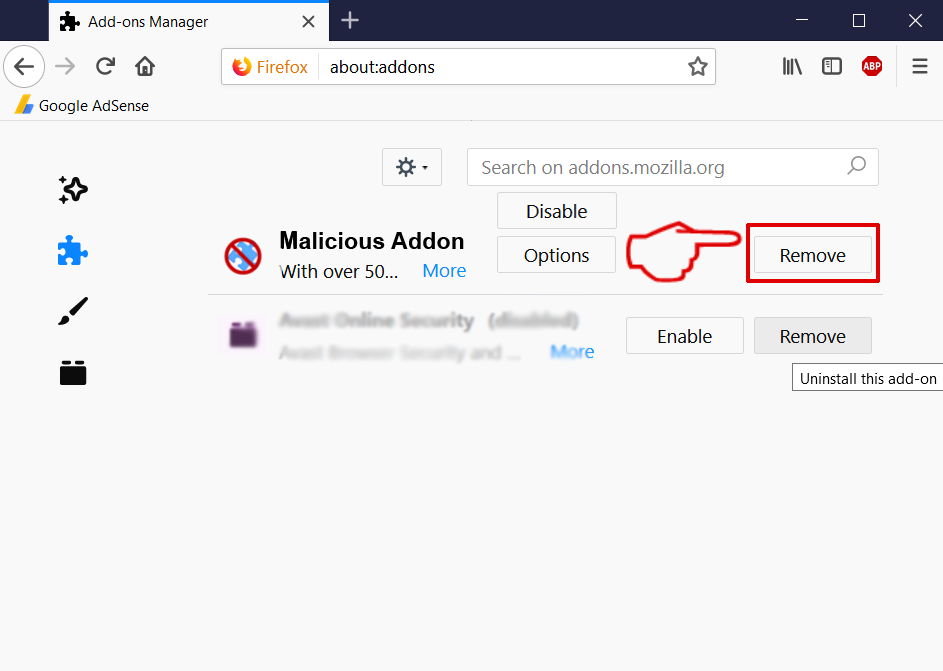
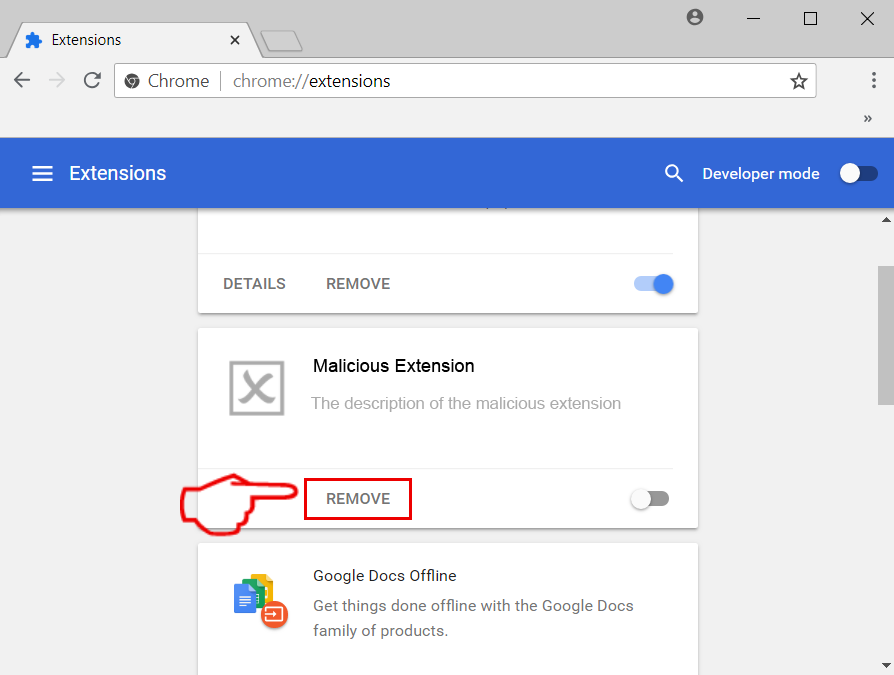
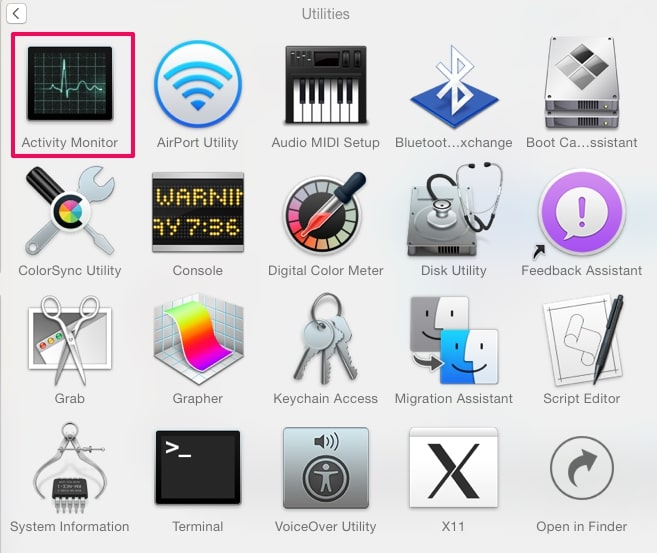
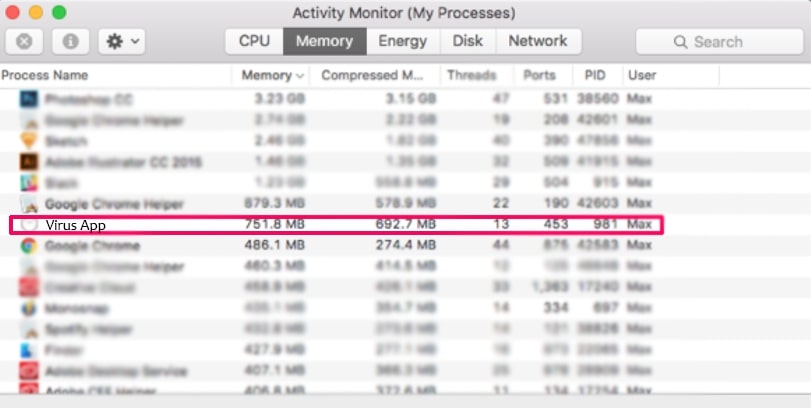
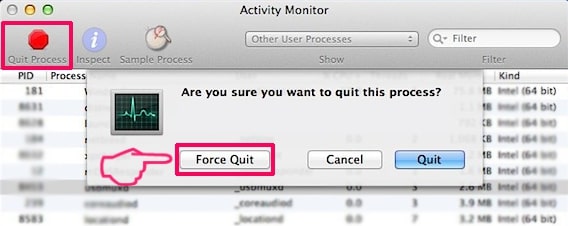
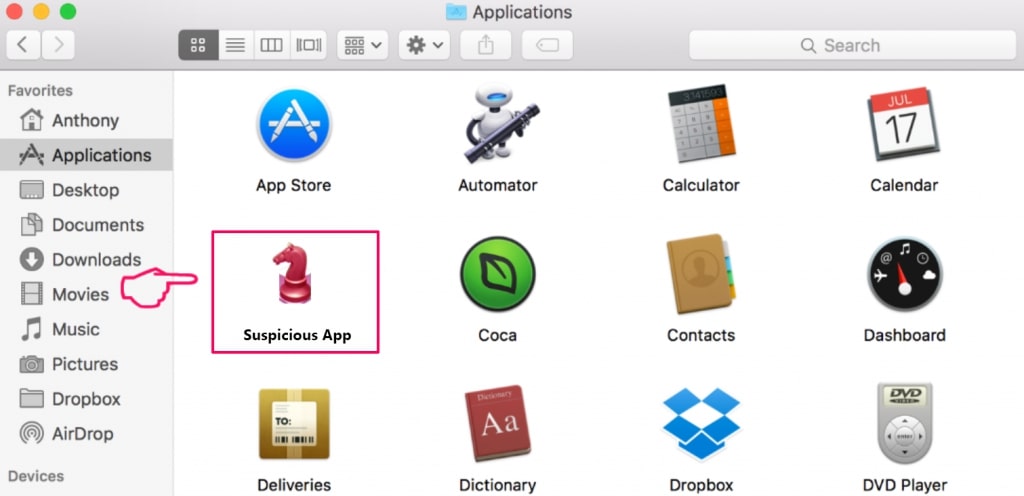
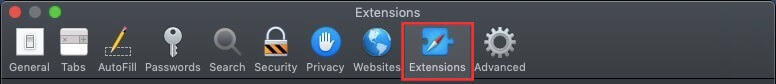
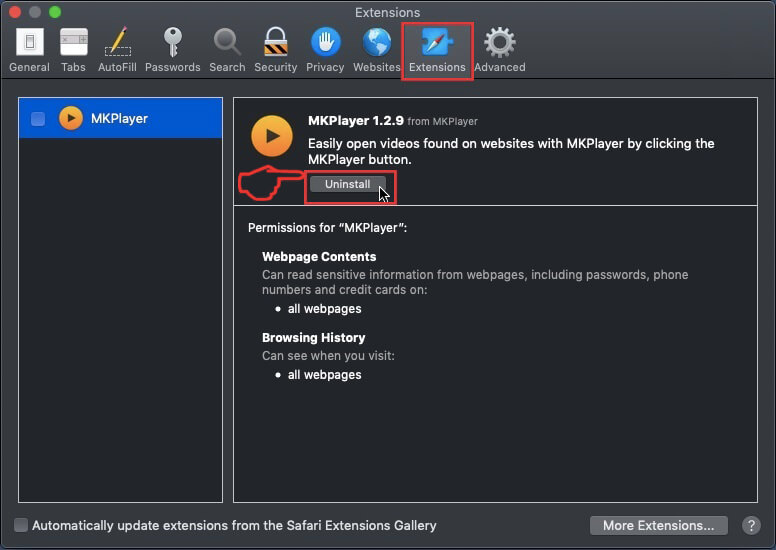
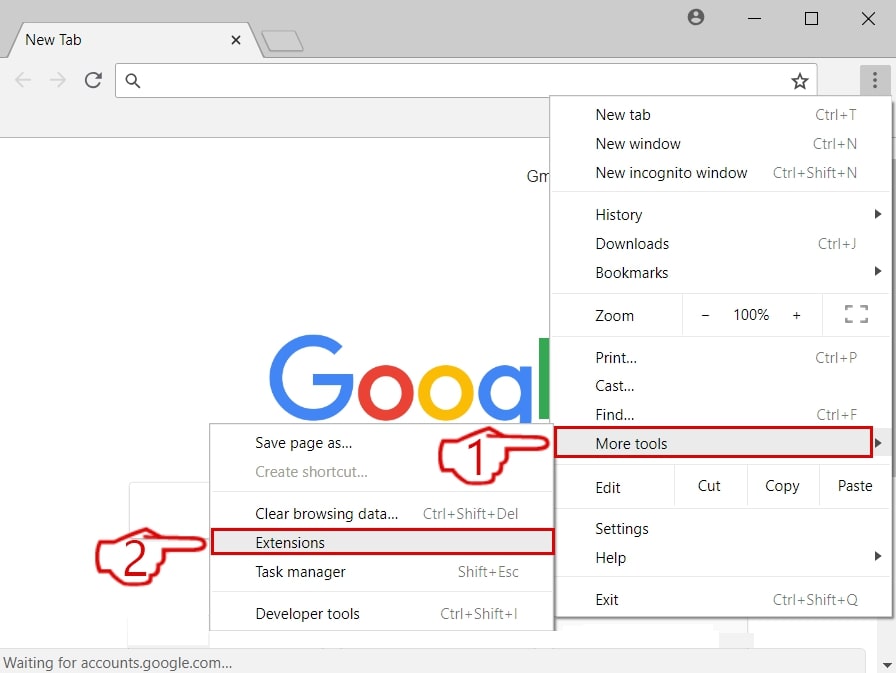
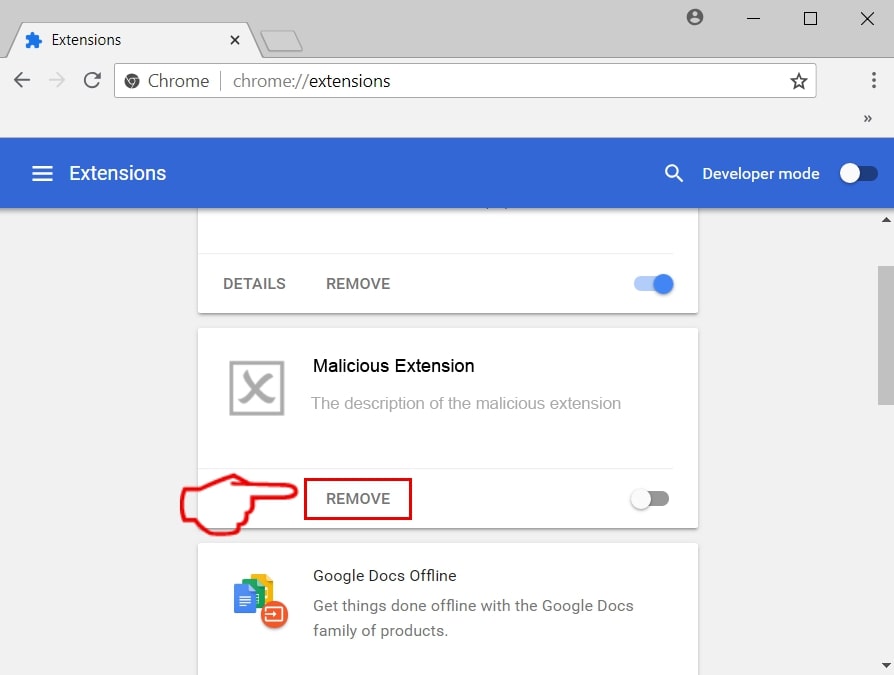
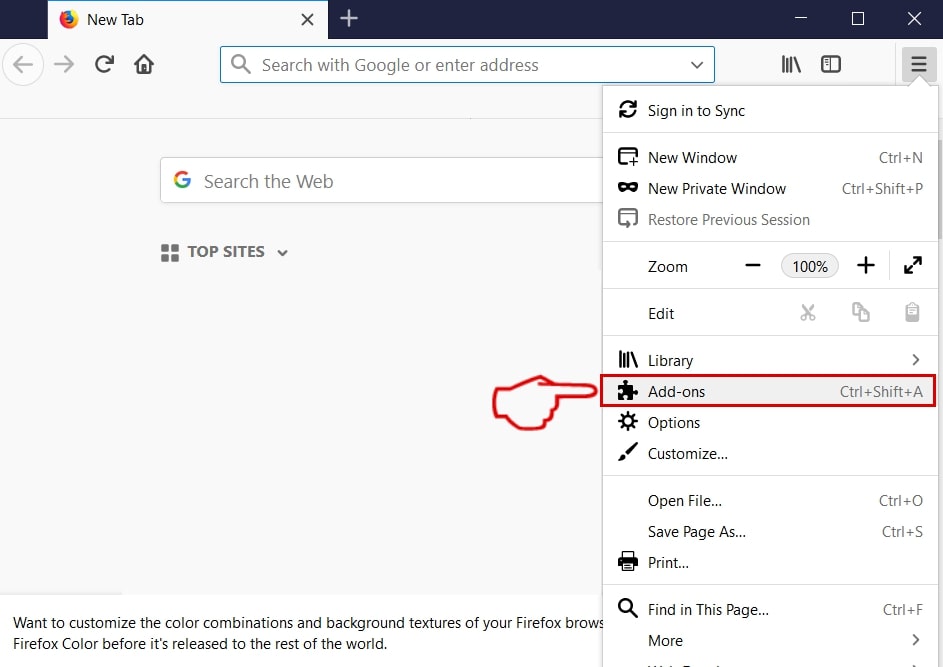
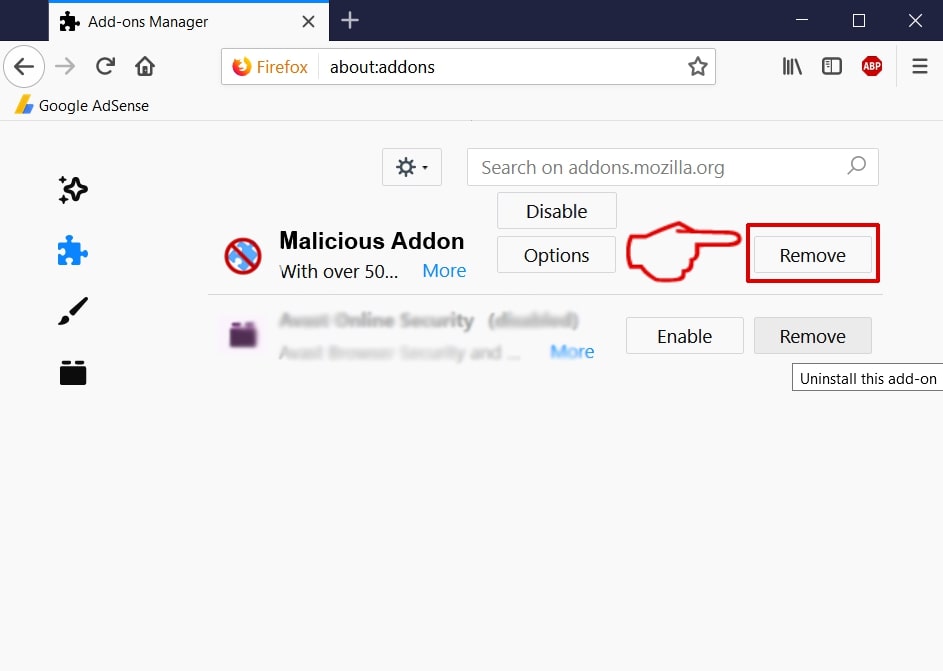
This blog post is made in order to give you insight on how to detect and remove phishing pages which are aimed at your information and it will also explain how you can remove such fake pages from your PC by eliminating the software or site that might be causing them.
So far, phishing does not show any signs of stopping, since there have been countless phishing attacks out there and many users who lack experience with phishing tend to fall for these traps and as a result either financial or personal (or both) information is lost in the process. Most antivirus companies are now actively working in cooperation with web browsers to block phishing web sites from their source hosts that are spreading the URLs at an alarming rate on a massive scale. And this rate of spread cannot seem to be stopped because of the sheer count of the new phishing pages that appear every day. This is why we have decided to provide you with information on how you can stop phishing URLs and how you can make sure that they won’t spread again on your Mac.

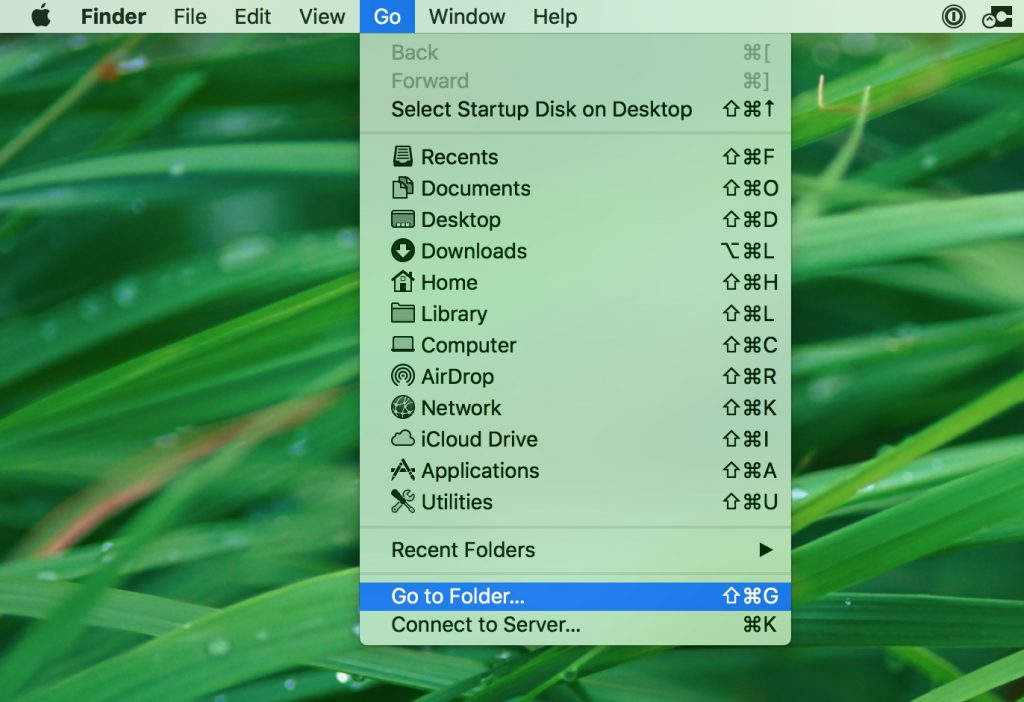
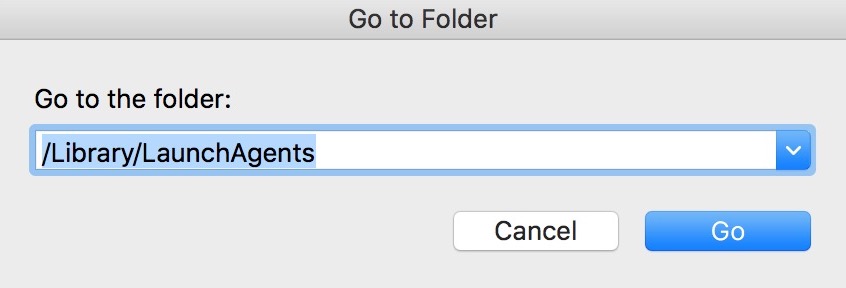
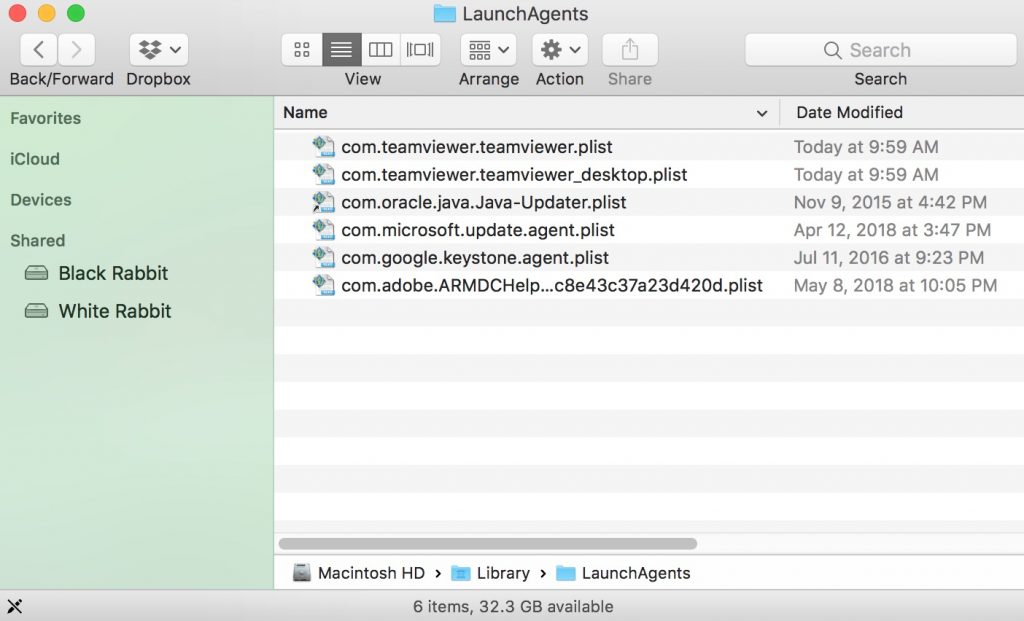
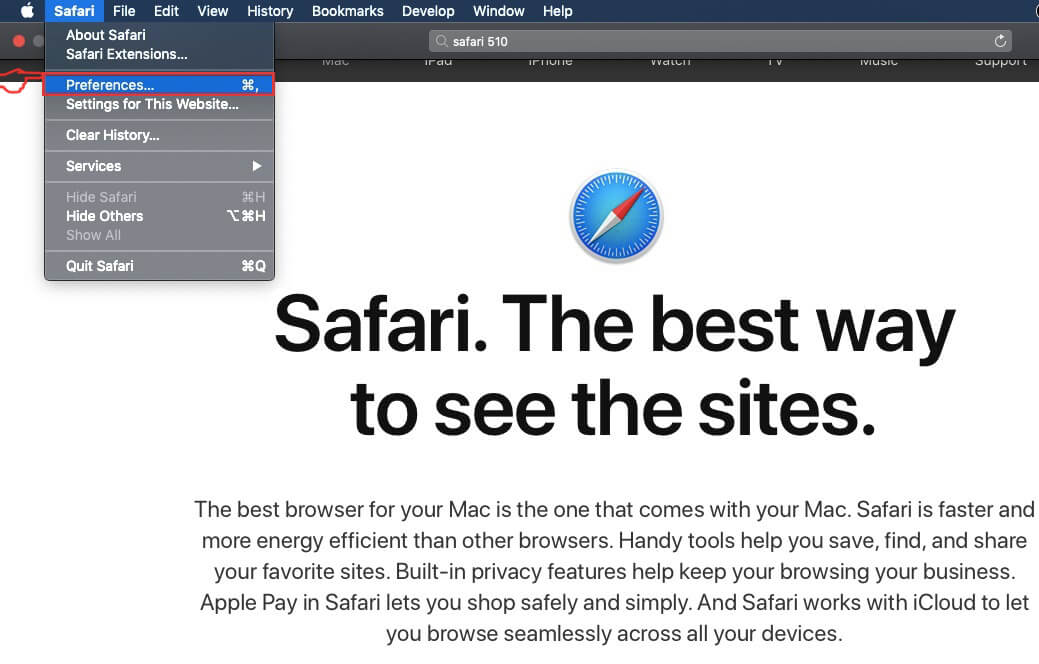
How Do Phishing Links Spread on Macs
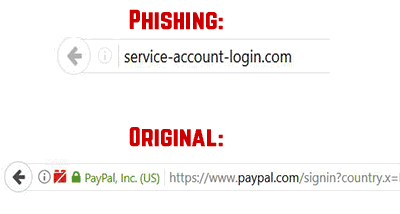
A lot of effort I put in a phishing attack to make it appear like the original site that targets the victim. Cyber-criminals go as far as to employ clever tactics to spread phishing much faster than normal, using more automated methods, like the ones underneath:
Spreading Via Referrer Spam
Some phishing sites which spread at an alarming rate have been detected to replicate web pages automatically by manipulating Google itself. They use specific Google indexing methods that are known as Web Crawlers and Ghost Referrers that attack websites and spam the phishing URLs on their comment sections and other places on the sites. Web Crawlers, one of the spam bots aim to go through various pages and look for those pages that lack specific security measures against referrer spam, like missing Captcha and so on and use these weaknesses to comment spam URLs. The other method, known as Ghosting uses more advanced and persistent software that does not spread at an alarming rate, but can remain for years on a website, since it uses more advanced tactics to remain hidden and directly connected to it. These referral spam threats are not only bad for the user, but for the website vendor as well, because the pages to which the links point are fake and can lower the website’s reputation. Here is one example of a fake versus actual referral spam redirect by clicking on a URL from a referral spam comment:

Spreading via Adware, Hijackers and Other PUPs
This method of spreading phishing web pages is possibly the most used one, because it is a quick way for the adware developer to become rich via pay-per-click schemes or even if the adware maker is the phishing attacker himself. The spreading can range from fake browser extensions, ad-supported toolbars, software, installed on your Mac and even fake web browsers. All of these unwanted apps may cause redirects that may ultimately lead to the phishing page.
And the benefits for the creators of these ad-supported programs are many as well:
- They lead automated traffic by causing redirects to the phishing site.
- They show other advertisements that eventually cause redirects to malicious web pages in some cases.
- They display phishing pages that aim to steal passwords and usernames.
Such phishing pages can be shown as a result of a web browser redirection or via a fake web page that is posted on a toolbar as some sort of a bookmark. This includes fake login pages, like Facebook imitation login pages, PayPal, Amazon, Apple, LinkedIn and many other phishing scams.
Such unwanted programs are often spread as a result of software bundling, where the application in question is advertised as an included program that is also a useful one and a free offer alongside the current installation. The bad news here is that such bundled applications could be seen on suspicious download sites, or torrent websites. They cannot be easily located, since their installation step often resides In the “Advanced” or “Custom” install modes, looking similar to the example image below:
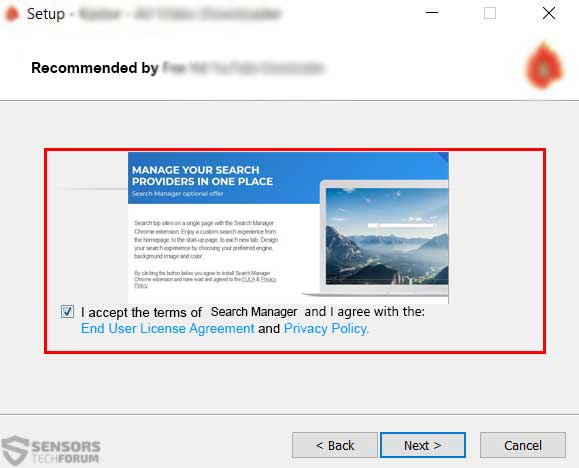
When it comes to Mac users, the outcome of this is fake web pages that demand to log into services, like iCloud and others, while displaying very well disguised web pages, that look close to the original ones:
Spreading via Viruses and Other Malware
The best method that will definitely result in a lot of phishing pages to appear on your Mac unobstructed is via phishing attacks as a result of malware infections. These types of infections are usually Trojan horses that are modified to display ads. These threats are commonly reffered to as Trojan.Clickers and they often tend to cause a lot of automated redirects to different pages when the victim visits them. One good example is if you try to access PayPal and the virus detects it and as a result you are displayed a fake PayPal web page. The same goes of Dropbox, which was recently the center of attention for many phishing attempts.
Related: Dropbox Phishing Scams and Malware E-Mails – Remove and Stop Them
Spreading Via Phishing E-mails
Another very well known and often used tactic to spread Phishing pages by sending e-mail spam messages that appear very close to the original ones. According to a research, conducted back in 2017, the most targeted users for phishing are users that belong to Banking sites, electronic payment sites and telecommunications, so the attackers definitely know what they are doing.
Related: Apple Phishing Season Is Here And Users Are At Risk
And they are very clever on how they perform the phishing schemes as well, since they send very cunning e-mails that imitate the original e-mails very closely:
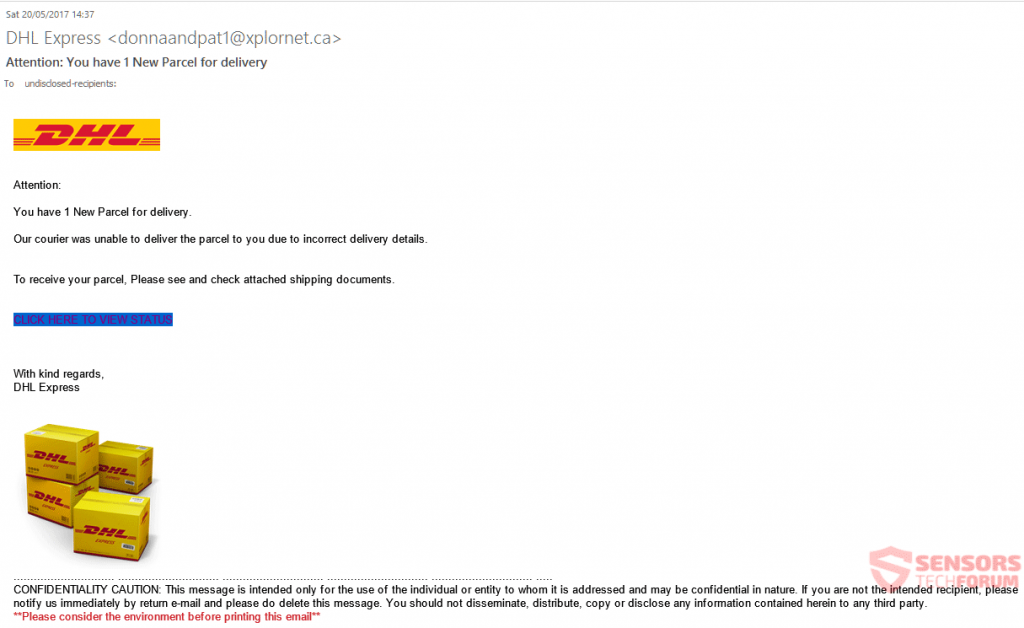
The e-mails often stress important issues in order to convince victims to give away their vital credentials. The most widespread subjects that are extremely convincing are:
- Logged in account from another device.
- Unauthorized PayPal transfer.
- Suspicious activity on the victim’s account.
- Purchasing receipt the victim has not made.
And the body of such e-mail contains images of the company that are basically the same as the original ones that are sent from the company itself, having logos, links to the web pages and even options to unsubscribe, just like in the real ones. And the websites they lead to may not always be blocked by antivirus software, so victims might be thinking “Yes, I have an antivirus, so I’m safe.”, but sadly, that is not always the case.