There is a new version of the TeslaCrypt ransomware. It is dubbed TeslaCrypt 3.0. It is known to encrypt files with the .micro extension or with .ttt and .xxx extensions. The .micro extension variant still uses an RSA encryption algorithm.

Threat Summary
| Name | TeslaCrypt 3.0 |
| Type | Ransomware |
| Short Description | The ransomware searches for files with various extensions and encrypts them. Then, it asks for money to decrypt the files, and describes where to send it in a ransom note. |
| Symptoms | Files get encrypted with a .micro extension. A ransom note appears on the desktop. |
| Distribution Method | Malicious Sites, Spam emails with attachments |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
| User Experience | Join our forum to discuss TeslaCrypt with .micro Extension. |
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |

TeslaCrypt .micro Extension Ransomware – Distribution
The TeslaCrypt 3.0 version may be spread by Trojan horses, just like its previous version was spread through the Miuref.B Trojan. That normally happens when you visit suspicious sites and click on links with malicious code without knowing.
An effective distribution method for the ransomware remains spam emails with malicious file attachments. The attachments can be some archives or executable files. There are reports that some of the malicious files may infect computers by running compromised macro commands of Microsoft Office or Adobe programs.

The .micro Extension Ransomware – Details
When activated on your computer, the ransomware creates a randomly named executable file on the User profile in the following location:
→Appdata/Roaming/[random name].exe
After this file is executed, it creates an entry in the Windows Registry. The name of the entry is “meryHmas” and its location is:
→HKCU\Software\Microsoft\Windows\CurrentVersion\Run\meryHmas
That enables these files of the ransomware to be read and run with each start of the Windows operating system.
The .micro extension variant may also create more entries in the Windows Registry, as follows:
→HKCU\Software\[random name] HKCU\Software\xxxsys
Then TeslaCrypt 3.0 begins searching files to encrypt and lock them with the .micro extension. The known file formats it scans for are listed right down here, but it may not be a full list.
→sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt
After successful encryption, the ransomware creates other files on your desktop and links to other locations that contain the ransom note with the payment instructions. The files are named as:
→Howto_Restore_FILES.BMP
Howto_Restore_FILES.HTM
Howto_Restore_FILES.TXT
These instructions are nearly identical to another nasty ransomware, called CryptoWall 3.0. Researchers think that this message has been used to simplify and outsource the ransom payment using CryptoWall’s methods or to hide the real identity of the malware.
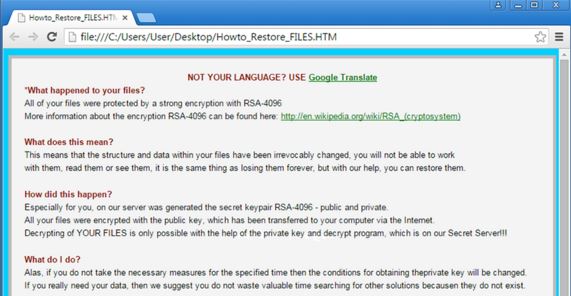
This ransom message has instructions on how to use the Tor network to reach the cyber-criminals via an anonymous connection and make the ransom payment. It is strongly advised NOT to pay the ransom money demanded by the TeslaCrypt 3.0 creators since it is no guarantee you will get a decryption key to restore your files. Also, if you pay the ransom, you are funding the cyber-criminals to further sophisticate their work, and they can use the money for many other ill deeds.

The .micro Extension Ransomware – Removal
To fully remove TeslaCrypt 3.0, first have to cut off the ransomware by stopping your internet connection. Then, back up your system files. Afterwards, carefully follow the instructions provided below. If you still see the ransomware being active, you may need to install an advanced anti-malware tool. Such software will keep your system secure in the future.


Hi,
did someone know what about micro extensions.
I lost everthing