A new ransomware was discovered on a Healthcare network by Carbon Black security researchers. The ransomware is dubbed PowerWare, and it uses Windows PowerShell to deploy its payload. It is spread via emails containing a Microsoft Word document with an invoice message inside it. Enabling editing on the document releases the payload as a script of commands in PowerShell, thus avoiding creating new files and consequently, detection.

Threat Summary
| Name |
PowerWare |
| Type | Ransomware |
| Short Description | The ransomware uses Windows PowerShell to deploy its payload. |
| Symptoms | The user’s files are encrypted and unusable. |
| Distribution Method | E-mails and attachments. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
| User Experience | Join our forum to discuss PowerWare. |
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |

How Does PowerWare Ransomware Spread?
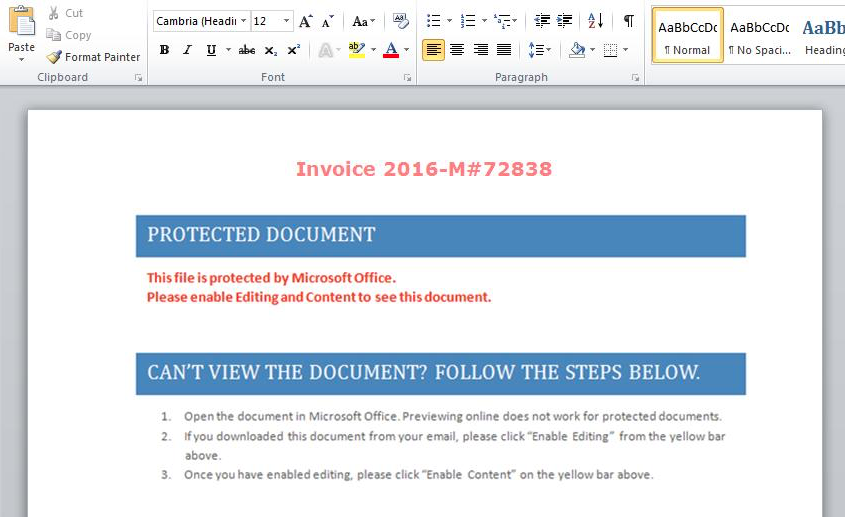
PowerWare ransomware is spread through e-mails. These emails are very well written and contain a Microsoft Word document as an attachment. Perhaps e-mails which are written with proper grammar are the main reason more people fall for the deception, compared to others. The Microsoft Word document includes the following invoice message:
Image Source: carbonblack.com
The invoice wants you to enable the editing feature in Microsoft Word so that the payload can be released. As that feature is inbuilt like Microsoft Word and PowerShell themselves, the malware avoids detection.

Technical Information about PowerWare Ransomware
The most unique thing about PowerWare is that it is a fileless ransomware. We have seen fileless malware before in the form of the Poweliks Trojan and a version of the Angler Exploit Kit for example.
Fileless, as in staying hidden in memory and creating absolutely no additional files for its payload to be executed. Instead, the Microsoft Windows PowerShell program is used to encrypt files. This happens with the help of macro commands embedded in a script, loaded into PowerShell. Random numbers are used as an individual encryption key. The key, along with a generated URL for where to pay the ransom are both sent back to the cybercriminals. That information is written in plain text, so people with a full packet capture device should be able to access it and recover their files.
In the unfortunate event of encryption, all file locations will be scanned thoroughly by the PowerWare ransomware. The files that can be encrypted are with the following extensions:
Image Source: carbonblack.com
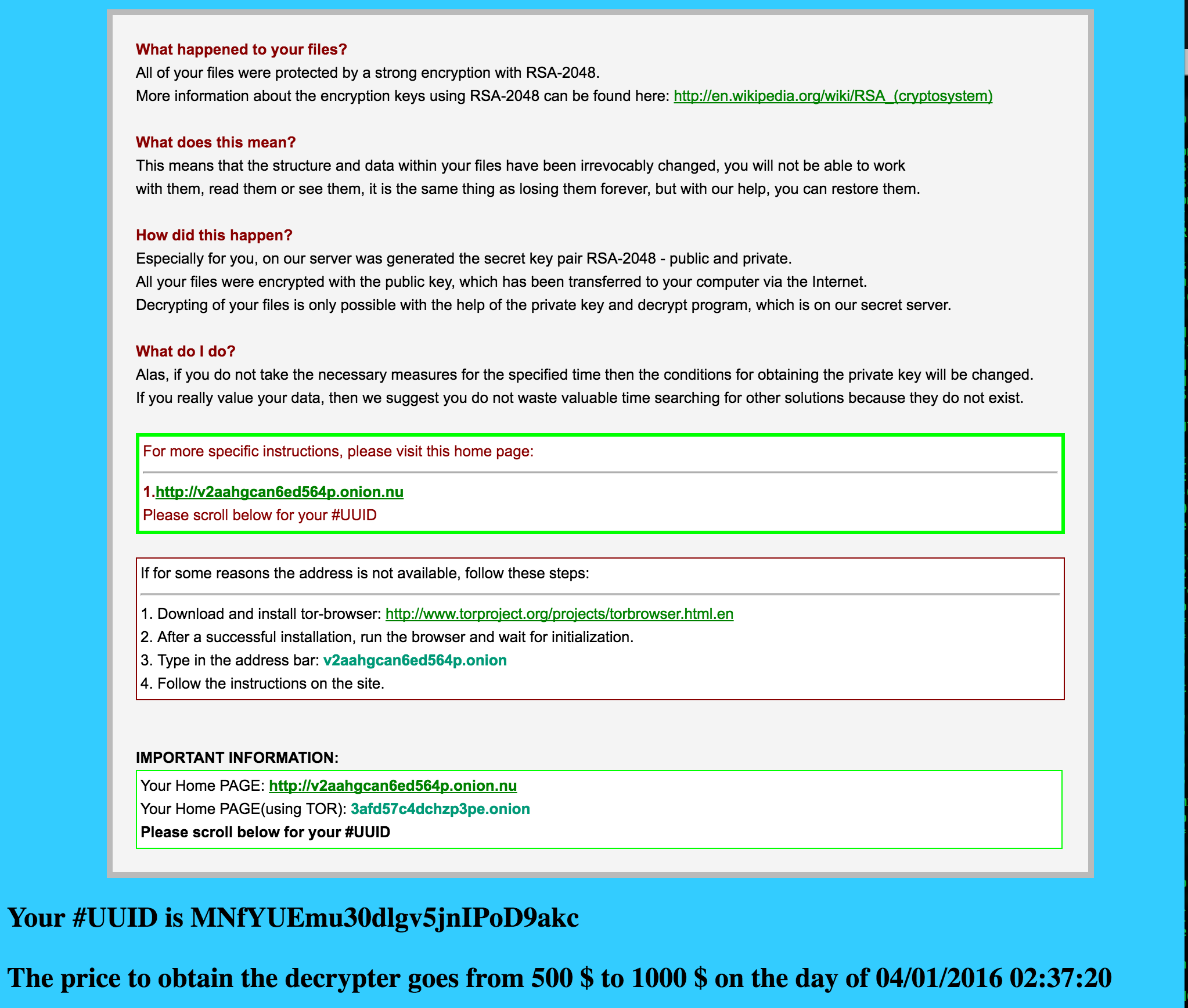
After completing the encryption, you will see instructions describing how the ransom to be paid. The ransom note, first seen on CryptoWall 3.0 is used and looks like this:
Paying the ransomware makers is NOT advised. No one can guarantee that you will get your files decrypted. The money will be spent on creating more malware or for other nefarious deeds.

Prevent PowerWare Ransomware from Infecting You
If you are infected by PowerWare ransomware, the commands are executed and there is nothing to be removed. In case you are not infected, you should have an anti-malware tool installed as a prevention method. Malware specialists should have set the new definitions for the known Word documents containing the malicious script.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter