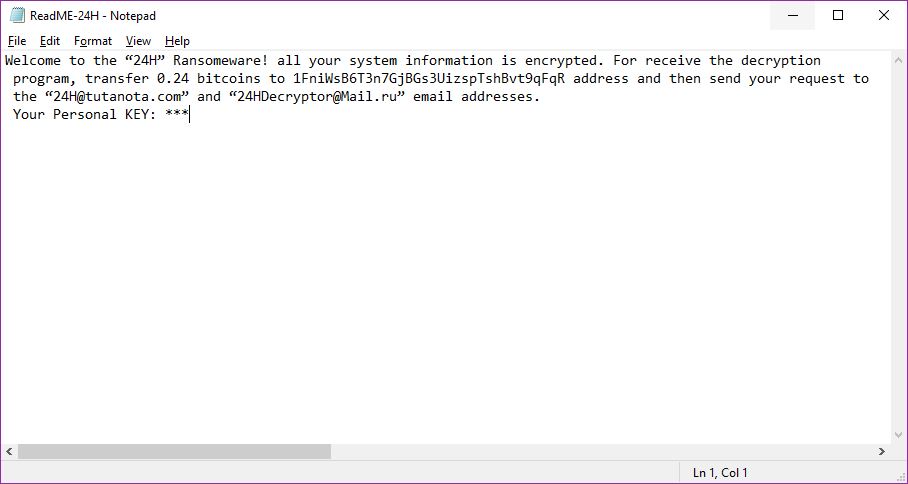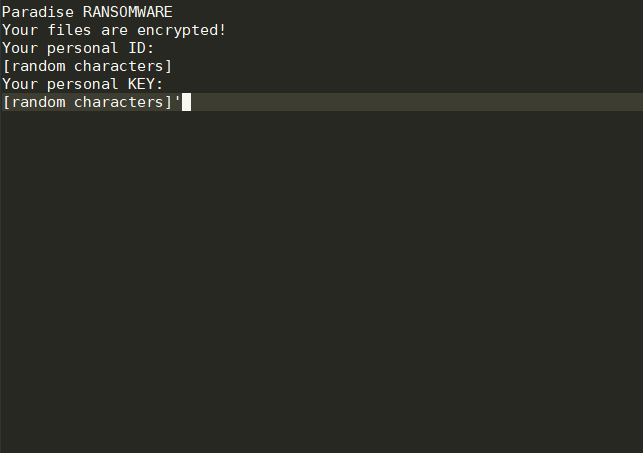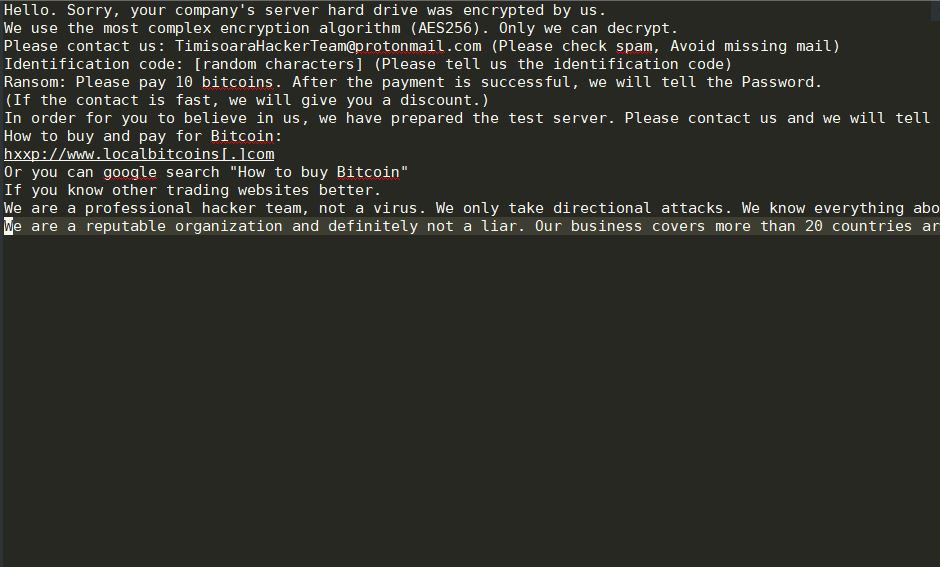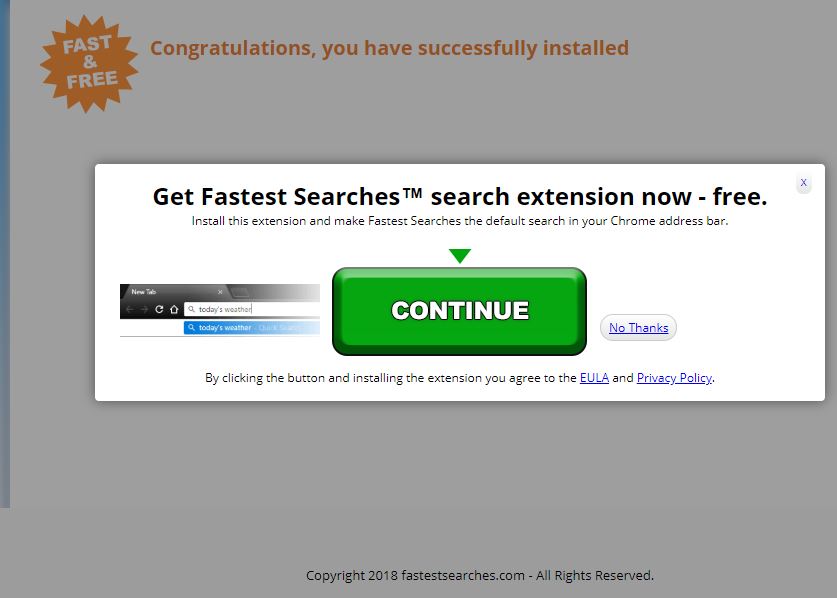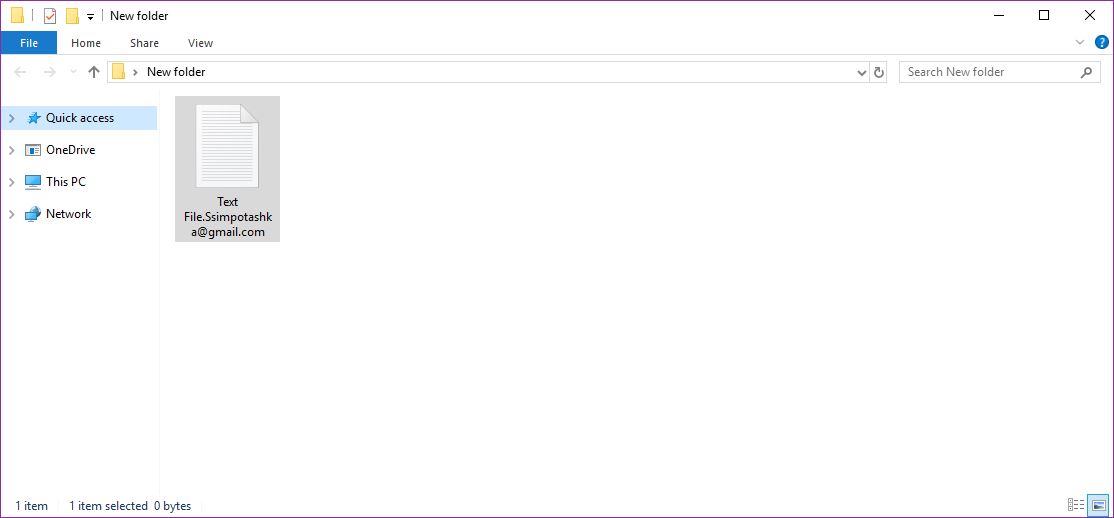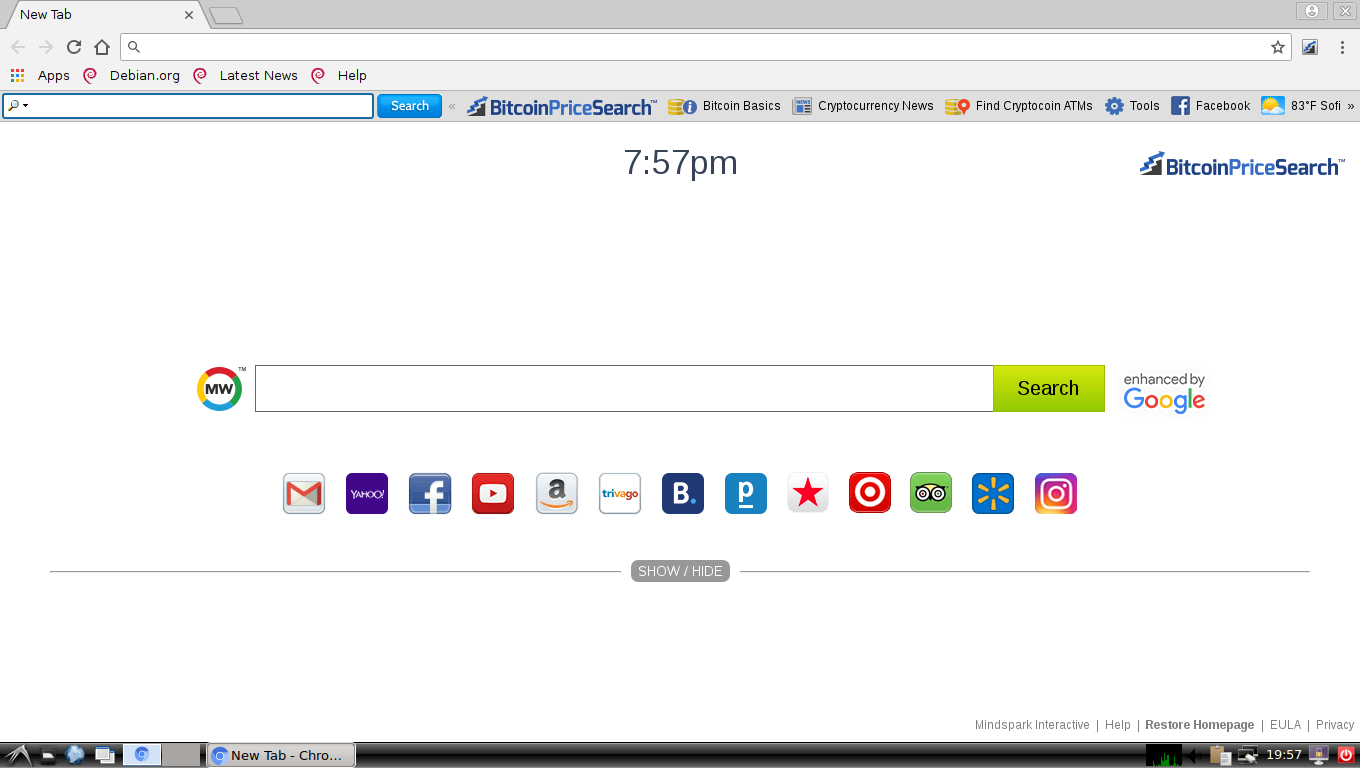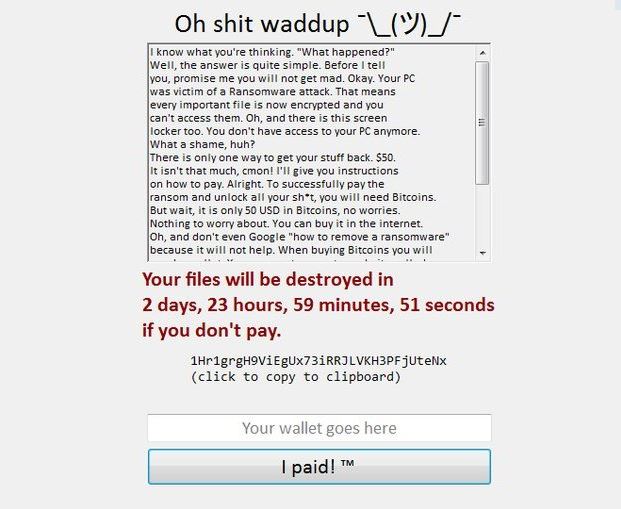
Shrug Virus Remove – How to Restore .SHRUG Files
Shrug virus is a newly discovered test version of a new threat. The security analysis reveals that it does not contain snippets from any of the famous malware families. It is possible that future versions of it are going to…