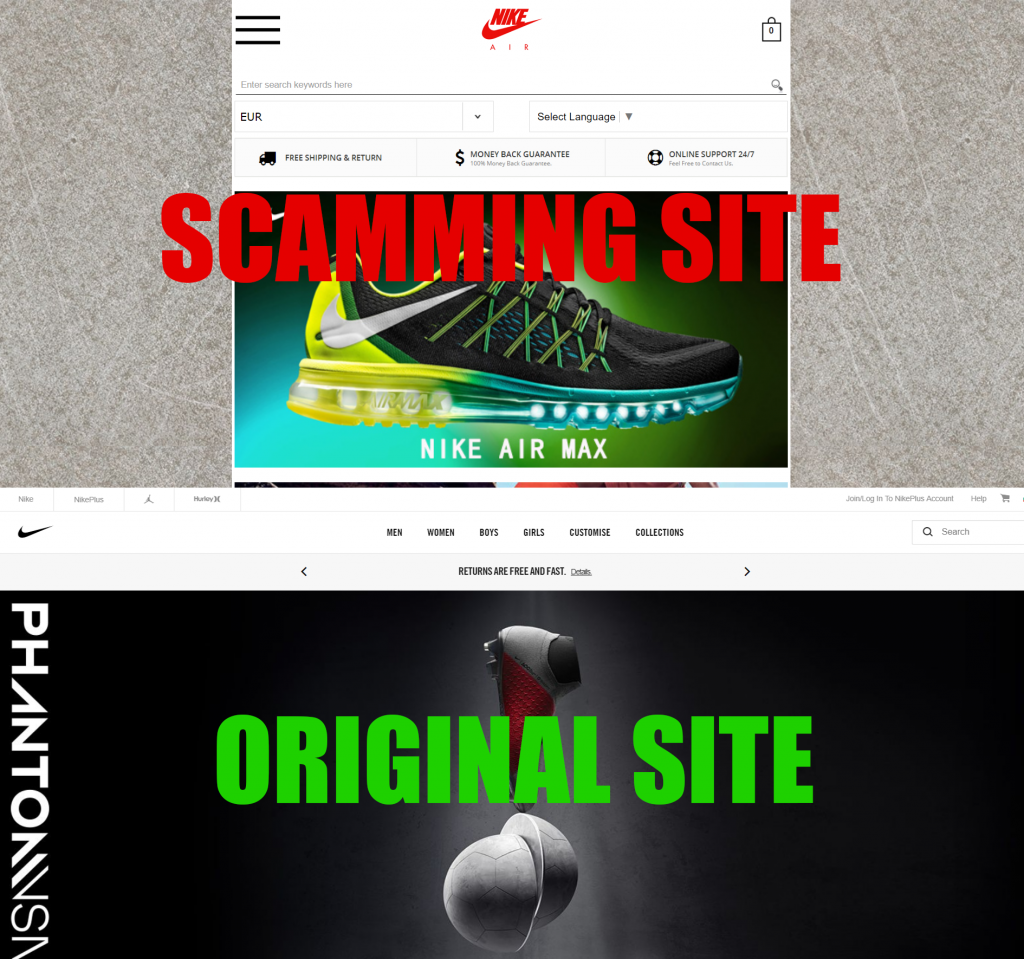
Facebook Nike Shoes Scam of 2018 Shows History Repeats Itself
A new scam wave has started to hit the world and this time it is a big one, advertising users to visit phishing web pages that aim to steal their sensitive information. We at Sensors Tech Forum have covered malware…