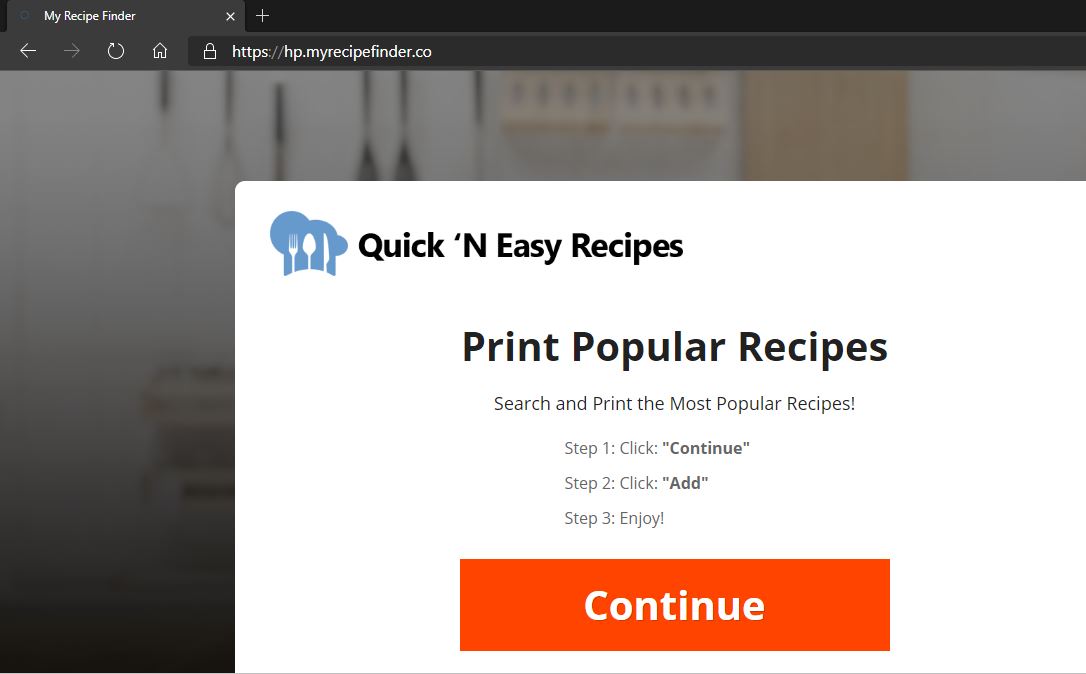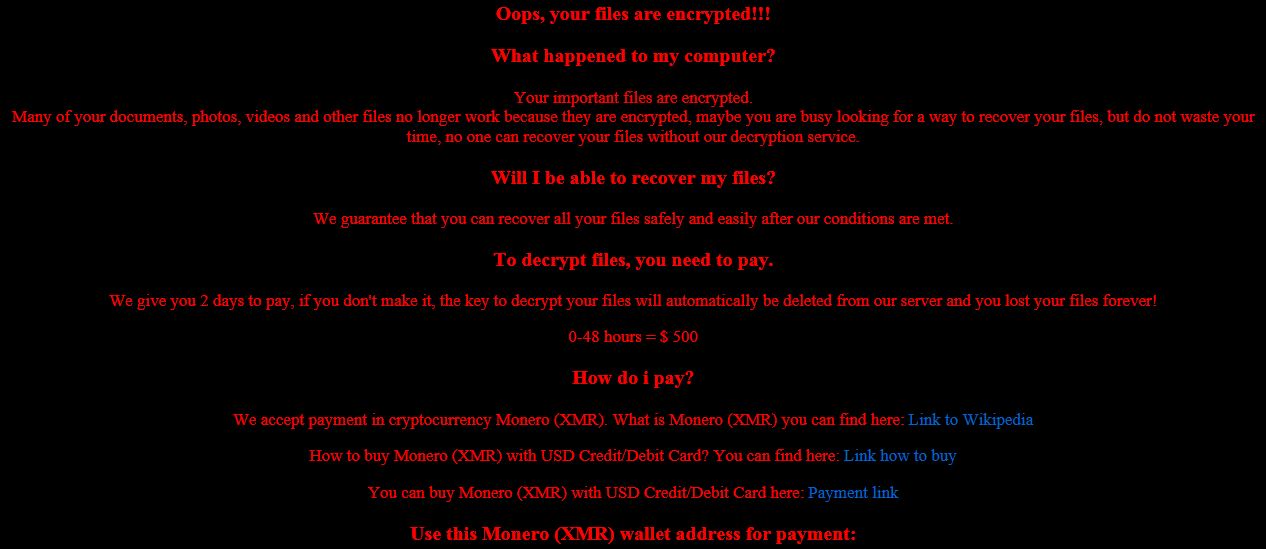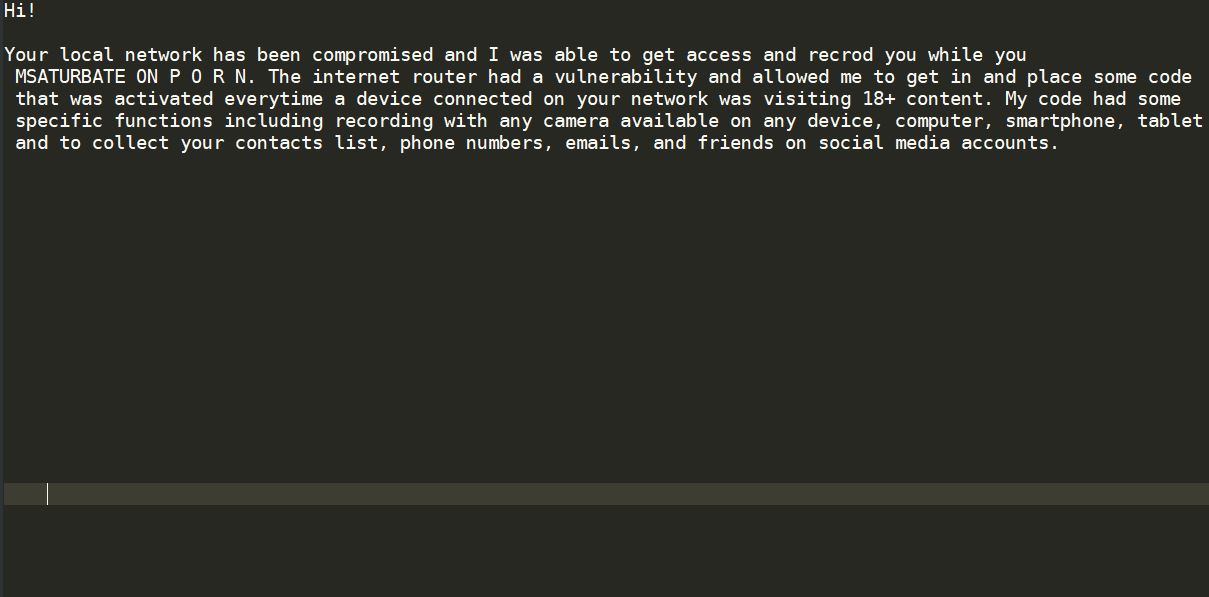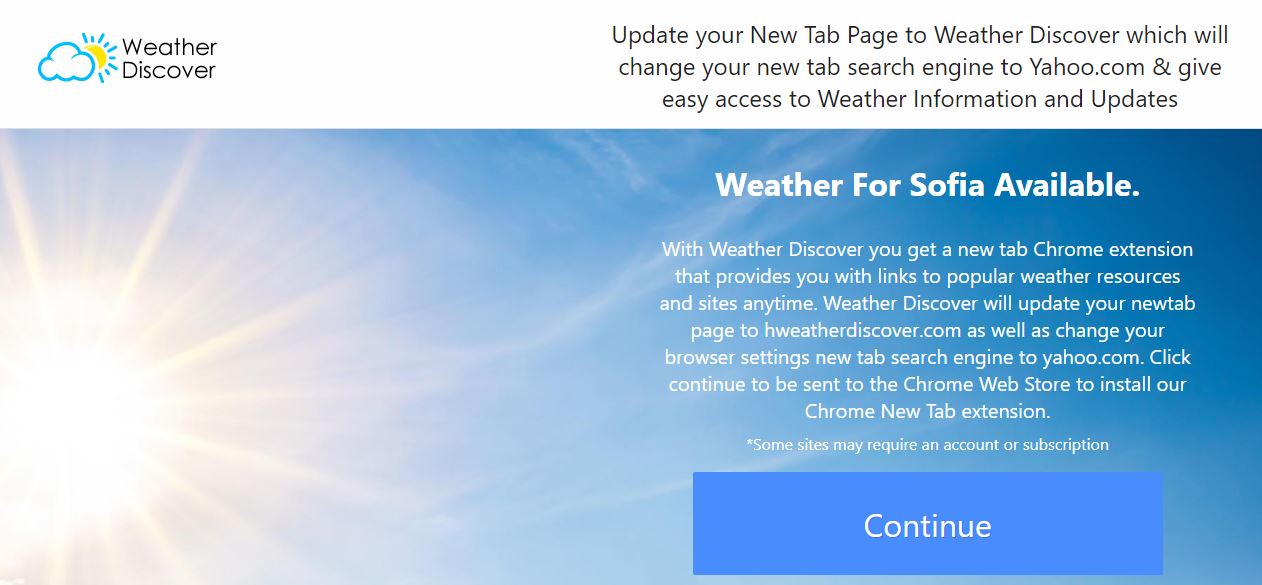
Remove Weather Discover Redirect
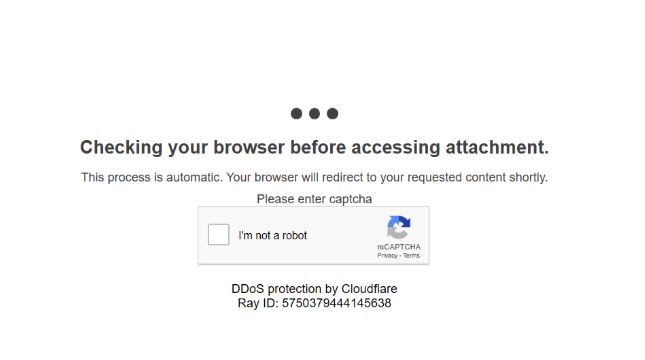
Weather Discover redirect is showing up in your browser programs? Weather Discover is a suspicious domain because of the page redirects that can happen in your browser programs. Weather Discover can push various full page advertisements and redirects. A single…