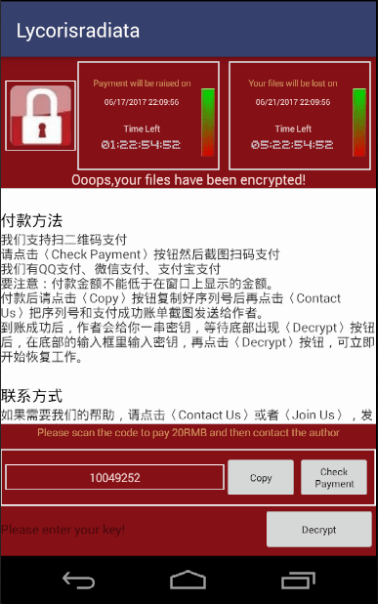
WannaCry August Update ‒ Ransom Sums Collected and Slayer Arrested
The security community reported two major incidents connected to the infamous WannaCry ransomware that hit computers worldwide about a month ago. The operators behind it have managed to collect the ransom sums. At the same time the expert who shut…