Mongo Lock is a new attack that is aimed at MongoDB databases which have no protection and remote access left open. Mongo Lock is a ransomware threat, which wipes these databases and uses extortion tactics like any other ransomware to try and trick the victim parties to pay a ransom fee for supposedly recovering their files.
Mongo Lock and its Modus Operandi
MongoDB databases have been targeted in the past, so it is not surprising to see a new campaign targeting them. The ones standing behind the attacks either scan the World Wide Web or use services similar to Shodan.io to find MongoDB servers which are not secure. If the attackers connect successfully and get inside a server, they could export or delete databases and then leave a ransom note with instructions on how to allegedly restore those databases.
Bob Diachenko – the security researcher who first discovered this new Mongo Lock campaign shares that attackers will connect to an unprotected database and simply erase it. A new database called “Warning” with a collection inside it named “Readme” will be left in place of the old database. As one could guess, that Readme collection contains the ransom message which claims that the database has been encrypted and that the victims need to pay up if they want it restored. The recent Mongo Lock campaign does not reveal a Bitcoin address, but directs victims to contact the cybercriminals through an email address.
The ransom note of the Mongo Lock ransomware threat is displayed below:
The note states the following:
Your database was encrypted by ‘Mongo Lock’. if you want to decrypt your database, need to be pay us 0.1 BTC (Bitcoins), also don’t delete ‘Unique_KEY’ and save it to safe place, without that we cannot help you. Send email to us: mongodb@8chan.co for decryption service.
Other attacks will show the Bitcoin address that should be used for paying the cybercriminals before contacting them through the included email address. That can be seen in the text given down here:
“BitCoin” : “3FAVraz3ovC1pz4frGRH6XXCuqPSWeh3UH”,
“eMail” : “dbbackups@protonmail.com”,
“Exchange” : “https://www.coincola.com/”,
“Solution” : “Your Database is downloaded and backed up on our secured servers. To recover your lost data: Send 0.6 BTC to our BitCoin Address and Contact us by eMail with your server IP Address and a Proof of Payment. Any eMail without your server IP Address and a Proof of Payment together will be ignored. We will drop the backup after 24 hours. You are welcome!”
Although the ransom note claims that the criminals behind Mongo Lock are exporting the database before its deletion, it is unknown if that is exactly what happens.
What Aftermath Does Mongo Lock Leave?
According to Diachenko, it appears that the attackers are using a script that automates the process of accessing a MongoDB database, possibly exporting it, deleting the database, and then creating the ransom note. Bob Diachenko admits that the script used by Mongo Lock fails to complete its job and that is a flaw in its design. The thing is that, fortunately, sometimes data is left unlocked and accessible to users, regardless that a ransom note message is present.
Such types of attacks are able to occur due to the fact that the MongoDB database is accessible remotely and not secured in a proper manner. Thus, attacks can easily be prevented by following some quite simple steps in securing the database servers. MongoDB has already issued a great article on how to make a database secure, while also offering a security checklist for administrators one can follow. Restricting remote access to the databases and allowing authentication are probably the two single most crucial steps that one can take to prevent
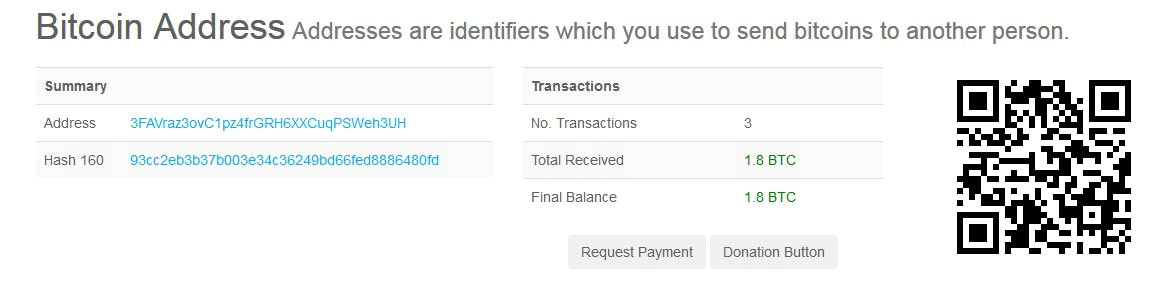
If you look up Bitcoin addresses used in MongoDB attacks, victims have been paying the ransom fees. For example, the address 3FAVraz3ovC1pz4frGRH6XXCuqPSWeh3UH is shown below:
That particular Bitcoin address is often used in the ransom notes and checking it indicates that it already holds the money of payments from three different Mongo Lock ransomware victims. The total sum inside the address equals 1.8 Bitcoin which is around 11,000 US dollars if the most current value of Bitcoin is considered.