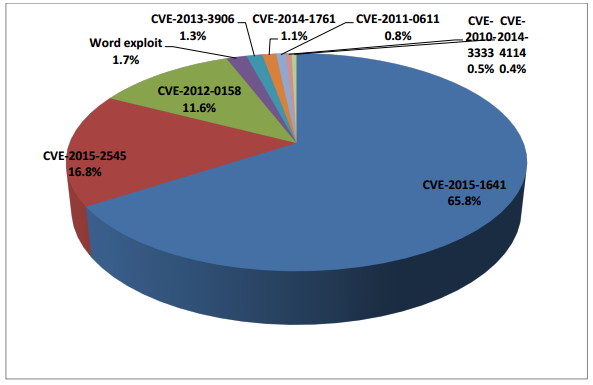
Microsoft Office vulnerabilities are cyber criminals’ favorites. Two of the more recent flaws – CVE-2015-1641 and CVE-2015-2545 – are quickly stepping up the malware game and seem to be replacing the all-time-favorite CVE-2012-0158. The latter leveraged a weak spot in ActiveX controls, and has been in the epicenter of multiple attacks puzzling security researchers as to why cyber criminals were using such an old exploit.
Microsoft Office vulnerabilities are cyber criminals’ favorites. Two of the more recent flaws – CVE-2015-1641 and CVE-2015-2545 – are quickly stepping up the malware game and seem to be replacing the all-time-favorite CVE-2012-0158. The latter leveraged a weak spot in ActiveX controls, and has been in the epicenter of multiple attacks puzzling security researchers as to why cyber criminals were using such an old exploit.
More about the Classic CVE-2012-0158
Official Description (from cve.mitre.org)
The (1) ListView, (2) ListView2, (3) TreeView, and (4) TreeView2 ActiveX controls in MSCOMCTL.OCX in the Common Controls in Microsoft Office 2003 SP3, 2007 SP2 and SP3, and 2010 Gold and SP1; Office 2003 Web Components SP3; SQL Server 2000 SP4, 2005 SP4, and 2008 SP2, SP3, and R2; BizTalk Server 2002 SP1; Commerce Server 2002 SP4, 2007 SP2, and 2009 Gold and R2; Visual FoxPro 8.0 SP1 and 9.0 SP2; and Visual Basic 6.0 Runtime allow remote attackers to execute arbitrary code via a crafted (a) web site, (b) Office document, or (c) .rtf file that triggers “system state” corruption, as exploited in the wild in April 2012, aka “MSCOMCTL.OCX RCE Vulnerability.”
Many infosec experts have paid tribute to the vulnerability, and Sophos recently released an intriguing report titled “Is it time for CVE-2012-0158 to retire?”. The report notes that this 4-year-old exploit has dominated the Office package attack scenario but is now being pushed aside by other vulnerabilities. This four-year-old classic exploit has been dethroned by two new flaws: CVE-2015-1641 and CVE-2015-2545.
It’s only logical that cyber criminals would turn to other, newer exploits, because users progressively patch their software leading to the decrease in chances of successful infections.
The first signs of CVE-2012-0158 slowly becoming obsolete were noticed this spring when the vulnerability started to evaporate from malware-carrying spam campaigns.
According to Sophos expert Gabor Szappanos the rise of CVE-2015-1641 and CVE-2015-2545 is directly associated with updates in several Office exploit kits. In other words, the exploit from 2012 is now removed and is replaced by the two 2015 flaws.
What Is a Microsoft Office Exploit Kit?
Malware operators have been leveraging Microsoft Office document vulnerabilities for many years. However, “document malware” as it’s sometimes called by cyber researchers has resurrected with vigor.
The attack vector mainly depends on whether it’s an average cyber crime group or an APT group targeting high-profile victims. In the first case, the exploited documents would be attached to email messages and sent out to large quantities of random potential victims. In the case of an APT attack, the victims’ number would be much smaller and would consist of selected targets.
Some of the Office exploit kits are known to be commercial, available for purchase at underground marketplaces. Others seem to be commercial, but haven’t appeared in any of the marketplaces yet. Finally, there are tools that are available only to a handful of groups.
More about CVE-2015-2545
This vulnerability has been observed in attacks carried out by cyber-espionage APT groups. It allows malicious actors to embed malicious EPS payloads as images inside Office files. CVE-2015-2545 affects Office 007 SP3, 2010 SP2, 2013 SP1, and 2013 RT SP1. Unfortunately, the flaw is gaining popularity not only among APT criminals but is also leveraged by cyber crime gangs.
More about CVE-2015-1641
This one has been noticed in small-scale high-profile operations, more specifically in APT attacks. Sophos, however, says that CVE-2015-1641 has been used in multiple spam campaigns. It’s easy to spot the vulnerability because it can only be activated through RTF documents. CVE-2015-1641 affects Microsoft Word 2007 SP3, Office 2010 SP2, Word 2010 SP2, Word 2013 SP1, Word 2013 RT SP1, Word for Mac 2011, Office Compatibility Pack SP3, Word Automation Services on SharePoint Server 2010 SP2 and 2013 SP1, and Office Web Apps Server 2010 SP2 and 2013 SP1.

How to Stay Protected against Document Malware
First and foremost – patch your software! Applying all available security patches should be your top priority. However, updates may be important but they are just a small piece from the puzzle. Since spam is a major culprit for both small- and big-scale malware operations, you shouldn’t neglect precautionary tips like the ones below…
Anti-Spam Protection Tips
- Employ anti-spam software, spam filters, aimed at examining incoming email. Such software serves to isolate spam from regular emails. Spam filters are designed to identify and detect spam, and prevent it from ever reaching your inbox. Make sure to add a spam filter to your email. Gmail users can refer to Google’s support page.
- Don’t reply to dubious email messages and never interact with their content. Even an ‘unsubscribe’ link within the message body can turn out to be suspicious. If you respond to such a message, you will just send a confirmation of your own email address to cyber crooks.
- Create a secondary email address to use whenever you need to register for a web service or sign up for something. Giving away your true email address on random websites is never a good idea.
- Your email name should be tough to crack. Research indicates that email addresses with numbers, letters and underscores are tougher to crack and generally get less spam emails.
- View your emails in plain text, and there’s a good reason why. Spam that is written in HTML may have code designed to redirect you to unwanted pages (e.g. advertising). Also, images within the email body can be used to ‘phone home’ spammers because they can use them to locate active emails for future spam campaigns. Thus, viewing emails in plain text appears to be the better option. To do so, navigate to your email’s main menu, go to Preferences and select the option to read emails in plain text.
- Avoid posting your email address or a link to it on web pages. Spam bots and web spiders can locate email addresses. Thus, if you need to leave your email address, do it as it follows: NAME [at] MAIL [dot] com or something similar. You can also look for a contact form on the website – filling out that form shouldn’t reveal your email address or your identity.
And finally, keep your system protected at all times!
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter