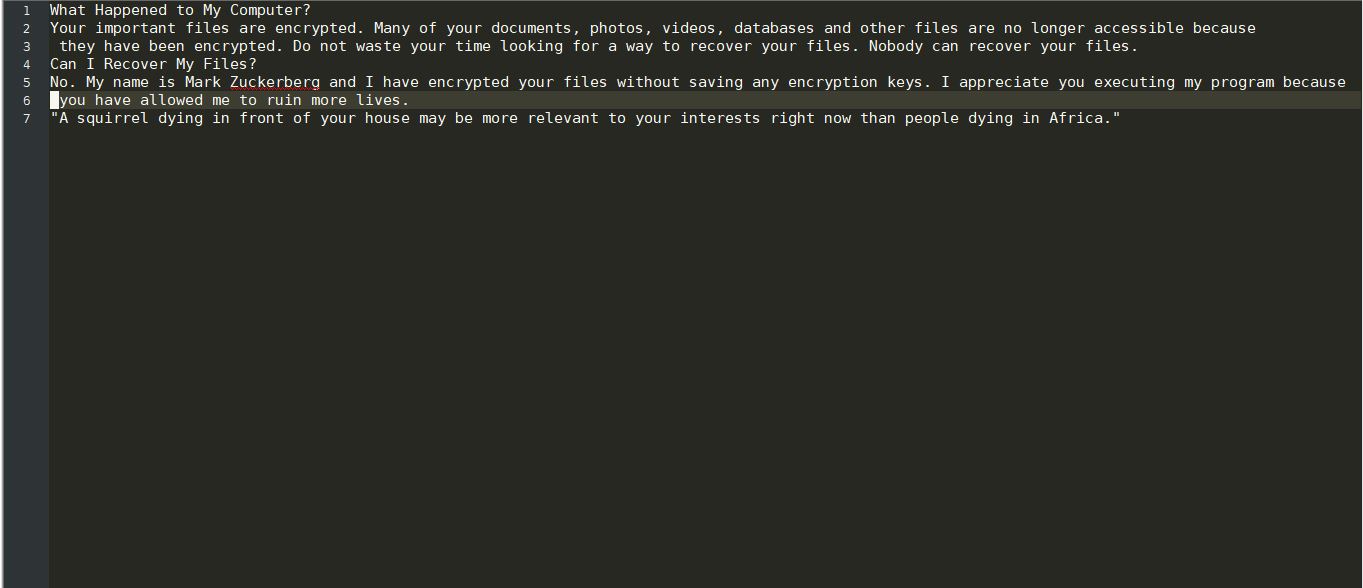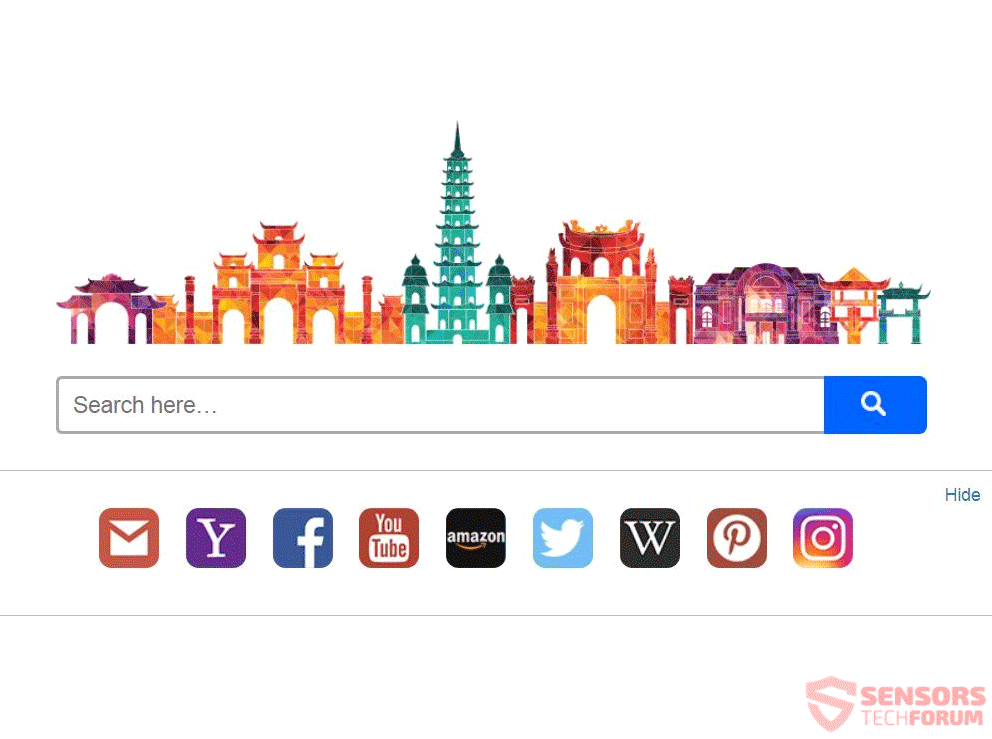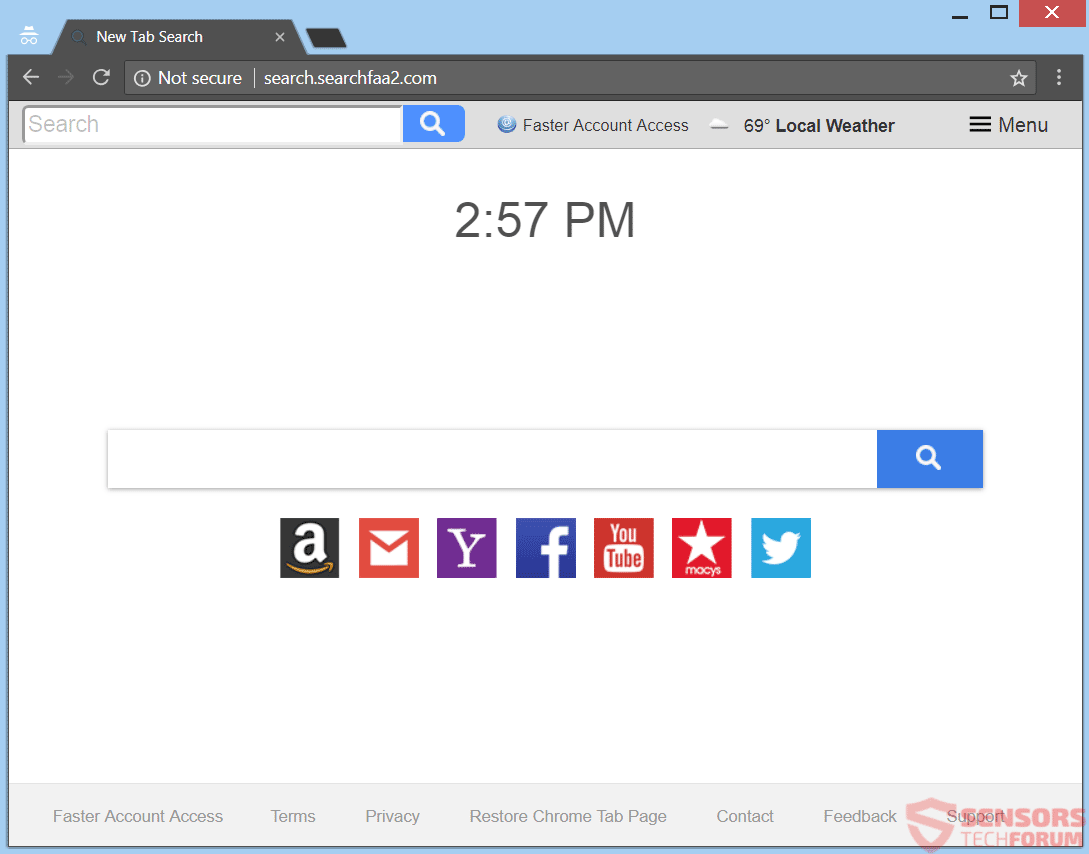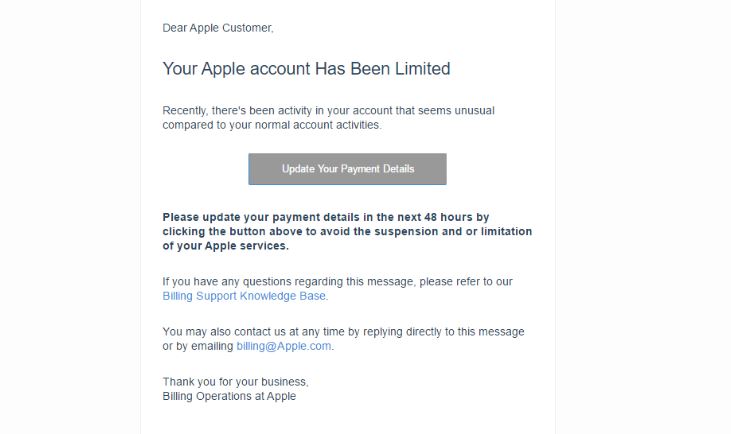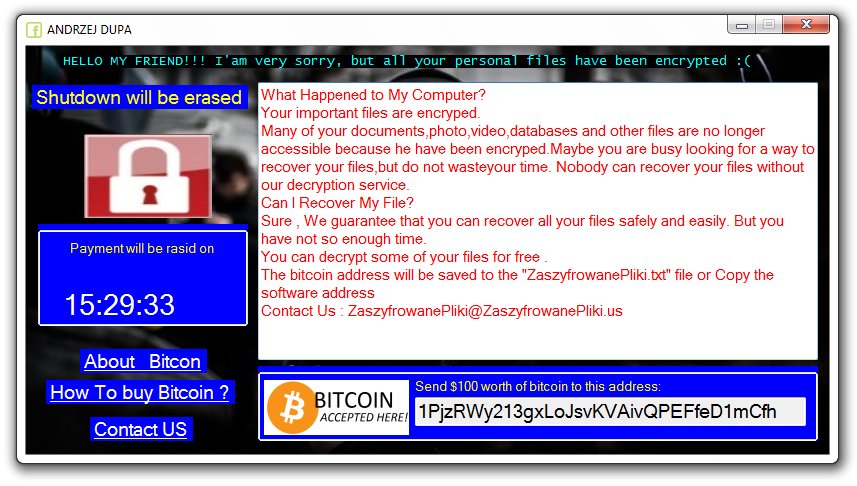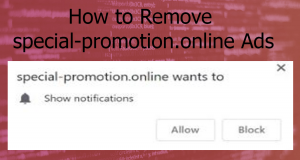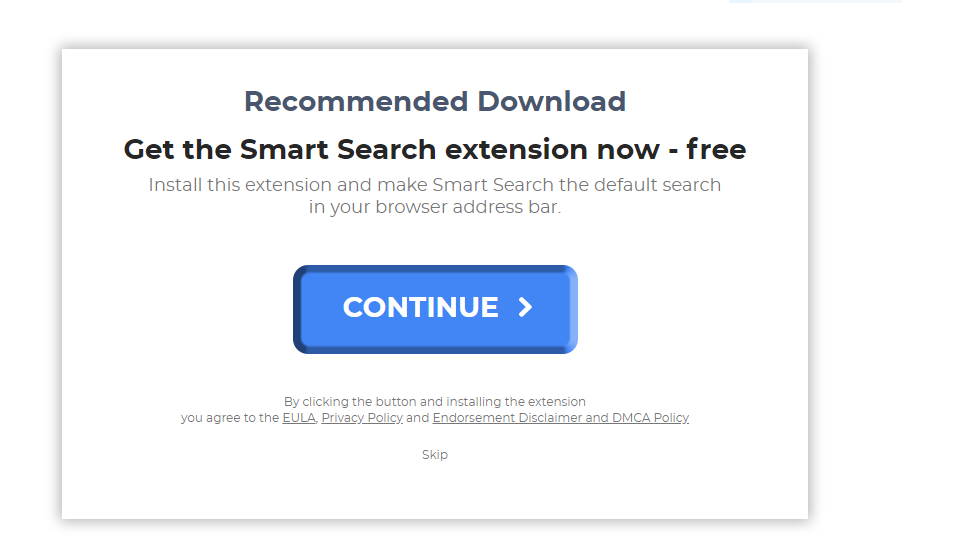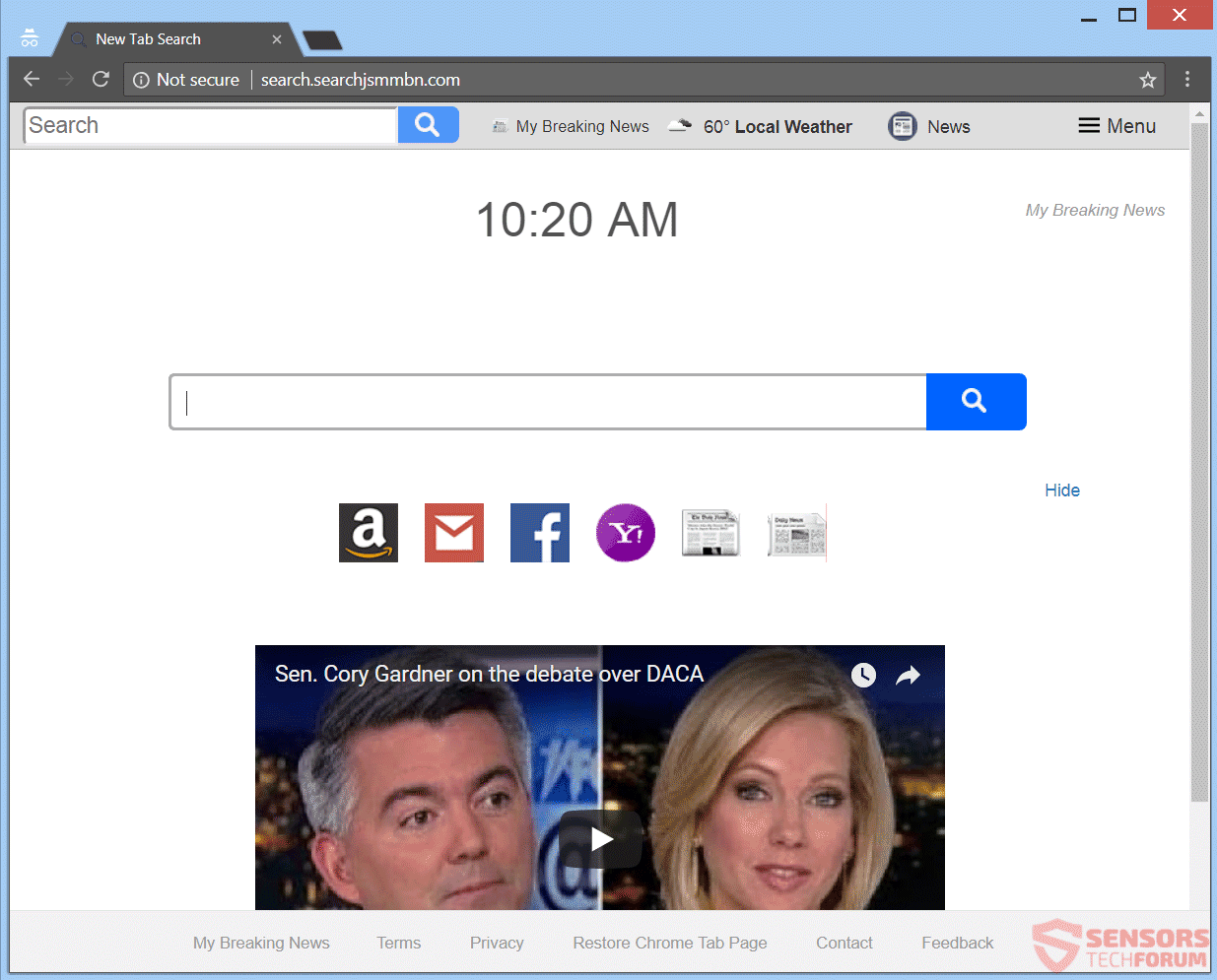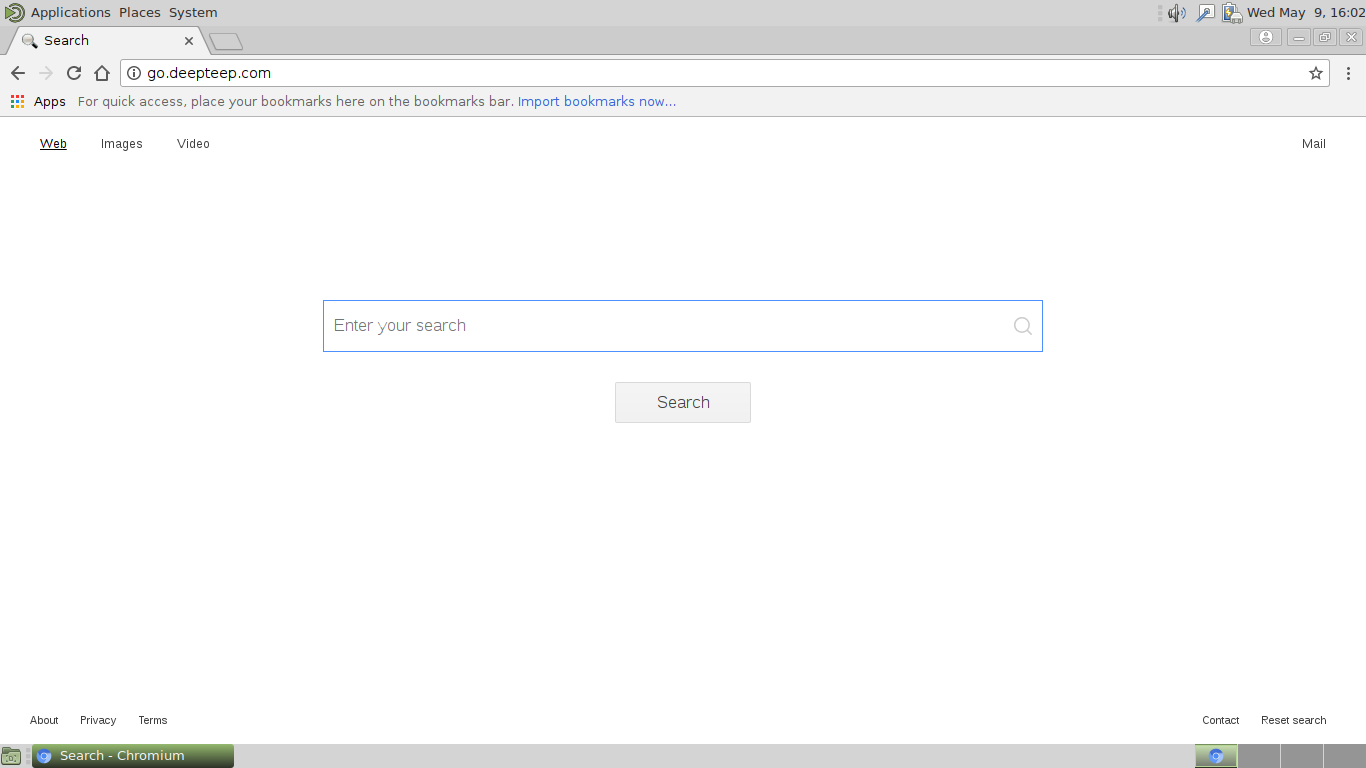
Gorlita.com Redirects “Virus” – How to Remove It Fully
This article has been created in order to explain what is the Gorlita.com – related software, causing browser redirects and how to remove this unwanted program from Android and your PC. A new browser redirection software in association with the…