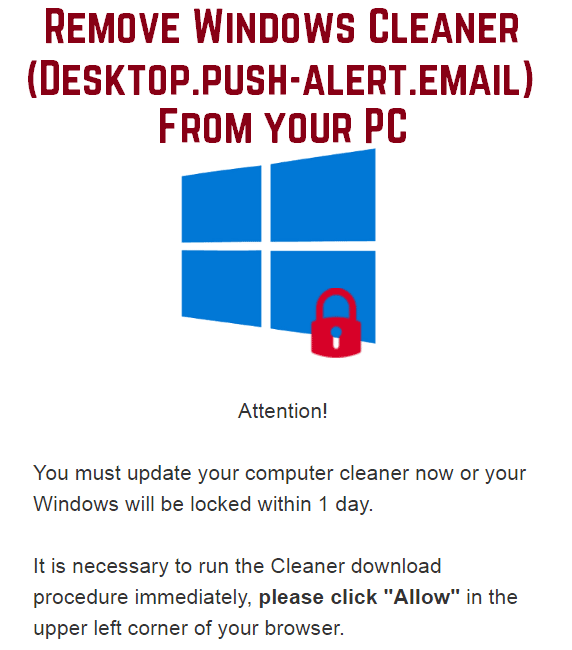
CVE-2018-16593: Critical Sony Bravia TV Vulnerabilities Discovered
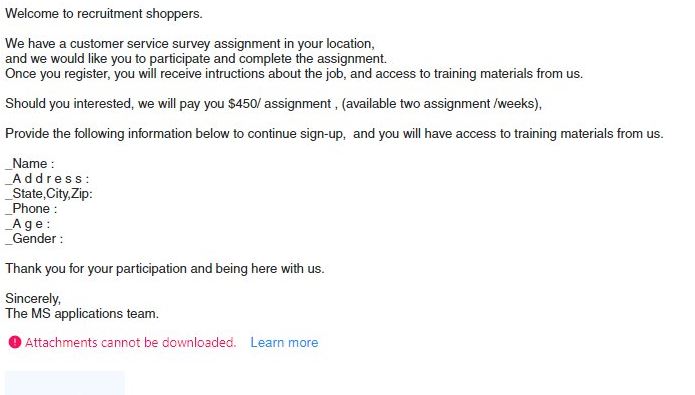
A dangerous Sony Bravia TV vulnerability has been found to affect several of the popular models of the range. The security researchers that alerted of the issue note that a series of other bugs were found as well. Our articles…