Uclaut.net (Adf.ly) “Virus” – How to Remove It
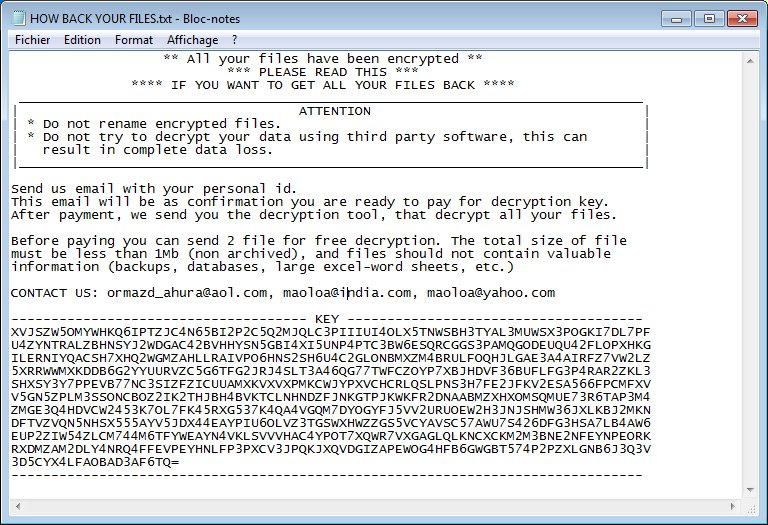
This article has been created to explain what is Uclaut.net browser hijacker and how you can remove it completely from your web browser, plus how you can try and restore your computer back to normal state. A new phishing and…