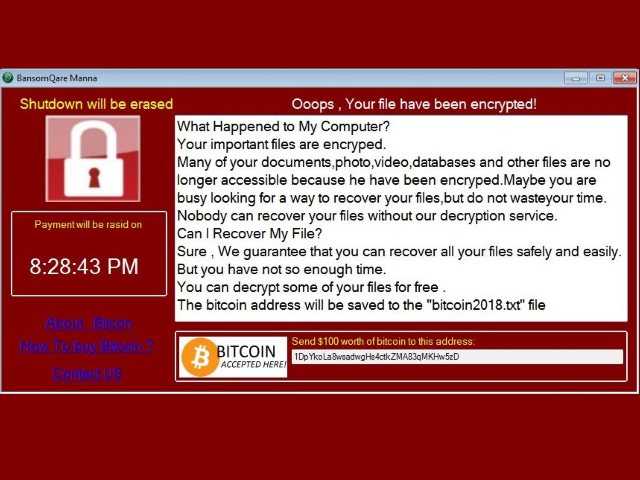
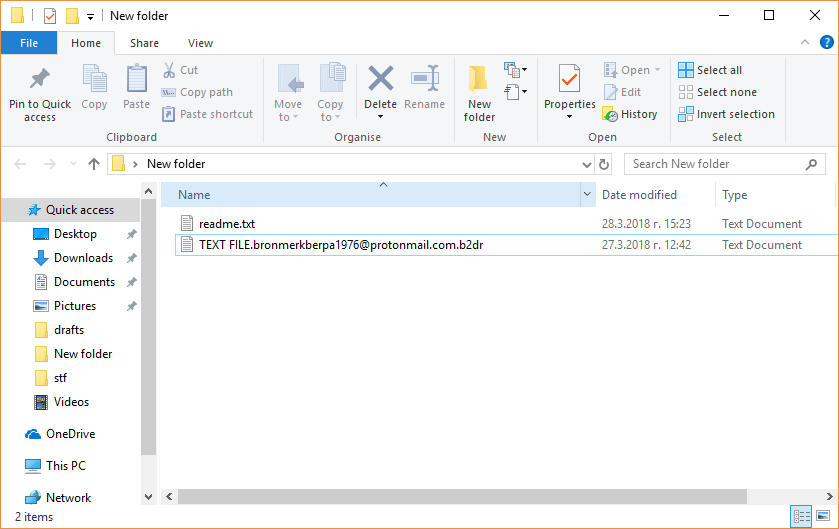
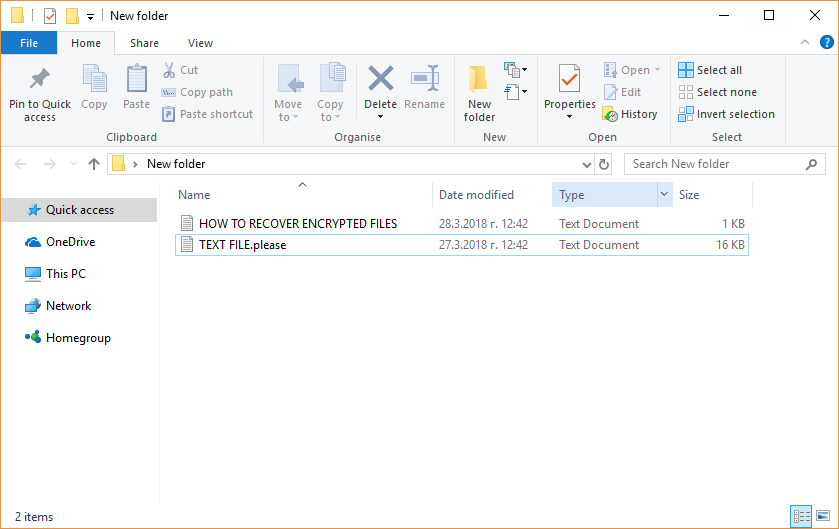
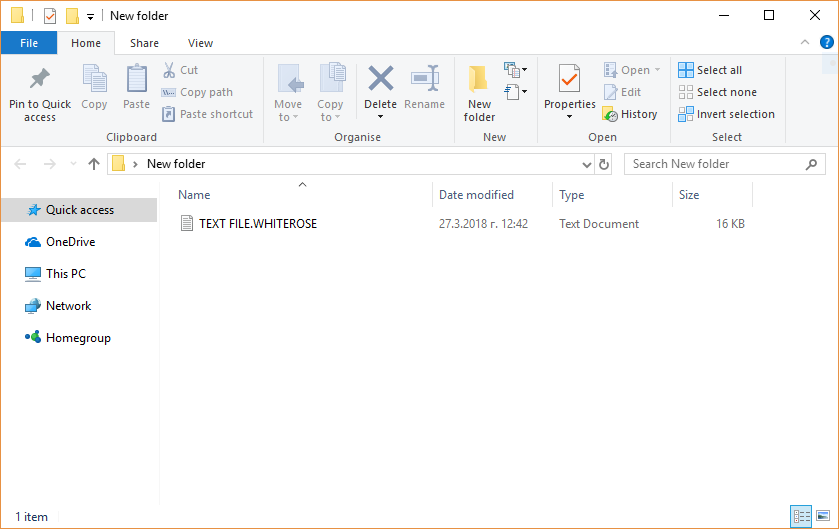
FunSocialTabSearch Redirect Removal Instructions
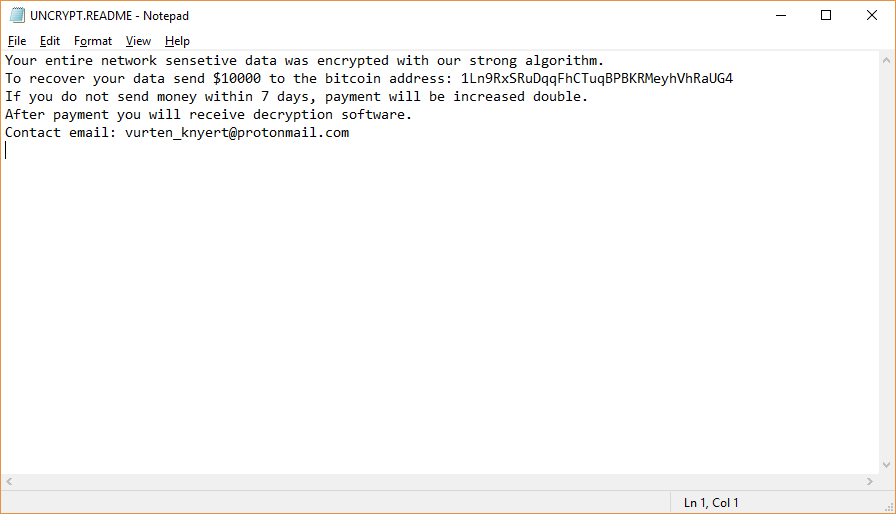
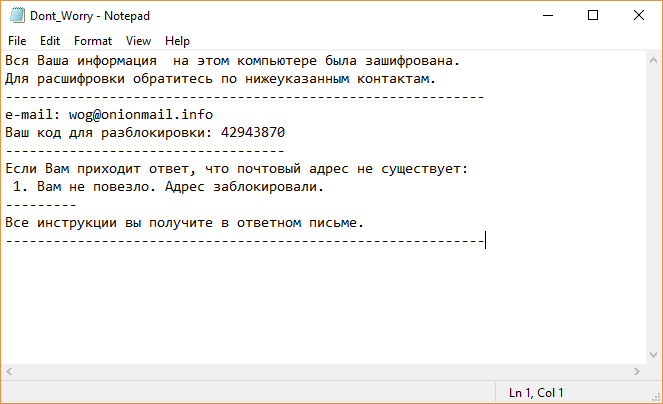
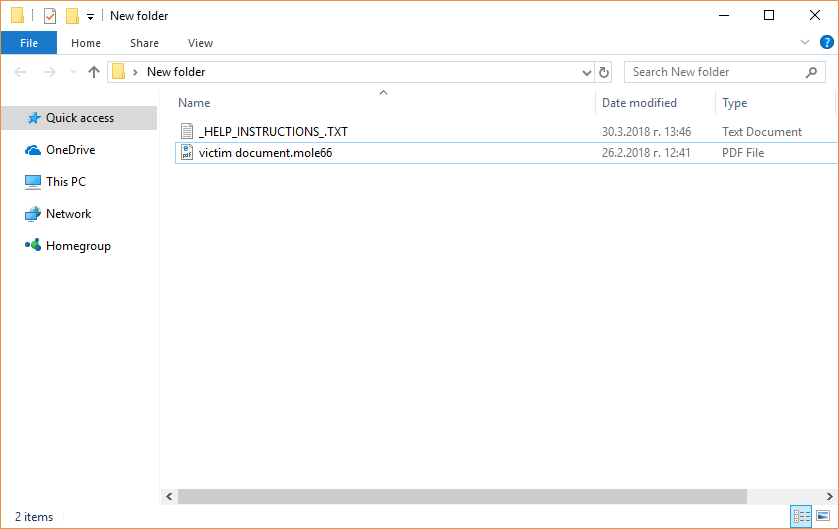
The article will help you to remove FunSocialTabSearch fully. Follow the browser hijacker removal instructions given at the end of the article. The FunSocialTabSearch is made by IMALI – N.I. MEDIA LTD., a company well-known for creating whole networks of…