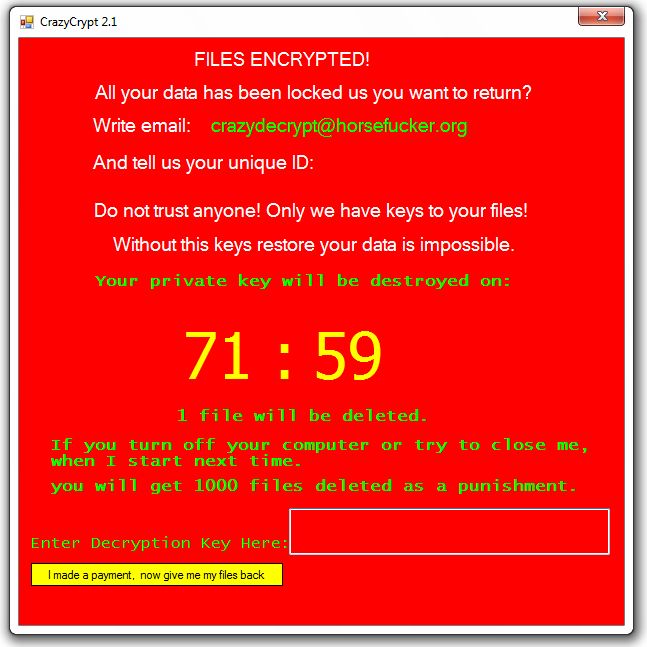
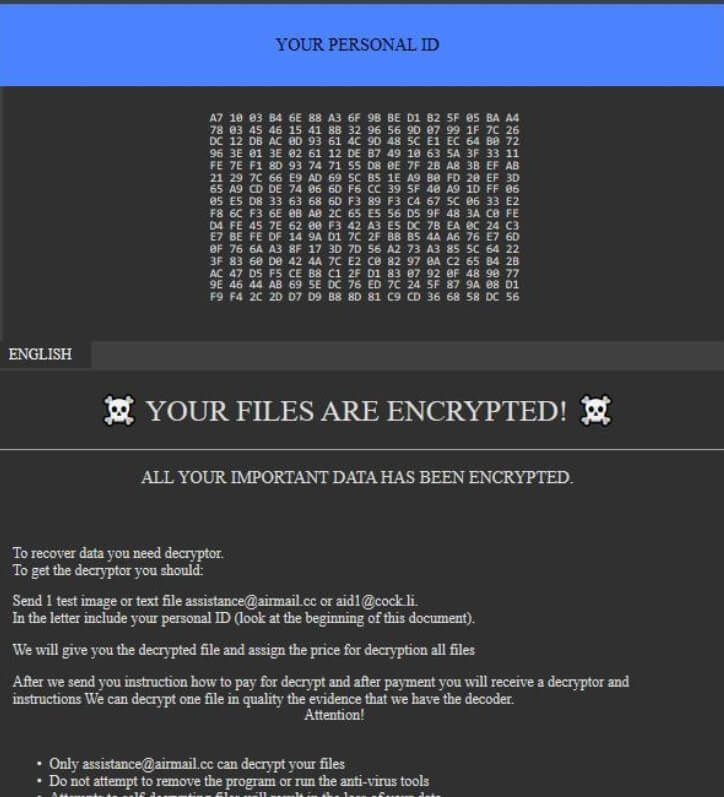
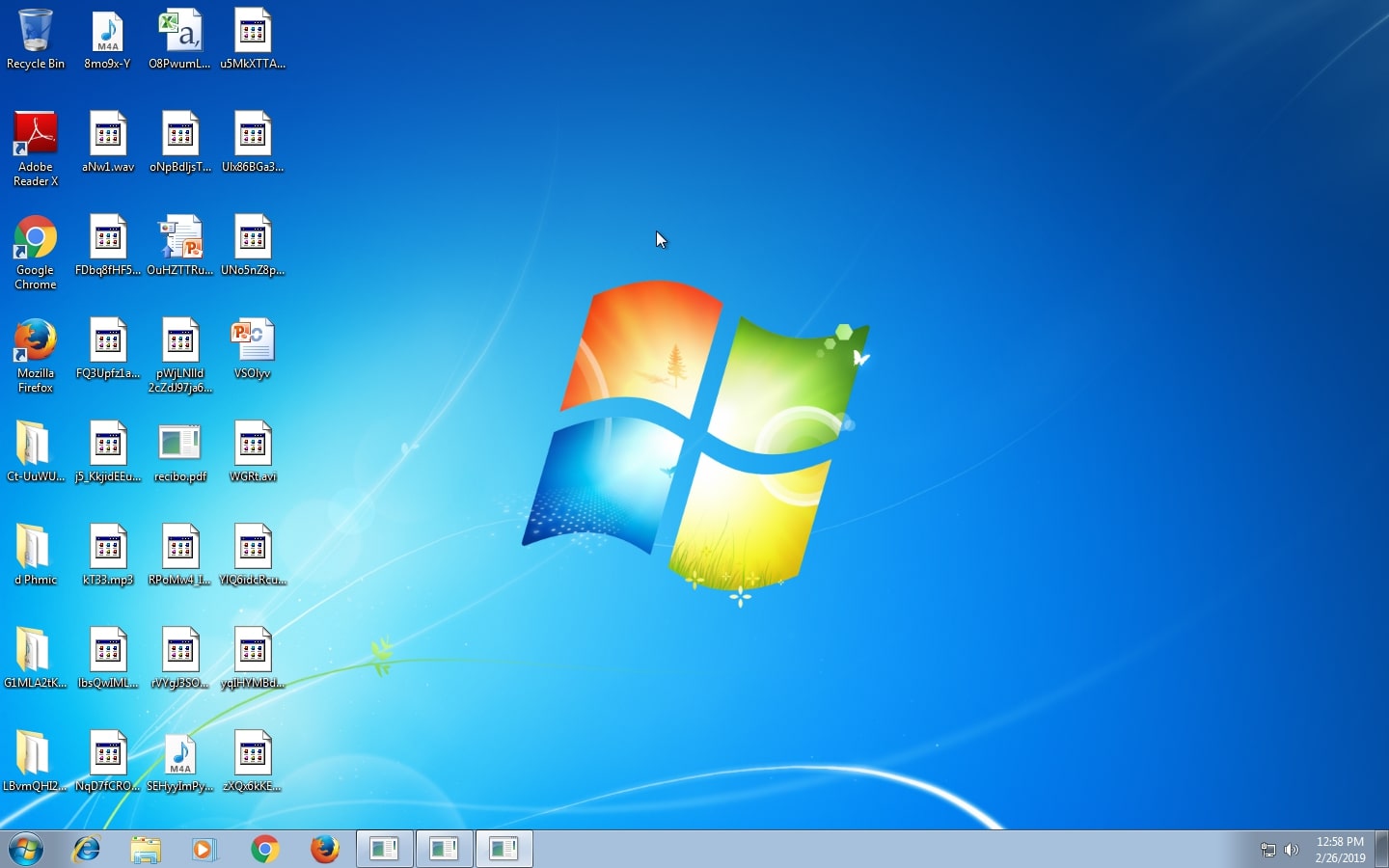
Vulnerabilities in SHAREit Android App Could Have Your Files Stolen
Two high-severity flaws were discovered in the popular SHAREit app which has more than 1.5 billion users. The app is available for Android, iOS, Windows and Mac, but the two flaws were located in the Android version which has more…