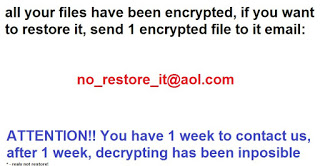
The L0rdix Malware Hacking Tool Released on the Dark Web
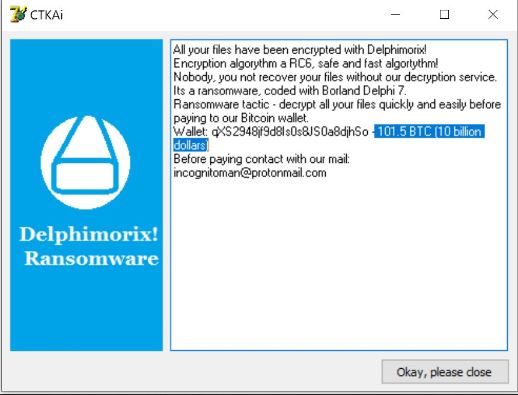
The L0rdix malware is a newly detected hacking tool that is being offered on the hacker underground markets allowing prospective buyers to use it in attack campaigns against Windows computers. It allows individual hackers and groups to use it in…