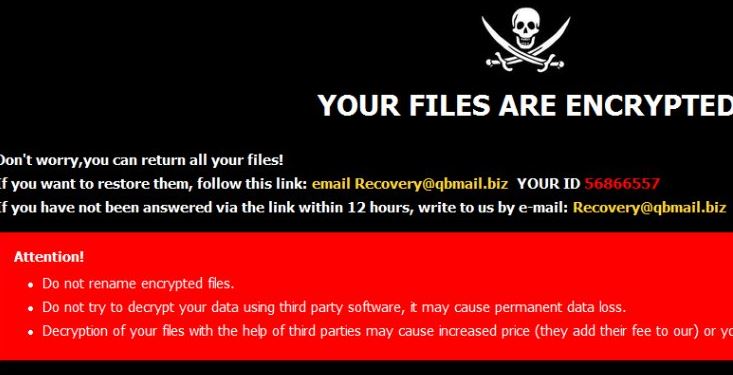
.Try2Cry Virus File (Try2Cry Ransomware) – Remove It
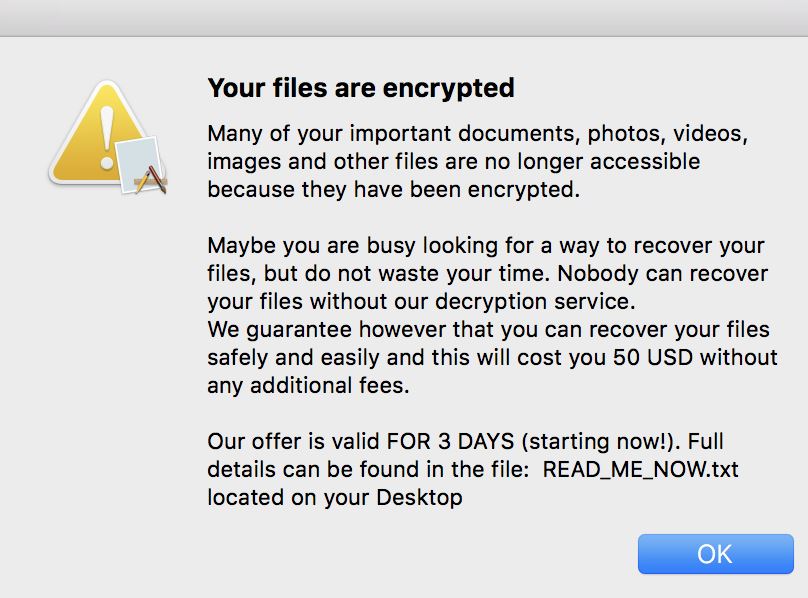
.Try2Cry file extension is placed on all of your files? .Try2Cry Virus File is also known as Try2Cry ransomware which locks files on a computer and may demand money to be paid at some point for unlocking them. Try2Cry Ransomware…