Researchers with Symantec have identified a new highly advanced espionage malware, dubbed Regin, used in attacks against numerous international targets, ranging from private individuals to businesses, and governments. The degree of technical competence displayed by Regin can be rarely seen, according to the experts at Symantec. Their research points out that Regin may be one of the key “cyber espionage tools used by a nation state.”
Regin’s Platform, Modules, and Tools
Regin is a platform with numerous modules, capable of seizing full remote control of the target’s network at all possible levels. Modular platforms like Flame and The Mask/Weevel have been detected before, but Regin uses a multi-stage loading technique which is reminiscent of the Duqu/Stuxnet family, according to Symantec’s team. In terms of functionality, design of the platform or flexibility Regin is much more complex than Stuxnet and Flame.
One of the more compelling modules allows Regin to monitor GSM base station controllers. Experts with Kaspersky Lab report that in April 2008, the attackers got their hands on administrative login credentials which allowed them to “manipulate” a GSM network in a Middle Eastern country. The experts did not specify which one exactly. Having full access to the base controllers, the attackers are able to redirect calls or even shut down the entire mobile network.
Regin includes different tools and uses a highly stealthy communications method to control the affected networks. It involves the victimized organizations communicating via a peer-to-peer network.
The compromised machines communicate through HTTP and Windows network connections. This allows the authors behind Regin to dig deep into the targeted networks, avoid air gaps, and control the traffic to the C&C server in order to remain undetected.
The standard capabilities of Regin include a few RAT features, like:
The Stages of Regin
Regin is a multistage malware and all stages except for the first one are hidden and encrypted. According to the report published by Symantec “, the initial stages involve the installation and configuration of the threat’s internal services. The later stages bring Regin’s main payloads into play. The most interesting stages are the executables and data files stored in Stages 4 and 5. The initial Stage 1 driver is the only plainly visible code on the computer. All other stages are stored as encrypted data blobs, as a file or within a non-traditional file storage area such as the registry, extended attributes or raw sectors at the end of the disk.”
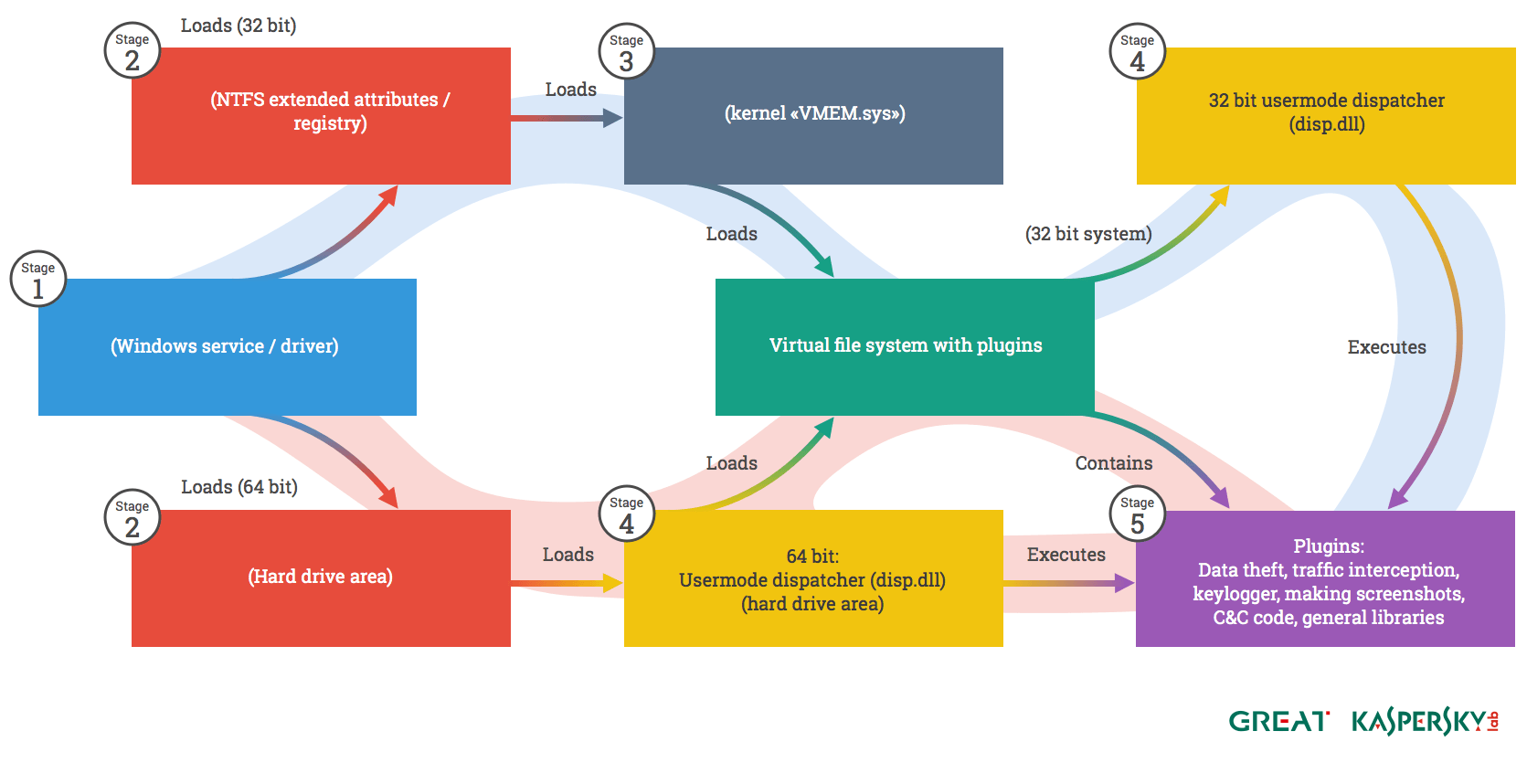
Stage One – This is the only executable file which appears in the system of the victim.
Stage Two – This stage has numerous purposes. It can remove the infection from the compromised system in case it becomes such instructions in Stage 3. In this stage, a marker file is created which allows the infected machine to be identified.
Stage Three – This stage can only exist on 32bit systems. On 64bit systems the dispatcher is loaded directly, making the third stage unnecessary.
Stage Four – The Dispatcher. This is the user-mode core of the framework and probably the most complicated single module in the whole platform. The dispatcher is responsible for the most complex tasks on the platform, like basic communications, network transport sub-routines, storage functions, providing an API in order to access virtual file systems.
Kaspersky Lab provides detailed information about each stage in their paper on the Regin malware.
Regin’s Distribution Method Is Still Unclear
Researchers are still not able to determine how the targeted computer gets initially infected with Regin. So far, no concrete zero-day exploits or any other methods have been confirmed. It is highly possible that the attackers use a range of initial attack vectors. Regin has minimum a dozen diverse exfiltration options.
Plausible options are a link, a drive-by, or an executable sent in an email. Symantec experts suspect that the dropper at Stage 0 is presumably never resident on the affected machine.
Regin’s Targets
Researchers report that Regin has been used in 10 countries. The main targets seem to be Russia and Saudi Arabia, but traces of the infection have been detected in India, Ireland, Afghanistan, Mexico, Belgium, Iran, Pakistan and Austria. At first, Regin was used in espionage campaigns against numerous organizations from 2008 to 2011. Then it was suddenly withdrawn, and a new version appeared last year. Almost half of the identified Regin infections were targeting small businesses and private individuals. The main purpose of the attacks on the telecommunication sector obviously was to gain access to calls that were routed through that infrastructure.
The victims of the Regin malware can be assigned to these categories:
- Individuals involved in advanced mathematical/cryptographic research
- Financial institutions
- Research institutions
- Multinational political bodies
- Telecom operators
- Government institutions
The Origin of Regin
As to the origin of the malware, researchers with F-Secure are certain that Regin is not created in Russia or China. Given the resources required to design such a malware, and the type of operations Regin supports, experts believe that the attackers behind it most probably involve nation-state.

