
Wise System Mechanic – How to Remove It from Your PC
This article has been created in order to explain what is the suspicious Wise System Mechanic PUP and how to remove it completely from your computer. A new potentially unwanted program, going by the name Wise System Mechanic has been…
















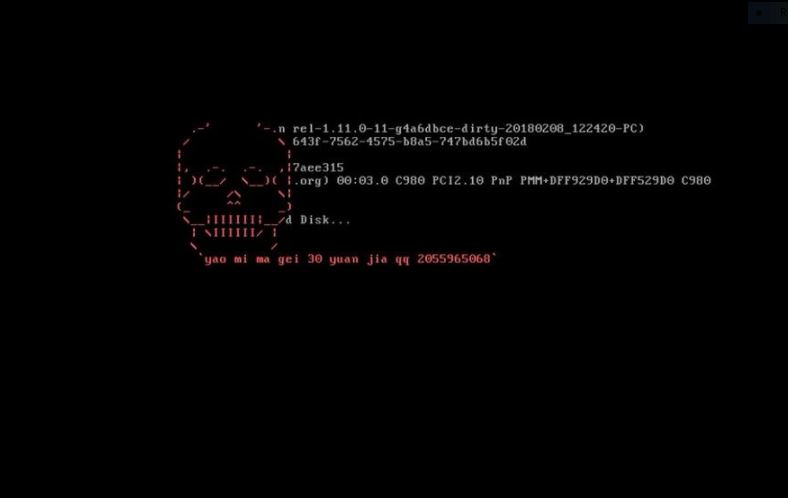
![Taskhostw.exe – What Is It + How to Remove It [Fix] Taskhostw.exe - What Is It + How to Remove It [Fix]](https://cdn.sensorstechforum.com/wp-content/uploads/2018/02/taskhostw-exe-what-is-it-how-to-remove-it-1024x576.jpg)


![Java:Malware-gen [Trj] Trojan – How to Detect and Remove CrossRAT](https://cdn.sensorstechforum.com/wp-content/uploads/2016/02/remote-access-trojan-sensorstechforum-300x260.png)




