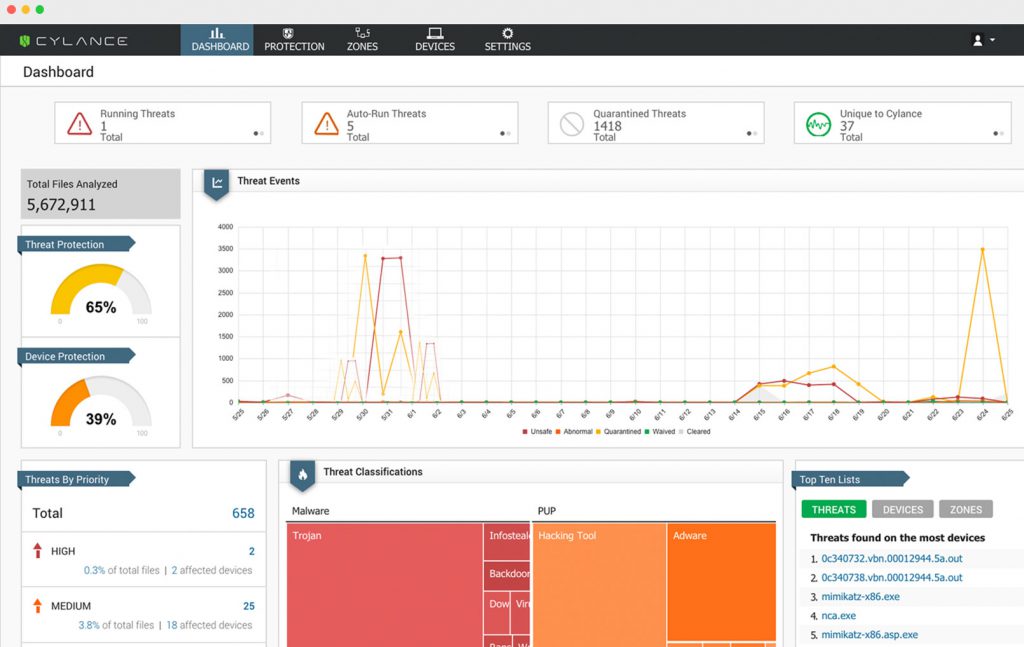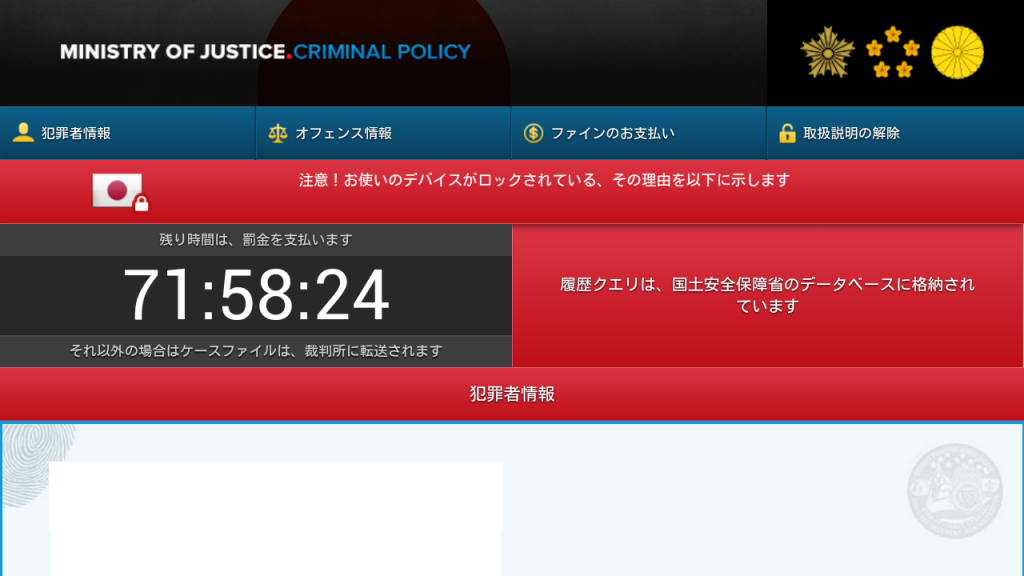
FLocker Ransomware Outsmarts and Locks Smart TVs
Not only your personal computer and smartphone are prone to ransomware attacks. TrendMicro researchers just unveiled that your Android TV is also exposed to the risk of being locked and becoming unusable until a ransom is paid. The threat, dubbed…