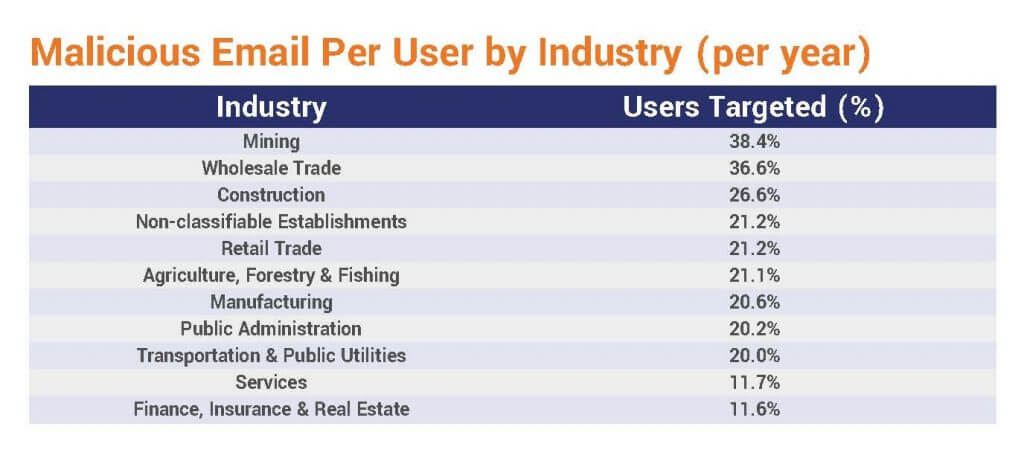
Top 10 Global Cybersecurity Issues in 2019, with 2020 in Mind
“Cybersecurity is the Biggest Threat to the World Economy, CEOs Say” So reads the July 9 headline of a major news publication on its website just two short months ago. Concerns about internet and network security have been around for…



















