
BitRAT Trojan Removal
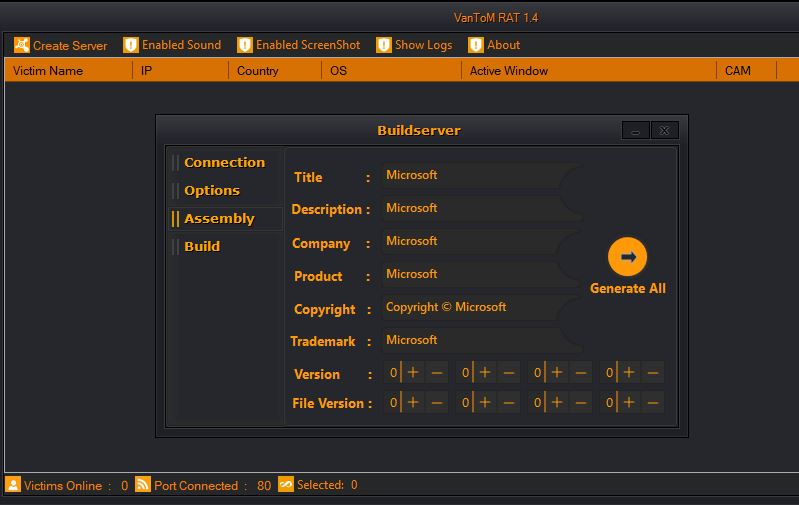
What is BitRAT Trojan? How Dangerous are BitRAT Malware Files? Exactly how to remove BitRAT Trojan completely? How to prevent threats, like Trojan.BitRAT in the future? BitRAT Trojan is a dangerous malware this is certainly malicious whoever main goal is…






![Coin Miner Virus – How to Remove It [Coinminer Malware] Coin Miner Virus - Coin Miner Malware](https://cdn.sensorstechforum.com/wp-content/uploads/2020/07/coin-miner-malware-crypto-miner-virus-remove-it-how-to-guide-1024x576.jpg)










![Trojan Horse Viruses – All You Need to Know [Removal & Protection Guide] Trojan Horse guide](https://cdn.sensorstechforum.com/wp-content/uploads/2020/06/Trojan-Horse-guide-1024x585.jpg)

