The SyncCrypt ransomware is a newly identified threat that is now being distributed in a worldwide spam attack wave. The hackers behind the threat coordinate template-based email messages that include payload files that lead to the dangerous infection.
SyncCrypt Ransomware Is a Newly Discovered Malware Threat
The first instances of the SyncCrypt ransomware were identified last week (August 2017) and the captured samples showcase that the malware is a serious threat to vulnerable computer users and their machines. According to the analysis this is a feature-rich ransomware that is able to encrypt both system and user data according to a predefined behavior pattern. The criminals behind the malware are using social engineering tricks to manipulate the targets into infecting themselves with the SyncCrypt ransomware code.

Current versions are configured and launched against potential targets via a large-scale worldwide attack. The cyber security experts were able to obtain live samples from the intrusion attempts which give insight on the current goals of the hackers. At the moment no information is available about its potential code source. It is very likely that it has been devised by its creators from scratch. In addition the identity of its makers is also not known, it could be a single hacker or a whole criminal collective.
SyncCrypt Ransomware Distribution Tactics
SyncCrypt Ransomware is delivered to customers worldwide using several strategies. All of them are made in a way that seek to increase the infection ratio as much as possible. The main tactic at the moment seems to be the full-scale email attack campaign. The current wave uses messages that pose as being sent by government institutions. The captured samples pretend to be court orders disguised in several different types of files. The messages may include text or elaborate body contents to capture the attention of the intended victims. In other cases the file attachments are presented directly without any text in a WSF format.
Active SyncCrypt infections can effectively be removed only with a capable anti-spyware solution, refer to our removal guide for an in-depth guide.
The WSF files are used by the Microsoft Windows Script Host which is able to execute a wide range of different scripts. Depending on the sent strains the criminals may utilize several infection techniques:
- Scripts containing the malicious code in themselves. They are usually the simplest forms of viruses that are the easiest to detect by security software.
- Scripts that download the malware from a hacker-controlled site.
- Complex infection mechanisms that use a series of payloads that deliver the final ransomware.
The current attack campaign uses a complex infection mechanism that delivers the final SyncCrypt ransomware as a result. The captured samples download an image from a hacker-controlled site that features an embedded archive in a ZIP file. The file is then unpacked on the local machine which leads to the SyncCrypt ransomware. This complex infection route effectively bypasses several anti-virus detection mechanisms. If a victim attempts to open one of the image files they will see a cover of a music album ‒ “& They Have Escaped the Weight of Darkness” by Olafur Arnalds.
SyncCrypt Ransomware Infection Process
Once the malicious files are deployed to the victim computers the malware is extracted revealing a series of files ‒ sync.exe, readme.html and readme.png. The image file is moved to the Windows temporary folder under a randomly-named ZIP file. The other files are placed in a subdirectory “BackupClient”. This is a reference to popular software that are used to generate backups from the machine. The hackers often use such names to fool the users that they have installed a legitimate software on their computers. The final executable file is launched and this starts the actual SyncCrypt ransomware process.
The captured samples associated with the virus follow the standard ransomware infection patterns by starting an encryption engine. It uses the powerful AES cipher which targets both user and system files. This is done according to a built-in list of target file type extensions. The hackers can configure it based on the intended targets. The current samples processes the following extensions:
accdb, accde, accdr, adp, ach, arw, asp, aspx, backup, backupdb, bak, bat, bay, bdb, bgt, blend, bmp, bpw, cdf, cdr, cdr3, cdr4, cdr5, cdr6, cdrw, cdx, cer, cfg, class, cls, config, contact, cpp, craw, crt, crw, css, csv, d3dbsp, dbx, dcr, dcs, dds, der, dif, dit, doc, docm, docx, dot, dotm, dotx, drf, drw, dwg, dxb, dxf, edb, eml, eps, fdb, flf, fpx, frm, gif, gpg, gry, hbk, hpp, html, hwp, jpe, jpeg, jpg, kdbx, kdc, key, jar, java, laccdb, latex, ldf, lit, lua, mapimail, max, mbx, mdb, mfw, mlb, mml, mmw, midi, moneywell, mocha, mpp, nef, nml, nrw, oab, odb, odc, odf, odg, odi, odm, odp, ods, odt, otg, oth, otp, ots, p12, pas, pab, pbm, pcd, pct, pcx, pdf, pef, pem, pfx, pgm, php, pict, pntg, potm, potx, ppam, ppm, pps, ppsm, ppsx, ppt, pptm, pptx, ppz, prf, psd, ptx, pub, qbw, qbx, qpw, raf, rtf, safe, sav, save, sda, sdc, sdd, sdf, sdp, skp, sql, sqlite, sqlite3, sqlitedb, stc, std, sti, stm, stw, sxc, sxg, sxi, sxm, sxw, tex, txt, tif, tiff, vcf, wallet, wb1, wb2, wb3, wcm, wdb, wpd, wps, xlr, xls, xlsb, xlsm, xlsx, xlam, xlc, xlk, xlm, xlt, reg, rspt, profile, djv, djvu, ms11, ott, pls, png, pst, xltm, xltx, xlw, xml, r00, 7zip, vhd, aes, ait, apk, arc, asc, asm, asset, awg, back, bkp, brd, bsa, bz2, csh, das, dat, dbf, db_journal, ddd, ddoc, des, design, erbsql, erf, ffd, fff, fhd, fla, flac, iif, iiq, indd, iwi, jnt, kwm, lbf, litesql, lzh, lzma, lzo, lzx, m2ts, m4a, mdf, mid, mny, mpa, mpe, mpeg, mpg, mpga, mrw, msg, mvb, myd, myi, ndf, nsh, nvram, nxl, nyf, obj, ogg, ogv, p7b, p7m, p7r, p7s, package, pages, pat, pdb, pdd, pfr, pnm, pot, psafe3, pspimage, pwm, qba, qbb, qbm, qbr, qby, qcow, qcow2, ram, rar, ras, rat, raw, rdb, rgb, rjs, rtx, rvt, rwl, rwz, scd, sch, scm, sd2, ser, shar, shw, sid, sit, sitx, skm, smf, snd, spl, srw, ssm, sst, stx, svg, svi, swf, tar, tbz, tbz2, tgz, tlz, txz, uop, uot, upk, ustar, vbox, vbs, vcd, vdi, vhdx, vmdk, vmsd, vmx, vmxf, vob, vor, wab, wad, wav, wax, wbmp, webm, webp, wks, wma, wp5, wri, wsc, wvx, xpm, xps, xsd, zip, zoo,
All affected files are renamed with the .kk extension. The samples also feature an exclusions list which disallows encryption into certain folders. This is done in order not to impact operating system. The folders include the following:
- Windows
- Program Files (x86)
- Program Files
- ProgramData
- WinNT
- System Volume Information
- \Desktop\Readme
- %Recycle.bin
Depending on the captured instance the engine may also delete all found Shadow volume copies. This effectively prevents data recovery without the use of a professional-grade recovery software.
SyncCrypt Ransomware Sample Ransomware Note
When the encryption process is complete a folder called README is created on the user’s desktop. It contains several files that are related to the infection:
- AMMOUNT.txt ‒ This file displays the ransomware sum request set by the hackers.
- key ‒ Contains the public encryption key used by the ransomware engine.
- readme.html ‒ This file displays the ransomware note presented to the victims.
- readme.png ‒ Shows the ransomware image.
The ransomware note is opened afterwards in the user’s default browser. It reads the following message:
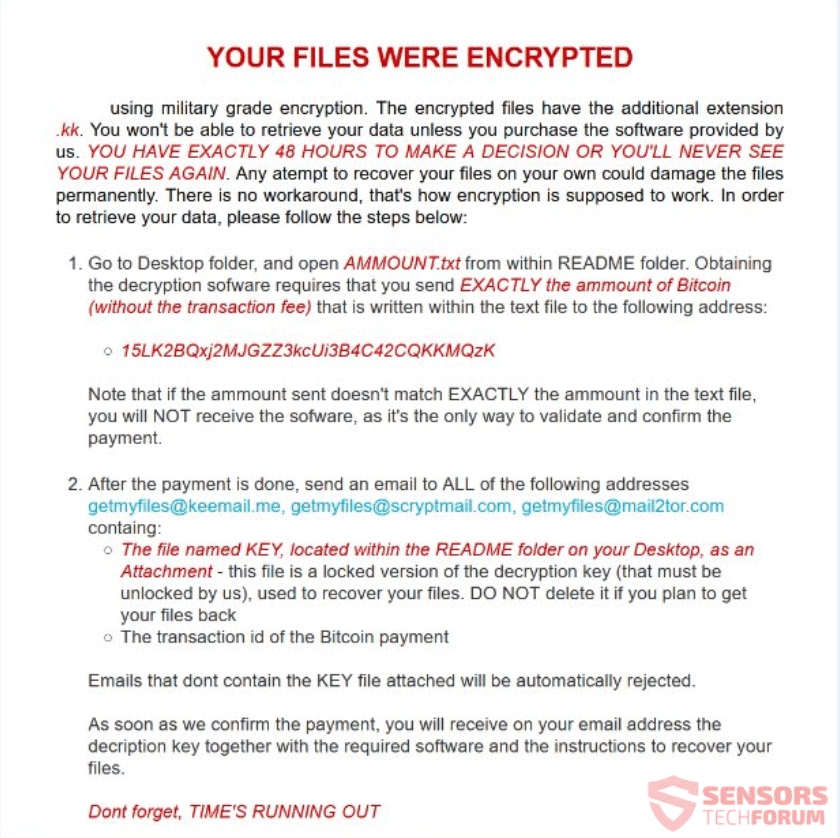
YOUR FILES WERE ENCRYPTED
using military grade encryption. The encrypted files have the additional extension .kk. You won’t be able to retrieve your data unless you purchase the software provided by us. YOU HAVE EXACTLY 48 HOURS TO MAKE A DECISION OR YOU’LL NEVER SEE YOUR FILES AGAIN. Any atempt to recover your files on your own could damage the files permanently. There is no workaround, that’s how encryption is supposed to work. In order to retrieve your data, please follow the steps below:
1. Go to Desktop folder, and open AMMOUNT.txt from within README folder. Obtaining the decryption sofware requires that you send EXACTLY the ammount of Bitcoin (without the transaction fee) that is written within the text file to the following address:
15LK2BQxj2MJGZZ3kcUi3B4C42CQKKMQzK
Note that if the ammount sent doesn’t match EXACTLY the ammount in the text file, you will NOT receive the sofware, as it’s the only way to validate and confirm the payment.
2. After the payment is done, send an email to ALL of the following addresses getmyfiles@keemail.me, getmyfiles@scryptmail.com, getmyfiles@mail2tor.com containg:
The file named KEY, located within the README folder on your Desktop, as an Attachment – this file is a locked version of the decryption key (that must be unlocked by us), used to recover your files. DO NOT delete it if you plan to get your files back
The transaction id of the Bitcoin payment
Emails that dont contain the KEY file attached will be automatically rejected.
As soon as we confirm the payment, you will receive on your email address the decription key together with the required software and the instructions to recover your files.
Dont forget, TIME’S RUNNING OUT
Depending on the obtained sample the virus may also choose to modify essential Windows registry settings. This may lead to stability or performance issues or prohibit the execution of certain applications. Advanced malware like the SyncCrypt ransomware may also disable anti-virus products.
We advise all users to use a quality anti-spyware tool to effectively scan for SyncCrypt infections and remove found instances with a few mouse clicks.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter


